Developers are increasingly using Kubernetes’ open-source platform to manage containerized workloads and services. Kubernetes containers became popular because it was impossible to define a resource boundary for multiple applications in a traditional CPU environment, and resource misuse created an inefficient environment.
Kubernetes solves the problem by allowing applications to work as isolated containers inside a single operating system. These lightweight containers have their own filesystem, CPU share, memory, storage space, etc. You can move the container across clouds and OS distributions, which makes them a powerful resource. Currently, there are three different Kubernetes certifications that you can take to develop your knowledge and skills even further. Keep reading to see which one is right for you.
Why should I get Kubernetes certifications?
Kubernetes certifications create new opportunities for career growth. A recent survey by Cloud Native Computing Foundation suggests that Kubernetes is the go-to choice for more than 78% of organizations, and nearly 84% of companies run containers in production. Such trends are also visible in the 2021 Red Hat OpenShift report, which states that more than half of IT companies intend to increase the use of containers in the future.
Many organizations shortlist employment candidates who hold the Kubernetes certification, so getting certified helps you stand out and often means less competition when you’re looking for a new job. Companies are also willing to pay more to K8s engineers because hiring managers realize that very few individuals are skilled in this emerging field.
Kubernetes certifications paths
The Linux Foundation manages Kubernetes certification. There are currently five certifications. These are:
- Certified Kubernetes Application Developer (CKAD)
- Certified Kubernetes Administrator (CKA)
- Certified Kubernetes Security Specialist (CKS)
- Kubernetes and Cloud Native Security Associate (KCSA)
- Kubernetes and Cloud Native Associate (KCNA)
Developer path: As the name suggests, a developer builds and manages Kubernetes applications. You will design, build, and configure apps. Developers can define the resources that applications will use and troubleshoot relevant issues.
Administrative path: The administrative path focuses on managing the Kubernetes environment. Administrators may install, manage, and configure production-grade Kubernetes clusters. They’re the people behind the Kubernetes operations.
The administrative path also leads to certification as a Kubernetes Security Specialist. The CKS certification ensures best practices and covers the necessary skills to secure container-based apps and platforms from threats. It is important to note that you must hold a Certified Kubernetes Administrator license before pursuing a Kubernetes Security Specialist license.
Foundational cloud-native path: This path is designed for beginners and professionals seeking to understand cloud-native ecosystems. The KCNA certification validates knowledge of Kubernetes fundamentals, while the KCSA certification focuses on cloud-native security principles, making them excellent starting points for a cloud-native career.
Certified Kubernetes Application Developer (CKAD)
The Certified Kubernetes Application Developer exam is developed by Linux Foundation and the Cloud Native Computing Foundation. It’s a two-hour online exam that tests the candidate’s ability to perform the responsibilities of a Kubernetes developer. The two-hour exam is the first step for many new individuals.
Prerequisites
There is no prerequisite to take CKAD; however, prior experience in an IT field will help candidates easily grasp the concepts. The exam will not test candidates on material related to container runtimes and microservice architecture, but it assumes that you should know these contents.
To pass the exam, you should be comfortable with the following:
- An OCI-Compliant container Runtime.
- Concepts and architectures related to Cloud Native application.
- Knowledge of programming languages such as Java, Python, and Node.js.
Content
The course content consists of seven domains and competencies. These include core concepts, configuration, multi-container pods, observability, pod design, service and networking, and state persistence.
The exam
For the CKAD exam, candidates must score 66% or above to become certified. The exam consists of performance-based tasks that candidates must solve in a command line. Each test is proctored online using audio, video, and screen-sharing feeds, allowing the examiner to view candidates’ desktops.
It will cost you $300 to take the Certified Kubernetes Application Developer exam, but you may be eligible for a bundled discount when opting for training and the exam. The certification is valid for three years.
Certified Kubernetes Administrator (CKA)
Certified Kubernetes Administrator certificate ensures you can install, configure, and manage production-grade Kubernetes clusters. After passing the exam, you also become eligible to take the CKS exam.
Prerequisites
Although this certificate does not have prerequisites, candidates should preferably have prior experience in the IT field. The exam is designed for Kubernetes administrators, IT professionals, and cloud administrators.
To pass the exam, candidates should be comfortable in:
- Understanding the key concepts of Kubernetes networking, storage, security, and maintenance.
- Establishing basic use cases for end-users.
- Knowledge of application lifecycle, troubleshooting, and API object primitives.
Content
The exam question tests candidates’ knowledge of five key subjects. Nearly 40% of the content covers storage and troubleshooting. Another 15% is dedicated to workloads and scheduling. Cluster architecture, installation, and configuration comprise almost 25% of the exam’s questions. The remaining 20% tests your knowledge of services and networking.
The exam
You must score at least 66% to pass the CKA exam. The exam is proctored online, and you can review documents installed by the distribution. Candidates can also review the exam content instructions presented in the command line terminal. The Procter will allow you to open one additional tab on the Chrome browser to access particular online assets.
The cost of the exam is $300, which includes a free retake. The certification is valid for three years. You will receive the result within 36 hours after the completion of the exam.
Certified Kubernetes Security Specialist (CKS)
The two-hour exam for Certified Kubernetes Security Specialist evaluates candidates based on the best practices required to secure the Kubernetes environment. To pass the exam, candidates must demonstrate knowledge of securing container-based applications and the Kubernetes platform during build, deployment, and runtime.
Prerequisites
To sit in the exam, you need to pass the Certified Kubernetes Administrator exam first. You may purchase the CKS certification before the actual exam, but you can only take the exam after completing the prerequisite.
Here are some of the important points to grasp before the exam:
- Understand a broad range of best practices required to secure a Kubernetes environment.
- Basic knowledge of dealing with Kubernetes and cloud security issues in a real-world environment.
- Ability to set up clusters, run security audits, detect threats, and do static analysis.
Content
The exam is divided into six modules. The cluster setup comprises 10% of the overall content, while cluster hardening and system hardening make up 30%. The remaining 60% evaluates supply chain security, microservice vulnerability, and managing runtime security.
The exam
The exam, which consists of 15 to 20 performance-based tasks, costs $300 to register for. During the exam, you can access Kubernetes documentation, tools, and app armor. Unlike the two other certifications, CKS certification is valid for two years.
Certified Kubernetes and Cloud Native Security Associate (KCSA)
The Kubernetes and Cloud Native Security Associate (KCSA) exam is designed by the Linux Foundation to validate foundational cloud-native security skills. It serves as a starting point for those new to Kubernetes security or cloud-native technologies. The exam evaluates a candidate’s understanding of Kubernetes security concepts, cloud-native infrastructure, and industry best practices.
Prerequisites
There are no formal prerequisites for the KCSA exam. However, having a basic understanding of Kubernetes and IT security concepts can be helpful.
To pass the exam, candidates should be comfortable in:
- Understanding Kubernetes cluster components and their security features.
- Applying security fundamentals for cloud-native environments.
- Managing container security using best practices.
Content
The exam is divided into six modules. The overview of cloud-native security accounts for 14% of the content, while Kubernetes cluster component security and Kubernetes security fundamentals each comprise 22%. The Kubernetes threat model and platform security cover 16% each, and compliance and security frameworks comprise the remaining 10%.
The exam
The KCSA exam costs $250 and is an online, proctored, multiple-choice test. Candidates have 12 months from the purchase date to schedule and complete the exam. Two exam attempts are included. The certification is valid for three years.
Certified Kubernetes and Cloud Native Associate (KCNA)
The Kubernetes and Cloud Native Associate (KCNA) exam is designed by the Linux Foundation to validate foundational knowledge of Kubernetes and the wider cloud-native ecosystem. It is an entry-level certification for those new to cloud-native technologies, providing a strong starting point for IT professionals and developers.
Prerequisites
The KCNA exam has no prerequisites, making it accessible to beginners and IT professionals who want to develop cloud-native skills.
To pass the exam, candidates should be comfortable in:
- Understanding Kubernetes fundamentals and container orchestration.
- Recognizing cloud-native architecture principles.
- Applying cloud-native observability and application delivery practices.
Content
The exam is divided into five modules. Kubernetes fundamentals account for 46% of the content, container orchestration makes up 22%, and cloud-native architecture covers 16%. Cloud-native observability and application delivery account for 8% of the total.
The exam
The KCNA exam costs $250 and is an online, proctored, multiple-choice test. Candidates have 12 months from the purchase date to schedule and complete the exam, with one free retake included. Like the CKS certification, the KCNA certification is only valid for two years.
Kubernetes certifications comparison table
| Criteria | CKAD | CKA | CKS | KCSA | KCNA |
| Prerequisites | None, but IT experience recommended | None, but IT experience recommended | Must pass CKA first | None | None |
| Exam Format | Performance-based tasks | Performance-based tasks | Performance-based tasks | Multiple-choice | Multiple-choice |
| Exam Length | 2 hours | 2 hours | 2 hours | Online, proctored | 90 minutes |
| Exam Cost | $300 (with possible bundled discount) | $300 (includes free retake) | $300 | $250 (two attempts included) | $250 (one free retake included) |
| Certification Validity | 3 years | 3 years | 2 years | 3 years | 2 years |
Certified Kubernetes Administrator (CKA) vs. Certified Kubernetes Application Developer (CKAD)
Many people need clarification about the two certifications. Because of their relevancy and similarities, they can’t decide which certification to pursue. Here’s our take on the subject.
If you have basic app development experience or are new to Kubernetes, starting as a Certified Kubernetes Application Developer may be better. The certification mainly tests your cloud-native developer and DevOps skills. In contrast, the Certified Kubernetes Administrator exam requires a thorough knowledge of the entire Kubernetes infrastructure and Linux system.
While both exams test various similar features, the Certified Kubernetes Administrator takes it up a notch by evaluating your problem-solving skills in installing, troubleshooting, maintaining, and upgrading. It also means that getting CKAD certification may be a better approach for anyone relatively new to the Kubernetes environment.
Additional cloud native certifications
As the cloud-native ecosystem continues to expand, several certifications complement Kubernetes expertise by focusing on specific cloud-native technologies. These certifications enable IT professionals to deepen their knowledge in specialized areas such as monitoring, service mesh, and cloud-native application delivery.
Prometheus Certified Associate (PCA)
The Prometheus Certified Associate (PCA) certification validates a candidate’s knowledge of observability and monitoring using Prometheus. This exam covers Prometheus fundamentals, querying with PromQL, and setting up alerts and dashboards.
Istio Certified Associate (ICA)
The Istio Certified Associate (ICA) certification focuses on the Istio service mesh, emphasizing service discovery, traffic management, and microservice security. It is ideal for developers and operators of microservice-based applications.
Other cloud native certifications
- Helm Certified Associate: Focuses on using Helm to simplify Kubernetes application deployment and management. Candidates learn about creating, managing, and maintaining Helm charts and handling Helm releases and repositories.
- Fluent Certified Associate: Emphasizes centralized logging, data processing, and log aggregation in cloud-native environments. Candidates learn about configuring Fluentd for log collection, filtering, and forwarding in distributed systems.
- Envoy Certified Associate: Validates expertise in using Envoy proxy for securing, managing, and routing microservice traffic. Candidates learn about configuring Envoy for service discovery, load balancing, traffic routing, and applying security policies such as TLS encryption and access control.
What are the overall benefits of Kubernetes certification?
Containers and the cloud are rapidly changing the IT landscape. Besides a potential rise in pay, new career opportunities, and respect from your peers, Kubernetes certifications allow everyone to integrate the newly acquired knowledge into their existing environment.
The certification allows developers to create container-based management systems. Kubernetes’s flexible environment enables developers to use a variety of programming languages and frameworks to strengthen the existing cloud infrastructure.
Operations can use Kubernetes to bridge the gap between developers and users who are not adept at learning all the scripts and tools. The team can use the technology and expertise gained from certifications to package an application with its required infrastructure.
Security professionals can use Kubernetes and containers to increase the development speed while keeping everything secure. The end-to-end toolchain supporting the existing cloud-native infrastructure creates an attack surface, which is often challenging to defend. Kubernetes can help solve this problem.
How to prepare for Kubernetes exams
A few essential tips will come in handy when preparing for Kubernetes exams:
- You can review the exam guide on the Linux Foundation’s official website. It will help you get the latest updates in each domain.
- Don’t ignore the significance of hands-on training even if you have prior experience and know-how of Kubernetes. Competent training instructors can also answer unresolved queries.
- Master the Linux command line and practice problems using a text editor. Learn systems services because the exam environment relies on them.
- Get used to the exam console as it is different from stand-alone platforms. Shortcuts that work on other platforms may not work here.
- You should also learn how to set up and administer a cluster from scratch. Various online resources can help you do it.
- Maintain your speed by memorizing where to find specific topics in the documentation. Since you only need to solve two-thirds of the questions, skip time-consuming questions and solve them if you have the time.
Taking the next step
Achieving Kubernetes certifications and learning Kubernetes skills can transform your IT career by enhancing your technical expertise, boosting your resume, and opening up exciting job opportunities. Whether you’re just starting with Kubernetes or seeking advanced cloud-native security skills, these certifications validate your capabilities and set you apart in the tech industry.
Take the next step in managing your Kubernetes environment with LogicMonitor’s container monitoring solution. Our scalable, dynamic monitoring platform provides real-time visibility into your Kubernetes and Docker applications, automatically adapting to changes in containerized resources. Identify and resolve performance issues quickly while focusing on innovation.
Amazon Elastic Kubernetes Service (Amazon EKS) is a managed Kubernetes service that simplifies deploying, scaling, and running containerized applications on AWS and on-premises. EKS automates Kubernetes control plane management, ensuring high availability, security, and seamless integration with AWS services like IAM, VPC, and ALB.
This managed AWS Kubernetes service scales, manages, and deploys containerized applications. Through EKS, you can run Kubernetes without installing or operating a control plane or worker nodes — significantly simplifying Kubernetes deployment on AWS.
So what does it all mean? What is the relationship between AWS and Kubernetes, what are the benefits of using Kubernetes with AWS, and what are the next steps when implementing AWS EKS? Let’s jump in.
Importance of container orchestration
Container orchestration automates container movement, supervision, expansion, and networking. It can be used in every scenario where containers are used and will help you position the same applications across different environments. Today, Kubernetes remains the most popular container orchestration platform offered by Amazon Web Services (AWS), Google Cloud Platform, IBM Cloud, and Microsoft Azure.
As companies rapidly expand, the number of containerized applications they use also increases. However, managing them in larger quantities can become challenging. You’ll benefit from this process if your organization manages hundreds or thousands of containers. Data shows approximately 70% of developers use container orchestration tools.
Due to its automation properties, container orchestration greatly benefits organizations. It reduces manhours, the number of employees needed, and the financial budget for containerized applications. It can also enhance the benefits of containerization, such as automated resource allocation and optimum use of computing resources.
An overview of Kubernetes
Often called K8s, Kubernetes is an open-source container orchestration tool and industry standard. Google developed this system to automate containerized applications- or microservices- development, management, and scaling. This platform was created for several reasons but was primarily developed with optimization in mind. Automating many DevOps processes, which developers once handled manually, has significantly simplified the work of software developers, allowing them to focus on more pressing, complex tasks.
Based on its applications, Kubernetes is the fastest-growing project in open-source software history after Linux. Data shows that from 2020 to 2021, the number of Kubernetes engineers skyrocketed by 67%, reaching 3.9 million. This figure represents 31% of all backend developers.
One of the main reasons Kubernetes is so popular is the increasing demand for businesses to support their microservice architecture. Kubernetes makes apps more flexible, productive, and scalable by providing load balancing and simplifying container management.
Other benefits include:
- Container orchestration savings: Once Kubernetes is configured, apps run with minimal downtown while performing well.
- Increased efficiency among DevOps teams, allowing for faster development and deployment times.
- The ability to deploy workloads across several cloud services.
- Since Kubernetes is an open-source tool and community-led project, there is strong support for continuous improvement and innovation. A large ecosystem of tools has been designed to use with this platform.
What is EKS?
Data shows that of those running containers in the public cloud, 78% are using AWS, followed by Azure (39%), GCP (35%), IBM Cloud (6%), Oracle Cloud (4%), and Other (4%). AWS remains the dominant provider.
AWS offers a commercial Kubernetes service — Amazon Elastic Kubernetes Service (EKS). This managed service allows you to run Kubernetes on AWS and on-premises, benefiting from the vast number of available services. By integrating with AWS services, you’ll benefit from supply scalability and security for your applications. For example, IAM is used for reliability, Elastic Load Balancer for load distribution, and Amazon ECR for container image.
Adding a system like AWS EKS allows you to run Kubernetes applications on various systems, like AWS Fargate. Along with benefiting from greater performance, scalability, and reliability, you can integrate with AWS networking and security services such as AWS Virtual Private Cloud. It will enhance your Kubernetes system, which will optimize your business overall.
AWS EKS can help you gain greater control over your servers or simplify cluster setup.
Amazon EKS functionality
Amazon EKS simplifies Kubernetes management by handling the control plane while giving users flexibility over worker node configurations. Its architecture is designed for scalability, reliability, and seamless integration with the AWS ecosystem.
1. Core architecture
Amazon EKS operates through two primary components: the Kubernetes control plane and worker nodes.
- Kubernetes control plane: This plan is managed entirely by AWS and includes Kubernetes API servers and management services spread across multiple AWS Availability Zones, ensuring high availability.
- Worker nodes: These are deployed within a customer’s Amazon VPC, allowing full administrative control over scaling, upgrades, and security configurations.
2. Deployment options
Amazon EKS supports several deployment models to meet varying business needs:
- Managed node groups: AWS provisions, scales, and automatically manages worker nodes.
- Self-managed nodes: Users deploy and manage their own worker nodes with complete customization.
- Fargate: Serverless Kubernetes deployment where AWS manages both the control plane and the underlying infrastructure, enabling container execution without EC2 instances.
- Hybrid deployments: Kubernetes clusters can be extended to on-premises infrastructure using Amazon EKS Anywhere.
3. AWS service integrations
Amazon EKS integrates with a broad range of AWS services for enhanced functionality:
- Networking: Amazon VPC provides isolated networking environments, Elastic Load Balancing ensures traffic distribution, and AWS PrivateLink secures data exchange.
- Storage: Amazon EBS is used for persistent storage, Amazon S3 is used for object storage, and Amazon EFS is used for file storage.
- Security: IAM manages user access, AWS Key Management Service (KMS) secures sensitive data, and AWS Shield protects against DDoS attacks.
- Monitoring and logging: Amazon CloudWatch collects performance metrics, AWS CloudTrail tracks activity logs, and AWS X-Ray provides distributed tracing.
How does AWS EKS work with Kubernetes?
AWS EKS supplies an expandable and available Kubernetes control panel. For optimum performance, it runs this control panel across three availability zones. AWS EKS and Kubernetes collaborate in several different areas to ensure your company receives the best performance.
- AWS Controller lets you manage and control your AWS service from your Kubernetes environment. Using AWS EKS, you can simplify building a Kubernetes application.
- EKS can integrate with Kubernetes clusters. Developers can use it as a single interface to organize and resolve issues in any Kubernetes application implemented on AMS.
- EKS add-ons are pieces of operational software. These add-ons will increase the functionality of Kubernetes operations. When you start an AMS cluster, you can select any applicable add-ons. Some of these add-ons include Kubernetes tools for networking and AWS service integrations.
Benefits of AWS EKS over standalone Kubernetes
There are several benefits of AWS EKS when compared to native Kubernetes.
- Implementing AWS EKS will remove time-consuming processes like creating the Kubernetes master cluster. With standalone Kubernetes, your employees would have to spend many company hours designing and building different infrastructures.
- AMS EKS eliminates a singular point of failure as the Kubernetes control plane is spread across various AWS availability zones.
- EKS is embedded with a range of AWS monitoring services, which means it has scalability and can grow as your company expands. It makes features like AWS Identity Access Management and Elastic Load Balancing straightforward and convenient for your employees.
Amazon EKS use cases
Amazon EKS supports a variety of enterprise use cases, making it a versatile platform for running containerized applications. Below are some of the most common applications where Amazon EKS excels:
1. Deploying in hybrid environments
Amazon EKS enables consistent Kubernetes management across cloud, on-premises, and edge environments. This flexibility allows enterprises to run sensitive workloads on-premises while leveraging cloud scalability for other applications.
2. Supporting machine learning workflows
Amazon EKS simplifies the deployment of machine learning models by enabling scalable and efficient data processing. Frameworks like TensorFlow and PyTorch can run seamlessly on EKS, with access to AWS services like Amazon S3 for data storage and AWS SageMaker for model training and deployment.
3. Building web applications
Web applications benefit from Amazon EKS’s automatic scaling and high availability features. EKS supports microservices-based architectures, allowing developers to build and deploy resilient web applications using services such as Amazon RDS for databases and Amazon ElastiCache for caching.
4. Running CI/CD pipelines
Development teams can use Amazon EKS to build and manage CI/CD pipelines, automating software release processes. Integration with tools like Jenkins, GitLab, and CodePipeline ensures continuous integration and deployment for modern applications.
Amazon EKS best practices
To ensure smooth operation and maximum efficiency when managing Amazon EKS clusters, following best practices centered around automation, security, and performance optimization is essential. These practices help minimize downtime, improve scalability, and reduce operational overhead.
1. Automate Kubernetes operations
Automation reduces manual intervention and increases reliability. Infrastructure-as-code tools like Terraform or AWS CloudFormation can be used to define and deploy clusters. CI/CD pipelines can streamline code deployment and updates. Kubernetes-native tools like Helm can be used for package management, and ArgoCD can be used for GitOps-based continuous delivery.
2. Strengthen security
Securing your Kubernetes environment is crucial. Implement the following security best practices:
- Access control: Use AWS Identity and Access Management (IAM) roles and policies to manage access rights.
- Network security: Enable Amazon VPC for isolated network environments and restrict inbound/outbound traffic.
- Data encryption: Use AWS Key Management Service (KMS) for data encryption at rest and enforce TLS for data in transit.
- Cluster hardening: Regularly update Kubernetes versions and EKS node groups to apply the latest security patches.
3. Optimize cluster performance
Performance optimization ensures workloads run efficiently without overspending on resources. Consider the following strategies:
- Auto-scaling: Enable Kubernetes Cluster Autoscaler to adjust the number of worker nodes based on demand automatically.
- Right-sizing resources: Use AWS Compute Optimizer to recommend the best EC2 instance types and sizes.
- Monitoring and logging: Amazon CloudWatch and AWS X-Ray are used to monitor and trace application performance.
AWS EKS operation
AWS EKS has two main components — a control plane and worker nodes. The control plane has three Kubernetes master nodes that will be installed in three different availability zones. It runs on the cloud controlled by AMS. You cannot manage this control panel directly; it is managed through AMS.
The other component is worker nodes, which run on the organization’s private cloud and can be accessed through Secure Shell (SSH). The worker nodes control your organization’s containers, and the control panels organize and monitor the containers’ creation and place of origin.
As EKS operations are flexible, you can position an EKS cluster for every organization or use an EKS cluster from multiple applications. Without EKS, you would have to run and monitor the worker nodes and control panel, as it would not be automated. Implementing an EKS operation frees organizations from the burden of operating Kubernetes and all the infrastructure that comes with it. AWS does all the heavy lifting.
Here is how to get started with AWS EKS.
Amazon EKS pricing
Understanding Amazon EKS pricing is essential for effectively managing costs. Pricing is determined by various factors, including cluster management, EC2 instance types, vCPU usage, and additional AWS services used alongside Kubernetes.
Amazon EKS cluster pricing
All Amazon EKS clusters have a per-cluster, per-hour fee based on the Kubernetes version. Standard Kubernetes version support lasts for the first 14 months after release, followed by extended support for another 12 months at a higher rate.
| Kubernetes Version Support Tier | Pricing |
| Standard Kubernetes version support | $0.10 per cluster per hour |
| Extended Kubernetes version support | $0.60 per cluster per hour |
Amazon EKS auto mode
EKS Auto Mode pricing is based on the duration and type of Amazon EC2 instances launched and managed by EKS Auto Mode. Charges are billed per second with a one-minute minimum and are independent of EC2 instance purchase options such as Reserved Instances or Spot Instances.
Amazon EKS hybrid nodes pricing
Amazon EKS Hybrid Nodes enable Kubernetes management across cloud, on-premises, and edge environments. Pricing is based on monthly vCPU-hour usage and varies by usage tier.
| Usage Range | Pricing (per vCPU-hour) |
| First 576,000 monthly vCPU-hours | $0.020 |
| Next 576,000 monthly vCPU-hours | $0.014 |
| Next 4,608,000 monthly vCPU-hours | $0.010 |
| Next 5,760,000 monthly vCPU-hours | $0.008 |
| Over 11,520,000 monthly vCPU-hours | $0.006 |
Other AWS services pricing
When using Amazon EKS, additional charges may apply based on the AWS services you use to run applications on Kubernetes worker nodes. For example:
- Amazon EC2: For instance capacity
- Amazon EBS: For volume storage
- Amazon VPC: For public IPv4 addresses
AWS Fargate pricing: Charges are based on vCPU and memory resources from container image download to pod termination, billed per second with a one-minute minimum.
To estimate your costs, use the AWS Pricing Calculator.
Maximize your Kubernetes investment with LogicMonitor
AWS EKS is a system that can streamline and optimize your company. However, many need to be using it to its full potential. Monitoring will help you get the most out of your investment via key metrics and visualizations.
LogicMonitor offers dedicated Kubernetes monitoring dashboards, including insights into Kubernetes API Server performance, container health, and pod resource usage. These tools provide real-time metrics to help you detect and resolve issues quickly, ensuring a reliable Kubernetes environment. These insights help drive operational efficiency, improve performance, and overcome common Kubernetes challenges.
Learn more here:
- LogicMonitor & AWS: Maximize your Kubernetes Investment with Monitoring
- LogicMonitor’s Kubernetes Monitoring Overview
If you need a cloud monitoring solution, LogicMonitor can help you maximize your investment and modernize your hybrid cloud ecosystem. Sign up for a free trial today!
A growing number of enterprises are shifting toward a multi-cloud environment with the rise of remote and hybrid work. In fact, 76% of organizations have already adapted to a multi-cloud infrastructure.
These dynamic networks offer companies many reported advantages, such as scalability, agility, and optimized performance. When it comes to a company’s digital transformation and transition to a multi-cloud environment, Software-Defined Wide-Area Networking (SD-WAN) often emerges as a top consideration.
What is SD-WAN?
Many companies with a multi-cloud network have replaced the conventional Multiprotocol Label Switching (MPLS) transport protocols with SD-WAN.
SD-WAN refers to a software-based method of managing wide-area telecommunication networks. With SD-WAN, you can combine transport services (including MPLS circuitry) through encrypted overlay tunnels to communicate and prioritize enterprise data across internal applications.
There is a good reason for SD-WAN’s widespread appeal. While the MPLS has proven reliable for decades in handling predetermined communication pathways, it lacks the flexibility and agility for managing modern multi-cloud environments with vast and dispersed endpoints.
Unpacking the SD-WAN architecture
SD-WAN networks run on an abstract infrastructure divided into a control and forwarding plane. The control plane functions from a centralized location as a remotely controlled network, eliminating the need for on-premise technicians. At a granular level, SD-WAN features three components that comprise its virtualized infrastructure, removing the reliance on specific hardware.
SD-WAN Edge
The SD-WAN Edge refers to the user endpoint within the network. These may include multi-cloud systems, on-premise data centers, and SaaS platforms.
SD-WAN Controller
An SD-WAN Controller offers a transparent view of connected networks and facilitates decision-making policies for orchestrators. Essentially, an SD-WAN controller provides centralized management of enterprise data flow and authenticates devices linked to your network.
SD-WAN Orchestrator
Your designated SD-WAN Orchestrator manages and systematizes policies and traffic among authorized controllers. The component streamlines intuitive workflows across your enterprise networks (e.g., branch offices). Essentially, orchestrators are the definitive bridge between your controller and edge routers. You can upgrade orchestrator functions by providing enhanced analytics and performance SLAs that expedite troubleshooting processes and network fixes.
Top SD-WAN providers
The modern market features an assortment (and an ever-growing number) of SD-WAN vendors, each providing unique features and functionalities. Therefore, you will benefit from researching the leading vendors to access the best solutions in network function virtualization (NFV) and software-defined networking (SDN) deployments.
Fortinet Secure SD-WAN
With superior security standards, Fortinet offers services that drive high-performance network capabilities. The vendor’s SD-WAN structure helps your organization manage precious enterprise data without compromising speed or function. Also, Fortinet’s SD-WAN services have undergone rigorous testing, with Gartner validating the solution for its high performance, reliable security, and low total cost of ownership (TCO).
Using Fortinet’s SD-WAN technology guarantees several improvements to communication processes with built-in encryption protection and sandboxing features that prevent data loss. Fortinet provides frictionless integration to your branch infrastructure for smooth data management across LANs, optimizing hybrid SD-Branch layouts.
Versa Networks (OS)
Versa Networks’ SD-WAN solution features an integrated platform with premium security capabilities. The technology’s intuitive functions include multi-cloud connectivity, full multi-tenancy and micro-segmentation of businesses, and context-based network and security policies throughout registered networks.
Versa prioritizes optimal network security as one of its core missions. In 2021, Gartner recognized Versa Networks as a visionary in the Gartner® Magic Quadrant™ for Network Firewalls, emerging as the preferred choice from an in-depth comparison of the top 19 vendors in the communications industry. The SD-WAN offers access to Versa’s Secure Access Service Edge (SASE), enhancing user security through multi-factor authentication, data protection, and SSL decryption.
Aryaka
Aryaka is an innovative service provider that combines SD-WAN technology with a secure web gateway as a one-stop network solution. Specifically, Aryaka’s hybrid approach equips your organization with a zero-trust WAN that significantly reduces business and operational risks. As a result, Aryaka positions itself as a leader among SD-WAN vendors, promoting the fastest service of its kind within the industry.
Gartner has recognized the zero-trust vendor as the customer’s choice for three consecutive years through outstanding KPI standards, including 99.999% SLA performance and uptime and a 65 net promoter score rating five times the industry average. Your business can manage optimal security and communication performance from a single contact point through Aryaka’s SD-WAN layouts.
Understanding the pros of SD-WAN
SD-WANs give enterprise networks a general boost from conventional MPLS systems as they improve connectivity across separate applications and off-site locations.
Business traffic prioritization
SD-WAN helps your organization prioritize critical enterprise data by selecting the most cost-effective and efficient communication path. When you set up the technology’s load-balancing and traffic-steering capabilities, your SD-WAN network can recognize business applications and allocate bandwidth volume according to individual service requirements. Traffic steering lets your team manage multiple parallel connections in business traffic with a responsive system, providing rate-limitless sensitive applications with optimal bandwidth.
Affordability
An SD-WAN approach applies private and distributed data exchange and control measures, which function seamlessly across diverse project environments. The process optimizes network functionality and cost-effectiveness by securing data from the cloud and immediate networks.
Application performance optimization
SD-WAN’s structured infrastructure drives optimal application performance across enterprise networks. Specifically, the agile transport mode fulfills the latest enterprise compliance mandates and automates traffic steering based on business priorities. Additionally, SD-WAN provides a centralized control center for managing enterprise data across multi-cloud endpoints, connecting with authorized SaaS and IaaS collaborators and vendors without complication.
Diverse transport methods
With SD-WAN networks, users can access multiple transport channels, including direct broadband connection, 5G, and traditional MPLS circuits. The flexible arrangement improves data availability for undisrupted and optimized communications. You can expect optimal application performance across cloud systems, on-premise servers, and SaaS platforms like Microsoft 365 or Salesforce.
The cons of SD-WAN
While SD-WAN networks seem like a step in the right direction in multi-cloud environments, they pose some user considerations as a developing technology.
No on-site security function
SD-WAN networks lack an on-site security function, so you must separately install and manage a security policy to safeguard networks against online threats. An unprotected SD-WAN infrastructure might face considerable risks from data breaches such as the Colonial Pipeline Hack, which resulted in significant data loss and reputational damage.
No Quality of Service (QoS) under specific scenarios
Communication networks that rely on SD-WAN provisions lack a proper QoS. Essentially, these networks will not receive the full technical benefits of SD-WAN, including path control, traffic shaping, and forward error correction.
Vendor concerns
SD-WAN vendors may provide their services and equipment at a higher cost. Also, due to the variability of service standards, some vendors may need more capability to service software-based networking (SDN).
Revisiting MPLS
In the 1990s, MPLS replaced standard internet protocol (IP) routing and became the primary transport method for enterprise data. While the infrastructure offers scalability, optimized bandwidth utilization, and enhanced security – by serving as a virtual private network – it requires installing and maintaining physical links. This process has become increasingly complex, costly, and impractical in a progressively multi-cloud landscape.
MPLS infrastructure
MPLS is a protocol-independent solution with predetermined paths between routers in the MPLS network; each label comprises four components:
- The label value that determines the direction of the data packet
- The traffic class field
- The bottom of the stack flag
- The time-to-life (TTL) field
Functionalities of the MPLS
The MPLS moves network traffic through predetermined labels instead of conventional addresses, guiding the data through private WANs (wide-area networks).
MPLS functions as layer 2.5 in the OSI seven-layer hierarchy between data links that use LANs and networks that run on internet-wide addressing. This infrastructure attributes a forwarding equivalence class (FEC) to each data packet within a network, which routers can decipher by comparing them against descriptive tables.
The routers update the outermost layer of the data packet as it travels through the FEC pathway and to the next hop, which is examined and submitted to the next layer. Users of the MPLS method can customize the information for each packet, essentially driving top performance in unified networks.
Private MPLS networks can provide your organization with a consistent and reliable means of managing communications in cloud-based environments.
Pros of MPLS
Your MPLS transport modes remain segregated from the public internet, making the infrastructure invulnerable to prevalent web-based attacks such as distributed denial of service (DDoS). As such, the enhanced security of MPLS offers the optimal performance of real-time data transportation by avoiding potential interceptions and packet loss within the open internet.
Despite the general security of MLPS (with SD-WAN combinations), some decision-makers may seek added protection from automated cloud monitoring across public and private connections.
Cons of MPLS
Most of the downsides to MPLS relate to its physical limitations and high cost compared to SD-WAN alternatives. In its original design, the MPLS catered to organizations communicating through remote branches of enterprise data centers. MPLS would conventionally backhaul data from branch offices for comprehensive security processing and distribution through on-premise hubs. However, many companies now prefer cloud services over MPLS. Additionally, the backhauling process often increases latency and reduces application performance.
Comparing SD-WAN with MPLS
A significant highlight of SD-WAN, unlike MPLS, lies in its transport-agnostic overlay structure. Your organization can benefit from the arrangement by applying and modifying policies across your WAN from a centralized location. Alternatively, MPLS functions via predetermined routes through physically installed connections, but its fixed circuits make managing changes across multiple user environments costly and complex.
Although SD-WAN might replace MPLS as the more popular transport choice for some companies, the technologies could co-exist depending on your enterprise arrangements. For instance, some companies may adopt a hybrid network management approach. Specifically, decision-makers would restrict MPLS use to on-premise legacy applications while offloading cloud-based programs to SD-WAN.
Additionally, some organizational leaders have adopted internet-augmented MPLS with SD-WAN. The advanced process increases organizational flexibility by enhancing MPLS with internet broadband links. These links prioritize networking decisions according to specific requirements, such as application type and optimal bandwidth volume.
Hybrid approaches
Many organizations are adopting hybrid approaches that combine the strengths of SD-WAN and MPLS. This strategy allows businesses to optimize performance and cost-effectiveness by leveraging the unique benefits of each technology for specific use cases.
How hybrid SD-WAN/MPLS solutions work
A hybrid approach integrates MPLS circuits with SD-WAN’s flexible, software-defined overlay. MPLS handles latency-sensitive and mission-critical applications that require guaranteed Quality of Service (QoS), while SD-WAN manages less critical traffic using cost-effective broadband or other transport methods. By dynamically routing traffic based on application requirements, hybrid setups ensure that each data type is delivered efficiently and securely.
For example:
- MPLS role: Ensures low-latency, high-reliability communication for applications like VoIP, video conferencing, and financial transactions.
- SD-WAN role: Routes non-critical traffic, such as email, file backups, and SaaS applications, through broadband connections, reducing MPLS bandwidth requirements and costs.
Scenarios where hybrid approaches excel
- Real-time applications with high bandwidth demand
Businesses requiring uninterrupted service for real-time applications, such as hospitals using telemedicine or financial institutions running stock trading platforms, can dedicate MPLS to these tasks while leveraging SD-WAN for less critical operations. - Multi-branch organizations
Enterprises with numerous branch offices can use MPLS for their headquarters and key locations, ensuring consistent performance for sensitive operations while using SD-WAN to connect smaller branches with broadband. - Global operations with varying network needs
Hybrid solutions are ideal for multinational organizations with offices in regions where MPLS availability or affordability varies. In these cases, MPLS can be prioritized in key regions while SD-WAN manages connections in remote or less-developed areas. - Disaster recovery and business continuity
By combining MPLS and SD-WAN, businesses can create highly resilient networks with failover capabilities. If MPLS circuits experience outages, SD-WAN dynamically reroutes traffic to maintain uptime. - Cloud-first strategies
Hybrid approaches enable organizations transitioning to cloud-based operations to retain MPLS for legacy applications while offloading cloud workloads to SD-WAN. This ensures seamless performance across both on-premise and cloud environments.
Decision-making checklist: Choosing between SD-WAN and MPLS
Selecting the right networking solution for your organization requires carefully evaluating your unique needs, priorities, and constraints. Use the following checklist to guide your decision-making process and determine whether SD-WAN, MPLS or a hybrid approach is the best fit for your enterprise:
1. Assess your network requirements
Do you have latency-sensitive applications, such as VoIP, video conferencing, or financial transactions, demanding guaranteed Quality of Service (QoS)?
- If yes, MPLS or a hybrid approach may be necessary.
Are your users distributed across multiple remote locations or regions with varying connectivity needs?
- If yes, SD-WAN offers better scalability and flexibility.
2. Evaluate your budget
What is your budget for networking infrastructure, including installation, maintenance, and operational costs?
- MPLS typically requires higher initial and ongoing investments due to physical circuits and hardware.
- SD-WAN offers a cost-effective alternative by leveraging existing broadband or internet connections.
3. Consider Scalability
Is your organization rapidly expanding or adopting a multi-cloud strategy?
- SD-WAN provides seamless scalability for growing networks and dynamic environments.
- MPLS may need to be more adaptable due to its reliance on fixed circuits.
4. Analyze Security Needs
Do you require private, highly secure connections for sensitive data?
- MPLS offers inherent security through private circuits but may need cloud integration for modern environments.
- For comprehensive protection, SD-WAN requires additional security layers, such as Secure Access Service Edge (SASE).
5. Examine Application Performance
Are your applications cloud-native, such as SaaS platforms or IaaS solutions?
- SD-WAN is optimized for cloud connectivity, enabling direct and efficient access to cloud applications.
- MPLS is more suitable for legacy on-premise applications that rely on data center backhauling.
6. Assess Management and Operational Complexity
Do you need centralized, simplified network management?
- SD-WAN provides centralized control and automation for effortless network monitoring and troubleshooting.
- MPLS requires more hands-on management, often needing on-premise technical support.
7. Plan for Future-Proofing
Is your organization prioritizing digital transformation, including support for hybrid work and zero-trust security models?
- SD-WAN, combined with SASE, aligns with cloud-first and modern security trends.
- MPLS may need help to keep pace with the agility required for these transitions.
8. Evaluate Hybrid Options
Would a combination of SD-WAN and MPLS better meet your needs?
- Use MPLS for critical real-time applications and SD-WAN for cost-effective handling of general traffic.
Alternatives to MPLS and SD-WAN
While MPLS has been a reliable transport method for enterprise networks, advancements in networking technology offer alternative solutions better suited for modern, cloud-first environments. These alternatives provide flexibility, scalability, and cost-efficiency for organizations looking to evolve beyond traditional MPLS setups.
VPN (Virtual Private Network)
VPNs provide a secure, encrypted tunnel for data transmission over the public internet. While they lack the QoS guarantees of MPLS, VPNs are a cost-effective solution for connecting remote users and smaller branch offices to corporate networks. VPNs work well for businesses prioritizing affordability and basic security over high-performance requirements.
5G networks
The rise of 5G technology offers a compelling alternative for enterprise networks. With ultra-low latency, high bandwidth, and widespread availability, 5G networks can support critical business applications that were previously reliant on MPLS. They are particularly effective for edge computing environments and mobile-first businesses.
Internet-based networking
Many organizations are turning to direct internet access (DIA) and broadband connections as replacements for MPLS. These options allow businesses to leverage high-speed, cost-effective public internet connections while pairing them with cloud-native security solutions like SASE to maintain performance and security.
Private LTE and CBRS
Private LTE and Citizen Broadband Radio Service (CBRS) networks are emerging as viable alternatives for enterprises requiring private, secure connectivity without the constraints of traditional MPLS. These technologies enable organizations to create their wireless networks, which are ideal for environments with unique coverage requirements, such as manufacturing facilities or campuses.
A summary of SD-WAN vs. MPLS
SD-WAN systems provide your organization with the trusted capabilities of managing multi-cloud environments with greater scalability and reliability. The modern data transport mode presents a more affordable and flexible solution that leverages MPLS, wireless, broadband, and virtual private networks (VPNs) to maintain high speed across remote environments.
On the other hand, MPLS boosts network efficiency through predetermined routes, and it is best suited for enterprise environments that continue to rely on data centers. In both instances, you can significantly improve observability by applying a trusted REST API that exposes all functionalities within your networks without tedious wrapper codes.
REST APIs with multiple integrations offer added convenience for managing data across multi-cloud platforms, preferably with automated webhooks that send real-time information between applications.
As the WAN continues to evolve, enterprise leaders must have the freedom and accessibility to navigate between private and public Internet infrastructures. Comparing SD-WAN vs. MPLS, you can successfully align your company’s specific requirements with the necessary product sets to achieve the best outcomes.
SD-WAN in the future of network communications
Through SD-WAN, your organization maintains optimized software functions regardless of location, elevating your overall user experience while reducing IT expenses. Combining SD-WAN networks with intelligent monitoring can help you streamline and optimize business continuity in work-from-home and hybrid settings.
Another major factor in SD-WAN adoption is its independence from tedious MPLS circuitry migrations. If your enterprise network currently runs on the public internet, you can choose to retain your service provider by moving or reconfiguring the virtualized elements of your WAN.
Next, SD-WAN capabilities support the core functions of Secure Access Service Edge (SASE) structures, a term Gartner coined in 2019. Advanced SASE setups provide your enterprise with a safe, reliable, unified cloud-based network.
SASE also helps your organization transport security and access between multiple user endpoints, such as branch offices and mobile applications. The structure operates through a combination of SD-WAN functionalities and cloud-based security solutions. Ultimately, SD-WAN proves integral in supporting your company through future-proofing communications for a cloud-first landscape.
Take your network management to the next level with LogicMonitor. Discover how our platform integrates seamlessly with SD-WAN to provide unparalleled visibility, performance monitoring, and scalability for your enterprise.
Since the revolutionization of the concept by Docker in 2013, containers have become a mainstay in application development. Their speed and resource efficiency make them ideal for a DevOps environment as they allow developers to run software faster and more reliably, no matter where it is deployed. With containerization, it’s possible to move and scale several applications across clouds and data centers.
However, this scalability can eventually become an operational challenge. In a scenario where an enterprise is tasked with efficiently running several containers carrying multiple applications, container orchestration becomes not just an option but a necessity.
What is container orchestration?
Container orchestration is the automated process of managing, scaling, and maintaining containerized applications. Containers are executable units of software containing application code, libraries, and dependencies so that the application can be run anywhere. Container orchestration tools automate the management of several tasks that software teams encounter in a container’s lifecycle, including the following:
- Deployment
- Scaling and load balancing/traffic routing
- Networking
- Insights
- Provisioning
- Configuration and scheduling
- Allocation of resources
- Moving to physical hosts
- Service discovery
- Health monitoring
- Cluster management
How does container orchestration work?
There are different methodologies that can be applied in container orchestration, depending on the tool of choice. Container orchestration tools typically communicate with YAML or JSON files that describe the configuration of the application. Configuration files guide the container orchestration tool on how and where to retrieve container images, create networking between containers, store log data, and mount storage volumes.
The container orchestration tool also schedules the deployment of containers into clusters and automatically determines the most appropriate host for the container. After a host has been determined, the container orchestration tool manages the container’s lifecycle using predefined specifications provided in the container’s definition file.
Container orchestration tools can be used in any environment that runs containers. Several platforms offer container orchestration support, including Kubernetes, Docker Swarm, Amazon Elastic Container Service (ECS), and Apache Mesos.
Challenges and best practices in container orchestration
While container orchestration offers transformative benefits, it’s not without its challenges. Understanding these potential pitfalls and adopting best practices can help organizations maximize the value of their orchestration efforts.
Common challenges
- Complexity in setup and operation
Setting up container orchestration can be daunting, especially for teams new to the technology. Configuring clusters, managing dependencies, and defining orchestration policies often require significant expertise. The steep learning curve, particularly with tools like Kubernetes, can slow adoption and hinder productivity. - Security risks with containerized environments
Containerized applications introduce unique security challenges, including vulnerabilities in container images, misconfigurations in orchestration platforms, and potential network exposure. Orchestrators need robust security measures to safeguard data and applications. - Vendor lock-in with proprietary solutions
Organizations relying on proprietary orchestration tools or cloud-specific platforms may find it difficult to migrate workloads or integrate with other environments. This can limit flexibility and increase long-term costs. - Performance bottlenecks
Resource contention, inefficient scaling policies, and poorly optimized configurations can lead to performance issues, impacting application reliability and user experience.
Best practices for successful container orchestration
- Simplify and automate with CI/CD pipelines
Automating workflows using Continuous Integration and Continuous Deployment (CI/CD) pipelines reduces manual intervention and ensures consistency in deployments. Tools like Jenkins or GitLab can integrate seamlessly with container orchestration platforms to streamline operations. - Proactively monitor and manage clusters
Monitoring tools like LogicMonitor can be used to track container performance, resource usage, and application health. Proactive alerts and dashboards help identify and resolve issues before they impact users, ensuring reliability and uptime. - Prioritize security from the start
Implement security best practices such as:- Regularly scanning container images for vulnerabilities.
- Enforcing Role-Based Access Control (RBAC) to restrict permissions.
- Configuring network policies to isolate containers and protect sensitive data. By building security into the orchestration process, organizations can mitigate risks and maintain compliance.
- Start small and scale gradually
Begin with a minimal setup to gain familiarity with orchestration tools. Focus on automating a few processes, then gradually expand the deployment to handle more complex workloads as the team’s expertise grows. - Optimize resource allocation
Regularly review resource usage and scaling policies to ensure efficient operation. Use orchestration features like auto-scaling to adjust resources based on demand dynamically. - Choose flexible, open solutions
To avoid vendor lock-in, prioritize tools like Kubernetes that support multi-cloud or hybrid deployments and integrate with a wide range of environments and services.
How does Kubernetes orchestration work?
Kubernetes is an open-source container orchestration platform that is considered the industry standard. The Google-backed solution allows developers and operators to deliver cloud services, either as Platform-as-a-Service (PaaS) or Infrastructure-as-a-Service (IaaS). It’s a highly declarative solution, allowing developers to declare the desired state of their container environment through YAML files. Kubernetes then establishes and maintains that desired state.
The following are the main architecture components of Kubernetes:
Nodes
A node is a worker machine in Kubernetes. It may be virtual or physical, depending on the cluster. Nodes receive and perform tasks assigned from the Master Node. They also contain the necessary services to run pods. Each node comprises a kubelet, a container runtime, and a kube-proxy.
Master Node
This node controls all the worker nodes and originates all assigned tasks. It does this through the control pane, which is the orchestration layer that exposes the API and interfaces to define, deploy, and manage the lifecycles of containers.
Cluster
A cluster represents the master node and multiple worker nodes. Clusters combine these machines into a single unit to which containerized applications are deployed. The workload is then distributed to various nodes, making adjustments as nodes are added or removed.
Pods
Pods are the smallest deployable computing units that can be created and managed in Kubernetes. Each Pod represents a collection of containers packaged together and deployed to a node.
Deployments
A deployment provides declarative updates for Pods and ReplicaSets. It enables users to designate how many replicas of a Pod they want running simultaneously.
How does Docker orchestration work?
Docker, also an open-source platform, provides a fully integrated container orchestration tool known as Docker Swarm. It can package and run applications as containers, locate container images from other hosts, and deploy containers. It is simpler and less extensile than Kubernetes, but Docker provides the option of integration with Kubernetes for organizations that want access to Kubernetes’ more extensive features.
The following are the main architectural components of Docker Swarm:
Swarm
A swarm is a cluster of Docker hosts that run in swarm mode and manage membership and delegation while also running swarm services.
Node
A node is the docker engine instance included in a swarm. It can be either a manager node or a worker node. The manager node dispatches units of work called tasks to worker nodes. It’s also responsible for all orchestration and container management tasks like maintaining cluster state and service scheduling. Worker nodes receive and execute tasks.
Services and Tasks
A service is the definition of a task that needs to be executed on the nodes. It defines which container images to use and which commands to execute inside running containers.
A task carries a container alongside the commands to run inside the container. Once a task is assigned to a node, it cannot move to another node.
How does container orchestration work with other Platforms?
Although Docker and Kubernetes are leading the pack when it comes to container orchestration, other platforms are capitalizing on their open-source software to provide competition.
Red Hat OpenShift is an open-source enterprise-grade hybrid platform that provides Kubernetes functionalities to companies that need managed container orchestration. Its framework is built on a Linux OS that allows users to automate the lifecycles of their containers.
Google Kubernetes Engine is powered by Kubernetes and enables users to easily deploy, manage, and scale Docker containers on Google Cloud.
Other platforms like Apache Mesos and Amazon ECS have developed their own container tools that allow users to run containers while ensuring security and high scalability.
Tool comparisons: Finding the right fit for your needs
When choosing the best container orchestration tool for an organization, several factors have to be taken into consideration. These factors vary across different tools. With a tool like Mesos, for instance, the software team’s technical experience must be considered as it is more complex than simple tools like Swarm. Organizations also have to consider the number of containers to be deployed, as well as application development speed and scaling requirements.
With the right tools and proper resource management, container orchestration can be a valuable approach for organizations looking to achieve improved productivity and scalability.
Below is a comparison of the most popular tools in the container orchestration space, highlighting their key features and ideal use cases.
| Tool | Scalability | Learning Curve | Supported Environments | Key Integrations | Best For |
| Kubernetes | Excellent for large, complex setups | Steep, requires expertise | On-premises, cloud (AWS, GCP, Azure) | CI/CD pipelines, monitoring tools, Istio | Enterprises requiring robust orchestration for multi-cloud or hybrid environments. |
| Docker Swarm | Moderate, ideal for small clusters | Low, easy for Docker users | On-premises, cloud | Docker ecosystem, Kubernetes (optional integration) | Small to medium teams seeking straightforward orchestration within the Docker platform. |
| Amazon ECS | Highly scalable within AWS ecosystem | Moderate, AWS-specific knowledge | AWS (native service) | AWS services (EKS, CloudWatch, IAM) | Businesses already leveraging AWS services for containerized applications. |
| Red Hat OpenShift | Enterprise-grade, highly scalable | Moderate, depends on Kubernetes base | Hybrid environments, Linux-based on-premise/cloud | OpenShift tools, Kubernetes integrations | Enterprises needing managed Kubernetes with robust security and enterprise-grade features. |
| Apache Mesos | Extremely scalable for large systems | High, requires advanced expertise | On-premises, private cloud | Marathon, custom integrations | Advanced users managing diverse workloads beyond containers, such as big data and microservices. |
Examples of container orchestration
Container orchestration provides a number of benefits for organizations, but what do those benefits look like in real-world work situations? We included a couple of common orchestration examples below:
First, consider a large e-commerce platform that experiences heavy traffic during the holiday season. In the past, that platform would have to manually provision additional servers to handle the increased holiday load, which is a time-consuming and error-prone process. With container orchestration, the platform can use an auto-scaling feature that automatically provisions additional containers as traffic increases and scales back down when traffic decreases. That way, increased traffic for the holiday rush can die down in January once everyone buys, returns, and exchanges their items.
Second, consider a company that has a website, a mobile app, and a back-end processing system that all runs on different servers in different environments. In the past, managing these different applications and environments would require much manual effort and coordination. With container orchestration, the company can use a single platform to manage all of its containers and environments, allowing it to easily deploy, manage, and scale its applications across different environments. This allows the company to adopt new technologies more easily and streamline its development process.
Monitor your containers with LogicMonitor today
Container orchestration is a critical component of modern application development, enabling teams to efficiently manage, scale, and secure containerized environments. By addressing the challenges of complexity, security, and resource management, and leveraging best practices like CI/CD pipelines and proactive monitoring, organizations can maximize the benefits of container orchestration while minimizing operational overhead.
To fully realize the potential of container orchestration, having a reliable monitoring solution is essential. LogicMonitor offers scalable, dynamic monitoring for ephemeral containerized resources alongside your hybrid cloud infrastructure. With LogicMonitor, you gain visibility into your Kubernetes and Docker applications through a single, unified platform that automatically adapts to your container resource changes.
What is NoSQL?
NoSQL is a non-tabular database that has a different data structure than relational tables. It is sometimes referred to as Non-SQL. NoSQL typically avoids relational data storage; however, while it can handle relationships in data storage, those relationships are built for specialized purposes.
There is much debate regarding SQL vs. NoSQL, with each data management system geared toward specific uses. Unlike SQL, which was developed in the 1970s to limit data duplication, NoSQL is a relatively new type of database. NoSQL came about in response to increasing amounts of data, and it uses a distributed system to help organize large amounts of structured and unstructured data. NoSQL is popular in business tech and other industries, with large organizations such as Amazon, Google, and LinkedIn using NoSQL databases.
Today, large companies are increasingly using NoSQL for data management. For example, a business that needs to store large amounts of unstructured and structured data or manage real-time streaming will want to consider NoSQL.
How NoSQL databases work
NoSQL databases function differently from traditional relational databases, offering a more flexible and scalable approach to data management. Their unique operational mechanisms make them well-suited for handling large-scale, distributed data environments.
NoSQL databases use flexible schemas, allowing dynamic and adaptable data models. Unlike SQL databases with predefined schemas, NoSQL supports various data types, including structured, semi-structured, and unstructured formats. Developers can update schemas without disrupting existing records, enabling rapid application development.
These databases also operate on distributed architectures, spreading data across multiple servers or nodes to ensure high availability, fault tolerance, and seamless scaling. Data replication guarantees durability, while partitioning efficiently distributes workloads to maintain performance under heavy demand.
Additionally, NoSQL terminology differs from SQL’s traditional structure. Collections in NoSQL function similarly to tables, grouping related data. Documents replace rows, allowing more flexible records. Some NoSQL models use key-value pairs or column families instead of columns to organize data.
Types of NoSQL databases
The structure and layout of different NoSQL database types depend on the data model. The four main structures are document, graph, key-value, and wide-column.
Document Databases – These databases store data similar to JavaScript Object Notation (JSON). Every document will contain pairs of values and fields, but it does not need foreign keys because specific relationships between documents don’t exist. Other essential features include fast creation, easy maintenance, flexible schema, and open formats.
Graph Databases – This format is primarily for data represented in a graph, such as road maps and public transportation information. The graphs store data in edges and nodes. Nodes generally contain information about people, places, and things, while edges store relational information between the nodes. Using a graph database enables quick identification of data relationships.
Wide-Column Databases – A wide-column database stores information in columns instead of rows. The columns form subgroups, and columns in the same family or cluster can contain different data types. Databases with columns read data more efficiently, and each column has a dynamic schema and isn’t fixed in a table. If you want to store large data, you’ll likely want to consider using wide-column databases.
Key-Value Databases – With the simplest format, key-value databases only have two columns containing keys and values. More extensive data models are sometimes extensions of the key-value database, which uses the associative array as the basic data model. Data also comes in a collection of key-value pairs, and each key never appears more than once in each collection. Important features of this type of database include simplicity, speed, and scalability.
You’ll also see several specific types of NoSQL databases. Examples include:
- BigTable
- Cassandra
- CouchDB
- FaunaDB
- HBase
- MongoDB
- Redis
NoSQL use cases
NoSQL databases excel in handling diverse and complex data environments, making them indispensable for a wide range of modern applications. Their scalability, flexibility, and high performance allow businesses to tackle demanding workloads effectively.
Real-time data management is one of the most compelling use cases for NoSQL. These databases handle large streams of incoming data with minimal latency, making them ideal for real-time analytics, fraud detection, and live social media feeds. Their ability to process data at lightning speed ensures a seamless user experience even during peak demand.
NoSQL databases play an important role in cloud security by supporting dynamic data models and secure storage. Their distributed nature ensures data integrity, availability, and disaster recovery, making them valuable for enterprises managing sensitive information across multiple cloud environments.
High-availability apps benefit greatly from NoSQL’s fault-tolerant and distributed design. Industries like finance, healthcare, and telecommunications rely on NoSQL databases to maintain uptime and continuous service delivery, even during infrastructure failures or spikes in user traffic.
Diverse workloads such as IoT and e-commerce also thrive with NoSQL. In IoT applications, vast amounts of sensor data require scalable storage solutions that can handle real-time processing and analysis. Similarly, e-commerce platforms depend on NoSQL databases for personalized product recommendations, dynamic pricing, and efficient inventory management.
Benefits
NoSQL offers several benefits:
- Easy for developers to use – One of the first advantages of NoSQL is that some systems only require a few lines of code. The databases also require less general maintenance.
- Flexible schemas – NoSQL is non-rigid, making testing and implementing updates easier. This is necessary for most modern applications because fields are different, and you will often need to make changes quickly and easily.
- Horizontal scaling – Expanding NoSQL is relatively easy and inexpensive, providing horizontal scaling because of its lack of structure. This means every element is independent and doesn’t need links. On the other hand, SQL will require upgrades such as more RAM or CPUs for vertical expansion.
- High performance – NoSQL often has higher performance levels than SQL because it doesn’t need to query data through various tables. Since things move much quicker with all the information in one database, doing 10,000 queries each second with some NoSQL databases is possible.
- Large data storage – NoSQL databases have the potential to store massive amounts of data sets, and they can do so at high rates of speed. For example, Cloud BigTable is a NoSQL database that lets you store structured data while allowing addition and deletion without disturbance.
Drawbacks
The potential drawbacks include the following:
- Requires multiple databases – Since the databases are specialized for particular use cases, you’ll need to use various data models and databases. You might still need to use SQL to help streamline the overall process.
- Requires more support – NoSQL is much newer than SQL. SQL is, therefore, more mature and has a lot of online instructional support. With NoSQL, you’ll likely have more difficulty finding expert support when you need assistance.
- Lack of consistency – NoSQL databases lack standardization, and the programming language and design of these databases vary extensively. This variation among NoSQL products is more extensive than with SQL databases.
- Lack of compatibility – NoSQL is not always entirely compatible with SQL instructions.
- Limited ACID applications – Most NoSQL systems don’t support ACID (atomicity, consistency, isolation, durability) transactions. MongoDB is an exception to this situation.
Choosing a NoSQL database
Selecting the right NoSQL database depends on several factors that align with your organization’s data management needs and business goals. NoSQL databases come in various models, each suited to specific use cases, making it essential to evaluate your options carefully. Key considerations include:
1. Data model selection
- Document databases: Ideal for applications requiring flexible schemas, such as content management systems.
- Key-value stores: Best for caching and real-time session management.
- Wide-column stores: Useful for high-volume analytical applications.
- Graph databases: Perfect for applications emphasizing relationships, like social networks.
2. Consistency trade-offs
- Consider your application’s tolerance for data inconsistency. NoSQL databases often sacrifice strict consistency for availability and scalability, following the CAP theorem.
- Use databases with configurable consistency settings if data accuracy is critical.
3. Cloud compatibility
- Choose a NoSQL database that integrates seamlessly with your cloud provider’s ecosystem.
- Consider managed services to reduce operational overhead and focus on development.
4. Migration strategies
- Plan for data migration if switching from a relational database to NoSQL.
- Ensure your team has the skills and tools necessary for a smooth migration process.
Assessing these factors can help you identify the NoSQL database that best meets your business needs, ensuring optimal performance, scalability, and reliability.
What is MongoDB?
MongoDB is a type of NoSQL database that is document-oriented and uses various documents and collections. It is primarily for high-volume data storage. Key-value pairs are the basic unit for MongoDB.
The following are a few of the essential features of MongoDB:
- MongoDB is very scalable. This system allows developers to write code in whatever language they choose.
- It doesn’t need a schema before starting. You can create the fields as you go.
- Every database will contain collections, with each collection housing documents. Each document can have fields with varying sizes and different content.
- It provides quicker query responses.
- MongoDB provides advanced searching.
- The database features indexing to improve search query performance.
- MongoDB provides data replication to send it to multiple nodes. Both primary and secondary nodes can replicate data.
- It supports advanced features for searching any field, range of queries, or regular expression.
- MongoDB provides the oplog (operations log) feature. This is a system that collects and stores all database changes. It keeps the changes chronologically and can help with deeper analysis since the oplog is entirely granular.
Many of these features point to a common theme, which is flexibility. When using SQL best practices, you must work within the database structure. There’s usually only one best way to do things. When using MongoDB, you’ll have several options for optimizing code throughout the process.
Is MongoDB NoSQL?
Yes, MongoDB is a type of NoSQL. MongoDB is a database management system that stores data using binary storage in flat files. This structure is helpful for large amounts of data since data storage is efficient and compact. It is document-based and open-sourced.
When using MongoDB, consider the following tips:
- The _id field must appear in every MongoDB document.
- Sharding is a way to distribute data through several partitions.
- There are size limits to keep in mind. When using MongoDB, you cannot exceed 16 MB for documents.
- There are limits on nested data. However, storing too many arbitrary objects when using MongoDB is usually not a good idea.
- Note that MongoDB restricts certain characters, including the $ sign and a period (.).
Like NoSQL, you’ll need to monitor MongoDB effectively. Several specific areas need monitoring:
- Instance Status
- Instance Hardware Metrics
- Replication Metrics
- Connections Metrics and Cluster Operations
What is the difference between SQL and NoSQL?
SQL is the acronym for Structured Query Language. As the most basic type of database management, SQL is a relational model that searches and retrieves information through different data, fields, and structures. Some of the most fundamental differences between SQL and NoSQL include:
- NoSQL uses dynamic schema for its unstructured data, while SQL uses queried language with a predefined schema.
- NoSQL databases are scalable horizontally, while SQL is scalable vertically.
- NoSQL has document, graph, key-value, or wide-column store databases, while SQL has table-based databases.
- NoSQL is better suited for unstructured data, while SQL will likely use multi-row transactions.
The bottom line
Each database has its merits, but when considering SQL vs. NoSQL, it’s important to remember a few key points. These include SQL being relational while NoSQL is non-relational, SQL databases generally scaling vertically, and NoSQL falling into four types of structures. When selecting from the NoSQL options, consider MongoDB an advanced database capable of handling dynamic schema and big data.
When evaluating NoSQL databases, consider factors such as scalability, consistency, and use case compatibility. Databases like MongoDB, Cassandra, and Redis provide powerful features designed to handle massive workloads and dynamic data models, making them essential for modern cloud-native applications.
Looking to optimize your data management strategy? Explore how LogicMonitor can help you monitor and manage your database infrastructure. Our comprehensive platform ensures visibility, performance, and reliability across all your IT environments.
If Artificial Intelligence is the ultimate multi-tool for IT operations (as discussed in our first article), then DevOps, Network Ops, Site Reliability Engineers (SREs), and SecOps are the teams using it. How each team uses AIOps’ capabilities will improve interconnectivity across an organization’s digital landscape, accelerate the production of high-priority business objectives, and reduce downtime to pave the way for a smoother developer and user experience.
Understanding the teams driving IT operations success
Before we map capabilities to teams, let’s establish some broad team definitions as they may currently exist within IT operations:
- DevOps: Ensure smooth collaboration between development and operations.
Priorities include automation, issue detection, and optimizing workflows to speed up software development and delivery.
- IT operations: Manage and maintain the organization’s IT infrastructure.
Priorities include improving operational efficiency, reducing downtime, and improving system reliability.
- Network operations: Manage and maintain the operation’s network infrastructure.
Priorities include identifying bottlenecks and predicting potential network issues.
- SRE: As an operational group, SREs own the back-end infrastructure responsible for the customer experience and consult with developer teams to ensure the infrastructure can support applications.
Priorities include avoiding downtime among revenue-critical systems, preventing bandwidth outages, and fixing configuration errors.
- Security operations: Protects the organization’s systems and data from security threats.
Priorities include security log analysis and response, as well as identifying anomalies or vulnerabilities.
Establishing a strong foundation: Key AIOps capabilities by team
AIOps uses artificial intelligence, machine learning, and consolidated operational platforms to automate repetitive or mundane tasks and streamline cross-team communications. An AIOps deployment is the scaffolding IT operations use to build evolving workflows so the teams can be more proactive, innovative, and able to accelerate the delivery of high-priority projects. That’s why we are seeing more AIOps success stories about how AIOps can liberate 40% of your engineering time through the automation of labor-intensive analysis or how Managed Service Providers (MSPs) are implementing AIOps’ intelligent alerting capabilities to dramatically reduce downtime.
So let’s dig into which three AIOps capabilities each team may leverage first:
DevOps
- Enhanced efficiency: Automating repetitive and manual tasks frees up time to focus on higher-value initiatives, increasing efficiency and productivity across the entire team.
- Faster mean time to resolution (MTTR): Streamlining incident management processes ensures faster issue identification, analysis, “next steps,” cross-team communications, and, ultimately, issue resolution. With automation doing the heavy lifting, these steps can happen outside of work hours. This 24/7 approach reduces the time to resolution, minimizing any impact on operations.
- Scalability and adaptability: AI and machine learning’s self-learning properties are made to handle complex and rapidly evolving technology stacks in dynamic environments.
Watch the 3-minute video below for more on how DevOps can use AIOps for faster issue resolution through integration with open-source provisioning and configuration management tools.
IT Operations
- Incident management: AIOps streamline incident identification and root cause analysis and escalate incidents to the right teams and people who can pinpoint the source of an issue and quickly fix it. Post-incident reviews are used to build resilience in systems to prevent future occurrences of similar incidents. Faster resolution reduces MTTR and operational impact.
- Scalability and adaptability: IT infrastructure has to adapt to business needs. AIOps systems handle the complexity of evolving modern stacks and dynamic environments, including hybrid and multi-cloud architectures. Faster scaling sets ITOps up for success in that they can effectively manage and monitor expanding IT landscapes at any stage of growth.
- Resource and cost optimization: Capacity planning and the automation of tasks lets ITOps teams allocate resources more efficiently, freeing up budget and personnel for new endeavors or headcount strategies.
Network Ops
- Streamlined troubleshooting: Automated root cause analysis capabilities quickly pinpoint the root causes of network issues, accelerating troubleshooting and improving uptime.
- Capacity planning: Historical and real-time data analysis on network use patterns, forecasted future demands, and resource allocation enables the team to reassign assets as needed to prevent network congestion and keep operations consistent while supporting business growth.
- Network security enhancement: Leveraging AI-driven algorithms that analyze network traffic, detect anomalies, and identify potential security threats enables Network Ops teams to take proactive measures ahead of a breach.
SRE
- Elasticity: As SRE teams manage complex and dynamic environments, including cloud-based systems and microservices architectures, AIOps provides the ability to scale and adapt to changing demands. AIOps ensures the SRE team can effectively monitor, manage, and optimize the system’s performance as it grows and evolves.
- Continuous optimization: AIOps analyzes data from various sources, including logs, metrics, and events, then identifies optimization opportunities that SRE teams can enact. Leveraging AI insights to make data-driven decisions, implement proactive measures, and continuously refine their infrastructure to achieve greater reliability.
- Collaboration and knowledge sharing: By providing a centralized platform for data collection, analysis, and visualization, AIOps facilitates communication and sharing of information so associated teams (such as developers) can align their efforts towards common goals, leading to improved teamwork and faster problem-solving.
SecOps
- Advanced threat detection: AIOps enhances threat detection capabilities by analyzing vast amounts of security-related data from various sources, such as logs, network traffic, and user behavior. AI-driven algorithms can identify patterns, anomalies, and potential security threats in real time, enabling SecOps teams to respond promptly to security incidents, minimizing damage caused by cyber threats.
- Threat intelligence integration: AIOps integrates with threat intelligence feeds and external security sources to enhance the effectiveness of security operations. By leveraging external threat intelligence data, AIOps enriches its analysis and detection capabilities, allowing SecOps teams to stay updated on the latest threats and attack vectors. This integration strengthens the overall security posture and enables proactive defense against emerging threats.
- Compliance and regulatory requirements: AIOps automate compliance monitoring and reporting processes and then compare them against predefined standards and regulations to evolve the automation and compliance process so teams consistently meet compliance and regulatory requirements.
Integrating AIOps for teams with existing tools
Seamless integration for unified operations
One of the standout advantages of AIOps is its ability to integrate with existing IT tools, providing a unified platform for monitoring, automation, and insights. Whether you’re leveraging monitoring tools like LogicMonitor, managing hybrid or multi-cloud environments, or maintaining CI/CD pipelines, AIOps can enhance and extend their functionality rather than replace them.
Compatibility with monitoring tools
AIOps platforms, such as LogicMonitor, act as a central hub, aggregating data from multiple monitoring tools to provide a unified view of IT operations. For example, integrating LogicMonitor with AIOps capabilities allows teams to consolidate alerts, correlate events, and automate responses—all from a single dashboard. This integration reduces manual intervention and provides actionable insights in real-time.
Enhancing cloud platforms
AIOps is designed to operate seamlessly in hybrid and multi-cloud environments. By analyzing data from cloud-native tools, AIOps systems provide predictive analytics, helping IT teams optimize workloads, prevent resource exhaustion, and identify anomalies before they escalate into problems.
Streamlining CI/CD pipelines
For DevOps teams, AIOps tools integrate with CI/CD platforms to enable continuous monitoring and intelligent automation throughout the development lifecycle. This ensures faster feedback loops, reduces downtime caused by deployment errors, and optimizes application performance.
Addressing legacy system concerns
One common concern when adopting AIOps is its compatibility with legacy systems. AIOps platforms are built with integration in mind, offering APIs and connectors that bridge the gap between older systems and modern tools. By applying machine learning to data generated by legacy tools, AIOps can derive valuable insights while extending the life of existing systems.
Laying the groundwork for success
To fully unlock the transformative potential of AIOps, organizations need to establish a strong foundation. These best practices ensure that teams can effectively leverage AIOps capabilities while minimizing disruptions and maximizing impact.
1. Prioritize data quality and accessibility
AIOps thrives on accurate and comprehensive data. Ensure all data sources—whether from legacy systems, monitoring tools, or cloud platforms—are clean, consistent, and consolidated. By breaking down data silos and standardizing formats, teams can enable AIOps to deliver actionable insights with precision.
2. Foster cross-team collaboration
AIOps works best when IT teams such as DevOps, Network Ops, and SREs collaborate seamlessly. Establish shared goals and encourage open communication to align team efforts. Unified dashboards, like those offered by LogicMonitor, help bridge gaps and provide everyone with a clear view of the operational landscape.
3. Start with targeted use cases
Rather than implementing AIOps broadly, begin with specific high-impact applications. Use cases such as automated incident management or anomaly detection are excellent starting points for demonstrating value and gaining stakeholder buy-in.
4. Balance automation with human oversight
While AIOps excels at automating repetitive tasks, human judgment remains critical for nuanced decision-making. Pair automated workflows with manual checks for complex scenarios to ensure both speed and accuracy in IT operations.
5. Commit to continuous improvement
AIOps systems evolve over time. Regularly monitor performance metrics, gather team feedback, and refine algorithms to adapt to changing environments. This iterative approach ensures long-term success and sustained benefits.
AIOps Use Cases
Here are some of the key use cases of AIOps in IT operations:
1. Identifying problems based on anomalies or deviations from normal behavior
AIOps enhances IT systems by using machine learning to detect anomalies and potential issues, unlike traditional tools that rely on manual configuration and threshold alerts. It analyzes data in real-time, flags deviations from normal behavior, and allows IT teams to address problems before they escalate.
2. Forecasting the value of a certain metric to prevent outages or downtime
AIOps forecasts crucial metrics like server capacity and network bandwidth, alerting IT teams before they reach critical levels. This proactive approach helps prevent outages and disruptions. By using machine learning algorithms, AIOps monitors data trends to predict threshold breaches, enabling preemptive actions to mitigate issues.
3. Improving incident response and resolution times
AIOps substantially improves incident response and resolution times by automatically correlating events from various sources and providing intelligent insights for root cause analysis. Machine learning algorithms effectively process large volumes of data from logs, alerts, and metrics to identify the root cause of incidents. This methodology not only expedites incident response but also reduces the mean time to resolution (MTTR), thereby minimizing the impact on business operations.
4. Enhancing IT operations through automation
AIOps presents substantial benefits by automating routine tasks and processes within IT operations, allowing IT teams to focus on higher-value activities such as strategic planning and problem-solving. This automation ranges from fundamental tasks like ticket routing and categorization to more complex processes such as incident remediation based on predefined rules. Consequently, it enhances efficiency, reduces the risk of human error, and streamlines workflows.
Take your IT operations to the next level
AIOps give teams the tools they need to transform from reactive to proactive. The combination of artificial intelligence and machine learning accelerates issue mitigation, breaks through work silos, improves systems security and scalability, increases productivity, reduces error risk and optimizes resources and costs. Having an AI-empowered IT operation means an organization’s infrastructure is instantly ready to handle roadblocks for a smoother developer and user experience.
LogicMonitor’s AIOps platform empowers businesses to transition from reactive troubleshooting to proactive, intelligent operations. With AI and machine learning capabilities, LogicMonitor provides meaningful alerts, illuminates patterns, and enables foresight and automation. Spend less time resolving issues and more time driving innovation.
LogicMonitor is proud to power the journey to AIOps by offering these free educational resources:
What is AIOps and How is it Changing IT Operations?
Simplify Troubleshooting with AIOps
Monitoring and Alerting Best Practices Guide
Sensirion Goes from 8 Monitoring Tools to Just One
Comprehensive AIOps for monitoring
Unlocking the Path to Automation with LogicMonitor
The art of monitoring the influence of an application’s performance on business outcomes is constantly evolving. It used to be directing IT teams to act on insights from an Application Performance Monitoring (APM) solution was enough to drive business outcomes. Now we know the user experience has a heavy hand in determining whether a digital platform survives or dies. An APM solution keeps tabs on the performance of application components such as servers, databases, and services. When it comes to monitoring user experience, Digital Experience Monitoring (DEM) is the key component organizations need to go a step further and really understand how users (human, machine, or digital) are interacting with their digital platforms.
So what is DEM exactly?
DEM is a practice within application performance management that focuses on monitoring and optimizing the overall user experience of digital apps and services. A DEM-enabled monitoring solution combines various techniques to gain insights into user behaviors, experience metrics (page load times, transaction responses, and error rates), application performance, network performance, and infrastructure performance. This allows organizations to proactively identify and address issues driving user satisfaction, improve the overall user experience, and positively drive business outcomes.
While DEM shares a connection with APM, it focuses more on the user’s perspective by tying performance metrics directly to user behaviors and experiences. DEM also complements observability practices by integrating telemetry data into user-centric insights, bridging the gap between technical performance and real-world user interactions.
Over time, DEM has evolved from basic performance monitoring to a sophisticated practice that combines real user monitoring, synthetic testing, and advanced analytics. This progression reflects the growing importance of delivering seamless digital experiences in increasingly complex environments.
Why does DEM matter?
As a monitoring capability, DEM is what mines and presents critical user patterns and trends to IT teams so they can collaboratively elevate their organization’s digital user experience from good to great. In many organizations, APM data gets splintered and analyzed through the lens of the team looking at it. Where DevOps teams are more likely to look at APM insights to keep tabs on application components and code-level performance, ITOps teams are more likely to pay attention to the data regarding broader infrastructure performance (servers, network devices, and databases). DEM provides unified insights from a variety of sources so both DevOps and ITOps get a unified look at the intertwined influences of user behavior, application performance, network metrics, and infrastructure data. This singular data set, coming directly from the users, gets IT teams out of their silos and at the whiteboard to collaborate on solutions.
Consider one scenario organizations will likely experience: a surge in CPU spikes on the servers. In the absence of DEM, DevOps and ITOps teams likely have separate insights into different application components and services, which limits their ability to troubleshoot the problem collaboratively. DEM bridges the gap between DevOps and ITOps, fostering a unified and cohesive approach to monitoring and optimizing the digital experience. It facilitates cross-functional collaboration, breaking down barriers that traditionally impede effective troubleshooting. By eliminating silos and promoting shared visibility, organizations can streamline incident response, reduce mean time to resolution (MTTR), and enhance the overall user experience.
How digital experience monitoring works
DEM works by leveraging a combination of monitoring techniques and technologies to capture, analyze, and interpret data related to user interactions with digital systems. The primary goal is to provide IT teams with actionable insights into how applications, networks, and infrastructure components impact the end-user experience. Here’s how it operates:
- Data collection: DEM solutions collect data from multiple sources, including real user monitoring (RUM), synthetic monitoring, application logs, and network performance metrics. This data spans application transactions, network latencies, server performance, and user interactions.
- Data correlation: Once collected, DEM correlates data points from these sources to build a cohesive picture of the end-to-end digital experience. For example, it links slow page load times with network bandwidth issues or high CPU usage on backend servers.
- Performance analysis: The solution uses advanced analytics and machine learning to identify patterns and anomalies. This enables IT teams to understand the root causes of performance bottlenecks, such as broken application dependencies or network congestion.
- Visualization of insights: DEM provides intuitive dashboards and reports that showcase user experience metrics, performance trends, and incident details. These visualizations are tailored to different teams, allowing DevOps to focus on application-level details while ITOps can monitor broader infrastructure health.
- Proactive alerting: By leveraging synthetic monitoring and threshold-based alerts, DEM identifies potential issues before they impact users. Simulated user journeys test critical workflows like logins or transactions, offering early warning signs of degradation.
- Collaboration enablement: DEM fosters cross-team collaboration by providing unified insights into user experience. Teams can access the same datasets, identify shared goals, and work cohesively to optimize performance and reduce mean time to resolution (MTTR).
By combining these operational mechanisms, DEM ensures organizations can maintain high-quality digital experiences for their users while proactively addressing performance challenges.
Components of digital experience monitoring
DEM is built on several key components that deliver a comprehensive view of the user experience. These components provide the data and insights necessary to monitor and optimize the performance of applications, networks, and infrastructure. Here are the essential building blocks of DEM:
- Real user monitoring (RUM):
RUM captures data from actual user interactions with an application or website in real time. It measures page load times, transaction durations, and error rates, offering insights into how users experience the platform. This component is invaluable for identifying pain points in the user journey and uncovering opportunities to enhance engagement. - Synthetic transaction monitoring:
Synthetic monitoring uses simulated user interactions to test critical workflows, such as logging into an account, completing a purchase, or searching for a product. By automating these tests, synthetic monitoring helps IT teams proactively detect issues like slow load times, failed transactions, or outages before they affect real users. - Endpoint monitoring:
Endpoint monitoring tracks the performance of devices and applications used by end users, such as desktops, laptops, and mobile devices. By analyzing factors like application responsiveness, network connectivity, and device health, this component ensures that user-side issues are addressed promptly, minimizing frustration and downtime. - Application performance monitoring (APM):
APM focuses on the performance of the application’s backend components, such as databases, APIs, and servers. It helps IT teams detect code-level issues, optimize application performance, and ensure smooth integration with other systems. - Network monitoring:
Since network performance directly affects the digital experience, DEM includes monitoring network metrics such as latency, bandwidth, and packet loss. This ensures that connectivity issues are identified and resolved to maintain seamless user interactions. - Session replay:
This component records and replays user sessions, allowing IT teams to see how users navigate and interact with digital platforms. Session replay is especially useful for diagnosing complex issues that require context beyond raw data points.
Why customer experience matters
Users don’t know which digital offerings use DEM to improve their experiences.
But they will ditch the ones that don’t.
Consider users in the e-commerce and digital retail space. DEM lets those platforms and websites monitor website performance, transaction times, and user interactions. If any of those experiences are suffering from downtime, disrupted transactions, or delayed user interactions, IT teams can use DEM analysis to identify the cause. They can then implement a solution and prevent a spike in cart abandonment rates while improving conversion rates and customer satisfaction ratings.
Let’s explore a second use case for Software-as-a-Service (SaaS) providers. DEM allows them to track user interactions, application response times, and errors to identify opportunities to enhance the customer experience and retain users (who hopefully tell their networks about the positive experience).
In both scenarios, integrating a DEM-enabled application monitoring solution would speed up the process of pinpointing the users’ pain points, diagnosing the root cause, and enabling IT teams to collaboratively solve the problem faster than they could without DEM insights.
Benefits of DEM
DEM-driven insights provide a variety of benefits to organizations looking for data-based strategies to help optimize their resources (both human and financial).
Enhanced user satisfaction
Organizations that monitor user experience metrics, such as page load times, transaction response times, and user interactions, can use this information to prioritize addressing the issues that have the most sway in user satisfaction. Proactively identifying and fixing those high-impact problems will result in higher engagement rates and increased customer loyalty.
Improved performance optimization
The holistic presentation of the end-to-end experience (application, network, and infrastructure performance) enables organizations to identify performance bottlenecks, diagnose issues, and prioritize areas for improvement faster than the competition ruled by an APM solution alone. Leveraging these insights lets IT teams optimize their applications and websites, resulting in faster load times, smoother interactions, and better overall performance.
Data-driven decision making
IT teams can know the solutions they are working on are backed by data that came from the users they are trying to impress. DEM helps developers uncover trends, patterns, and areas of improvement so those teams can prioritize resources to deliver an improved user experience effectively.
Drawbacks of DEM
Before investing, organizations need to consider some of the complexities they are signing up for when they deploy DEM capabilities in their monitoring solution.
Implementation complexity
For large or complex digital environments, integrating various monitoring techniques, tools, and systems may require upskilling or hiring the expertise needed for a successful implementation. In addition to configuring and fine-tuning the monitoring setup, ongoing maintenance and management of DEM can be a long-term investment.
Data volume challenges
DEM generates vast amounts of monitoring data, which can be overwhelming to process and analyze effectively. Organizations need to have robust data management and analysis capabilities already in place to sort through the onslaught of data, as well as a process in place for converting it into actionable insights for IT teams.
Resource considerations
Integrating and maintaining a DEM solution may require financial and resource investments ranging from procuring monitoring tools to hiring skilled personnel. Ongoing data analysis efforts may require long-term resource allocation.
Despite these drawbacks, many organizations will want to harness the benefits of DEM, as they outweigh the challenges.
Developing a digital experience monitoring strategy
Establishing an effective DEM strategy is essential for enhancing user satisfaction and business outcomes. A well-defined approach ensures that DEM integrates seamlessly with existing processes while delivering actionable insights. Here are the key steps to building a robust DEM strategy:
- Start with user-centric goals:
Define objectives that focus on improving the user experience. This includes reducing page load times, minimizing transaction errors, and ensuring seamless navigation. A user-centric approach aligns IT teams with what matters most—satisfaction and retention. - Leverage real-time analytics:
Enable real-time data collection and analysis to identify and resolve issues as they occur. This proactive monitoring approach minimizes downtime and ensures that problems are addressed before they impact users. - Integrate across tools and teams:
Ensure your DEM solution integrates with other monitoring tools, such as application performance monitoring (APM), network monitoring, and log management systems. This creates a unified view of the digital ecosystem, fostering cross-team collaboration between DevOps, ITOps, and other stakeholders. - Prioritize key metrics:
Identify and track metrics directly influencing the digital experience, such as transaction response times, error rates, and network latency. Tailor these metrics to your industry and use case to ensure relevance and accuracy. - Adopt synthetic monitoring:
Incorporate synthetic transaction monitoring to test critical workflows and identify issues before they reach end users. This proactive testing complements real user monitoring and strengthens overall system reliability. - Establish a feedback loop:
Create a process for continuously evaluating the effectiveness of your DEM strategy. Use insights from monitoring data to make iterative improvements, such as optimizing application code, upgrading network infrastructure, or refining user interfaces. - Communicate insights effectively:
Provide tailored dashboards and reports for different teams. For instance, technical teams may need granular data, while business teams benefit from high-level KPIs. Ensuring clarity in communication helps align efforts across the organization.
Not all DEM-enabled solutions are the same
Selecting the right APM is about more than the list of capabilities. The first consideration should be how a new DEM-enabled APM solution will complement any existing monitoring solutions.
Integration and compatibility
It is essential to evaluate how well the DEM-enabled APM solution integrates with your existing monitoring ecosystem. Consider whether it can seamlessly integrate with other monitoring tools and systems you rely on, such as application performance monitoring (APM) tools, log management, network monitoring, network performance diagnostics, or cloud monitoring platforms. Compatibility between the DEM-enabled APM solution and your existing infrastructure ensures smooth data aggregation, correlation, and analysis.
Scalability and flexibility
Consider whether the DEM-enabled APM solution can scale as your digital infrastructure grows and evolves. It should be able to handle increasing data volumes, monitor diverse applications and services, and adapt to changing technology stacks. Additionally, assess the flexibility of the solution in terms of customization and configuration to align with your specific monitoring requirements.
Context and correlation
An APM solution should provide DevOps and ITOps with context and correlation within observability platforms to manage application performance and gain digital experience insight across hybrid and multi-cloud environments to allow for cross-team collaboration. By proactively sharing those insights into the digital experience, both teams can own the solutions that enhance user satisfaction, increase productivity, and drive better business outcomes.
How LogicMonitor can help
If DEM is a measure of how much an organization values its users’ experiences, then LogicMonitor’s Application Performance Monitoring solution is how organizations show they’re serious about improving the processes and technologies that ensure their operations don’t just meet – but they exceed – users’ expectations.
OpenTelemetry integration monitors end-to-end application requests through distributed services in your existing environment.
Performance metrics capabilities can graph everything from high-level KPIs to granular technical metrics, visualizing business outcomes for the teams that need to deliver them.
Synthetic monitoring brings solution theories to life before users can test them in real time. This capability simulates end-user traffic through automated browser tests of user interactions or transactions, giving early insights into the quality of the end-user experience.
The collaboration challenges of remote work
A key conversation topic that repeatedly comes up with our customers is the challenge of collaboration in a remote work environment. Too many channels of communication or documentation are ineffective, and IT professionals are starting to feel fatigued by never feeling quite “in the know” about business decisions that are happening in real-time. Collaboration platforms such as MS Teams and Slack are intended to be solutions for these challenges, yet finding the right fit requires careful consideration. When separated from colleagues, teams can feel distant and unmotivated or find it hard to stay focused. Below, we have outlined Zoom vs. Slack vs. Teams, and some of the most common team collaboration tools teams use to communicate effectively and, ultimately, find balance in a work-from-home lifestyle.
Best online collaboration tools for IT teams
IT professionals have favorite collaboration tools, and recent data highlights their preferences. Each company tracks its statistics differently. While Microsoft hasn’t yet publicly disclosed the exact number of daily meetings conducted, Teams reports up to 5 billion meeting minutes in a single day. It remains a go-to platform for organizations already immersed in the Microsoft ecosystem. With its user-friendly interface and top-notch video quality, Zoom reports 300 million daily active users as of 2024, making it a favorite for virtual meetings. With its robust messaging capabilities and extensive integrations, Slack enjoys a more modest market share, with 32.3 million active users on average each day, catering to teams that prioritize real-time communication.
Unsurprisingly, many organizations mix and match these tools to fit their specific needs, using each where it works best to keep everything running smoothly and strengthen IT business continuity.
Microsoft Teams
Microsoft Teams was the most common response, but what is MS Teams? MS Teams is a chat-based collaboration tool that allows organizations to work together and share information in a common space. It’s part of Microsoft’s robust 365 product suite and offers a range of features that make it stand out for many users.
Public and private chat is a core feature, and with the absorption of Skype for Business, Teams offers integrated video capabilities, including popular social features like emojis and custom memes.
‘Hub’ is another important capability that offers a shared workspace for various Microsoft Office applications such as PowerPoint, Word, Excel, Planner, OneNote, SharePoint, and Power BI. Delve was once an integrated tool, but most of its features have been absorbed into Microsoft 365’s broader capabilities. Teams can remotely work together in one space without toggling between applications.
The users of Microsoft Teams that we polled recognized the ability to share documents across multiple locations and chat across multiple offices as the tool’s most widely used application. They also acknowledged the options for screen sharing or whiteboards.
Video conferencing and online meetings can include anyone outside or inside a business and are also important features of the tool. However, many offices use online video calling and screen sharing internally, as well as other tools, such as Zoom, for externally facing meetings.
As IT organizations implement a collaboration tool like MS Teams, the ability to deliver monitoring alerts directly into the MS Teams chat is a common need (LogicMonitor can utilize the Microsoft Teams API to deliver alerts via a custom HTTP integration). Monitoring user activity, quality of calls, private messages, team messages, and types of devices is also important.
Looking ahead, LogicMonitor will take a more cloud-based approach to monitoring MS Teams to pull important data, such as call quality metrics. Stay up to date by subscribing to our release notes.
At the end of the day, if a company uses Microsoft 365, MS Teams is probably a good collaboration solution. It is included for free with Office 365 and can be easily accessed through 365’s centralized management console.
Microsoft Teams vs. Zoom
Zoom remains one of the most commonly used video conferencing tools, valued for its ease of use, reliable video quality, and popularity in externally facing communication. While both Zoom and Microsoft Teams enable video conferencing, private and public chat, virtual meeting spaces, screen sharing, and file sharing, Microsoft Teams stands out as part of the Microsoft 365 suite and continues to expand its capabilities with AI-powered tools like Microsoft Copilot. This makes Teams a one-stop shop for organizations already using Microsoft’s tools, though it may be less accessible to participants outside the organization than Zoom’s simpler setup process.
Both platforms have made significant advancements in security. Microsoft Teams provides end-to-end encryption for data in transit and at rest, along with multi-factor authentication and Rights Management Services to safeguard sensitive information. Zoom has introduced robust security measures, including end-to-end encryption for meetings, enhanced data privacy controls, and user-friendly security dashboards. Its refined two-factor authentication (2FA) provides flexibility, allowing users to verify identities through authentication apps or SMS codes while ensuring alternative available methods if needed.
Both Microsoft Teams and Zoom offer free versions with optional paid upgrades at competitive per-user rates. The choice between the two ultimately depends on your organization’s specific needs. Many businesses find value in using both tools—leveraging MS Teams internally for collaboration and Zoom externally for virtual meetings. Their integration capabilities further enhance workflow efficiencies, ensuring teams can use the right tool for every scenario.
LogicMonitor offers out-of-the-box monitoring for Zoom to further optimize your collaboration tools, compatible with any Zoom account. Learn more about our Zoom monitoring.
Microsoft Teams vs. Slack
Slack is a fun and easy-to-use chat and channel-based messaging platform developed by Salesforce. Slack shines with its bot and app integrations, improving the user’s workplace experience. Onboarding is easy, and there are shortcuts and productivity hacks for just about anything. In terms of features, both MS Teams and Slack are fairly evenly matched. Both offer private and public chat, searchable message history, screen sharing, file sharing, and fun integrations to generate gifs and memes. Both offer free versions of their platform, with upgraded features and integrations on paid plans.
MS Teams beats Slack when it comes to online audio and video sharing and also wins out where security and compliance are of concern. Not only does Microsoft’s data encryption and compliance come into play, but the admin controls are more extensive than any other platform.
We recently updated our Slack integration, and it’s now bidirectional.
Zoom vs. Slack
Slack and Zoom are both cloud-based collaboration tools. Slack excels at team messaging and integrations, while Zoom specializes in high-quality video conferencing. Each platform caters to distinct communication needs, making them suited for different teams and projects.
Slack is a powerhouse for team messaging and integrations, offering robust real-time communication. It organizes conversations into channels, simplifying collaboration on specific projects. While its video calls are limited in functionality and best suited for smaller team discussions, Slack excels in messaging-based capabilities. It also supports integrations with third-party tools like Google Drive. Features such as pinned messages, customizable notifications, and emoji reactions enhance its usability for day-to-day collaboration.
Zoom specializes in high-quality video conferencing, offering a smooth, reliable experience for any size group. Its key features include HD video and audio, breakout rooms, virtual backgrounds, and whiteboard functionality. These capabilities make Zoom a go-to for presentations, team meetings, and webinars. While Zoom has a functional chat feature, Slack’s is more robust.
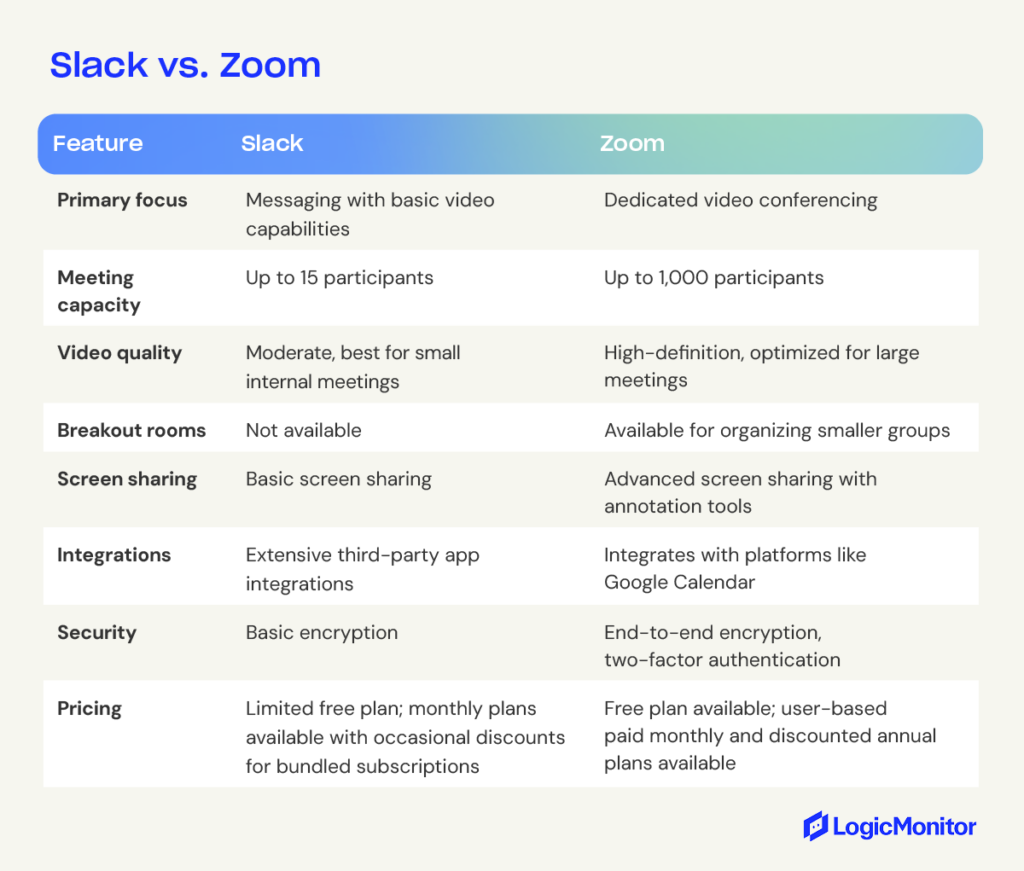
For many organizations, Zoom complements messaging platforms like Slack to create a complete collaboration suite. Teams might use Slack for daily messaging and collaboration while relying on Zoom for high-quality virtual meetings. Both platforms offer free versions, making evaluating their fit for your team’s needs easy.
Other collaboration tools to consider
Google Workspace has its own collaboration tool, Google Meet. In the same way that MS Teams is available right from 365, Google Meet is available to any business or individual with Gmail or a Workspace account. However, some features, such as recording meetings or exceeding the 60-minute mark, are reserved for paid plans. If your business already has Google Workspace, Google Meet is a great solution; some find it slightly easier to use than MS Teams.
Cisco Webex is also a leader in online meetings and video conferencing solutions. It has features similar to MS Teams, Google Meet, and Zoom, such as one-to-one or group conferencing, file sharing, and a vast library of integrations. The security features are robust, and there are a variety of protection tools to keep data safe. Learn more about LogicMonitor’s Webex monitoring capabilities.
Trello, Asana, and Monday are all popular project management applications most commonly used in marketing, customer support, sales, and HR. They allow teams to create, track, and manage complex workflows in a centralized hub and are often used in tandem with some of the video, chat, and file-sharing tools discussed above.
Using more than one collaboration tool
Work environments have changed dramatically in recent years. As organizations rely more on remote and hybrid work environments, it makes sense for them to take advantage of multiple collaboration tools to meet diverse needs.
Different platforms excel in specific areas, offering distinct advantages that make them ideal for certain workflows. For example, many teams use Slack for internal messaging and quick collaboration paired with Zoom for virtual meetings, then turn to Google Workspace for email, calendar management, and file sharing. This multi-tool approach provides teams with IT resources to tackle various aspects of their work seamlessly. Discover how LogicMonitor supports remote monitoring to enhance IT workflows.
LogicMonitor embraces this strategy by utilizing Slack for internal chat. We rely on Google Workspace for scheduling and document sharing, while preferring Zoom for internal and external video calls. This combination lets teams leverage the strengths of each platform, staying productive and maintaining a collaborative culture without compromise.
Choosing the right combination depends on your organization’s size, budget, and specific requirements. By exploring different tools and identifying the best fit for your workflows, you can empower your teams to stay connected and productive. Explore integrations with LogicMonitor to enhance your collaboration stack and support your business needs.
How to maximize value with Jira and AWS Lambda integration
One of our engineers on the TechOps team coined the term “Value++.” It references the shorthand operator for “increment” in various coding languages. It is also a motto for what we should be doing as a team—always adding value.
Here are a few things in our day-to-day operations that have been a serious “value –”
- Answering JIRA tickets that have no description
- “Customer has issue B,” but both the customer name and issue details are omitted from that sentence
- Doing things manually, over and over again
At LogicMonitor, most of the tasks requested of the TechOps team come in the form of JIRA tickets. A new application may be ready for deployment, or a customer account may require a rename. We also have to deal with operational tasks like moving new customer accounts from demo to production environments.
Because LogicMonitor is rapidly growing, we always try to be more efficient by automating ourselves out of work. We decided to automate parts of our DevOps tasks through AWS Lambda functions, API calls, and JIRA tickets. This allows the team to keep track of existing tasks that show up in our queue and spend their time doing more important things.
It’s “Value ++.”
Understanding projects and issue types for automation
We first had to lock down specific JIRA projects and issue types to differentiate tasks from other items, creating a separate issue type for every task we wanted to automate. This makes things easy to organize and allows us to lock down who can or cannot make specific tickets.
In this blog, we’ll go over one of our simpler use cases: automatically performing an account rename.
Streamlining workflows with straightforward solutions: The simple stupid
This crude Lucidchart (below) shows the basics of what we did. Every 5 minutes, a CloudWatch Event rule triggers a Lambda function. The function will make a JIRA API call to retrieve a list of tickets. Using those tickets, we will grab the necessary information and make subsequent API calls to backend services within LogicMonitor to perform specific actions, such as renames. Lambda will also actively update and close the tickets upon task completion. The first thing we need to do is know what tickets to look for.
Executing JQL queries directly from AWS Lambda
JIRA Query Language (JQL) is one of the most flexible ways to search for issues in JIRA. We use a JQL query with the JIRA REST API to find specific open tickets with issue types of “account rename.” This should return a list of associated tickets.
endpoint = "https://jira_url/rest/api"
jql_issuetype = "issuetype='Account Rename'"
jql_project = "project='TechOps Request'"
status = "status=Open"
jql = ("jql=" + jql_project +
"+AND+" + jql_issuetype +
"+AND+" + status
)
r = session.get(endpoint + "/2/search?" + jql % locals(), headers=headers_jira)
response = json.loads(r.text)
for issues in response["issues"]:
customer = issues["fields"]["customfield_10001"]
target_name = issues["fields"]["customfield_14673"]
Taking the list of open tickets, we need to be able to glean important information out of them, some of them in the form of custom fields.
Customizing workflows with Jira’s custom fields
Users create custom fields, which are not by default available in JIRA. For our specific use case, we created a few fields, such as customer name, target name, and rename date. From the code example above, you can see that within the JIRA API, you can not specify just the field’s name; you’ll need to add a customfield_id.
Pro tip:
If you don’t want to look at a page of ugly JSON, you can also use the advanced JIRA search bar and type in the field’s name.
Embracing event-driven automation with AWS Lambda… most of the time
Usually, when we build apps on Lambda, we have components like Lambda functions and event sources. An event source is an AWS service that publishes events for processing by code within a Lambda function. In this case, performing a rename upon JIRA ticket creation could have been handled with a post function and an API Gateway. However, customers have their own maintenance windows and preferred times for an account rename to happen. Sometimes, customers may want their account renamed on Saturday at 4 a.m. during my personal maintenance (sleep) window. As a workaround, we decided to use a CloudWatch event as a lambda scheduler.
today = datetime.datetime.today() - datetime.timedelta(hours=7)
desired_date = datetime.datetime.strptime(issues["fields"]["customfield_16105"].replace("-0700",""), "%Y-%m-%dT%H:%M:%S.%f")
if today > desired_date:
create_rename(customer, target_name)
Our CloudWatch event would run every 5 minutes, triggering our Lambda function. The function will first check if the current time exceeds the value we parsed from the custom field rename date (see code above), and then we will allow the function to continue.
Combining tools to create seamless automation
At this point, we have collected the information we need. We can perform the rename by making API calls to the backend LogicMonitor services, but we won’t show that code in this blog. However, we also want to treat the JIRA ticket as a state file. We don’t want to keep grabbing the same open tickets repeatedly. This is where we want to use another JIRA API call to move the ticket to a different workflow step (e.g., from “Open” to “In Progress”). However, just like custom fields, we need a specific transition id, which you can find by editing your existing project workflow. We can now update the status of our JIRA ticket programmatically:
def changeStatus(key, id):
jira_request = {"transition":{"id": id }, "fields": {"resolution": {"name": "Done"}}}
endpoint = "https://jira_url.com/rest/api"
r = session.post(endpoint + "/2/issue/%(key)s/transitions?expand=transitions.fields" % locals(), data=json.dumps(jira_request), headers=headers_jira)
return r.text
Reducing human errors through intelligent automation: Saving people from people
Customer renames for the team used to be an extremely arduous task. Looking back at the Confluence revision history for our account rename runbook is akin to cleaning out your basement after 20 years. Besides being extremely time-consuming, the process involved halting puppets and, for unknown reasons, executing both a Ruby and a Bash script simultaneously. Sometimes, an application restart was required, but it was not always. As we grow, the only scalable solution is to automate repetitive, manual, and often mind-boggling tasks. It allows us to provide better service for customers and allows us to bypass the mundane to embrace the innovative.
One last tip—and this is the most important part—when we want to automate anything that requires manual input from other people, we have to take human stupidity… uh… error into consideration. Make sure to create validators and conditionals to combat this.
Plus, witty warning messages are a “value++.”
For IT teams, the signal-to-noise ratio isn’t just a technical inconvenience—it’s the tipping point between operational success and systemic failure in today’s modern enterprises.
At the Gartner IT Infrastructure, Operations & Cloud Strategies (IOCS) Conference 2024, this critical issue took center stage. Two sessions presented by LogicMonitor leaders showcased how we’re pioneering the convergence of hybrid observability and next-generation AIOp—a transformative approach that’s redefining how organizations manage their infrastructure today.
LogicMonitor’s Edwin AI represents the evolution of traditional AIOps into the next generation. Unlike traditional AIOps which typically focus on basic monitoring and correlation tasks, next-gen AIOps adds sophisticated AI capabilities, predictive elements, and cross-domain analysis to deliver more proactive and comprehensive infrastructure management. Combining the power of generative AI with hybrid observability, Edwin AI demonstrates the tangible benefits of integrating next-gen AIOps into real-world operations, from reducing alert fatigue to enabling predictive incident management.
3 key takeaways from Gartner IOCS 2024:
- Hybrid observability has become indispensable as organizations operate across cloud, on-premises, and edge environments. With infrastructure spread across so many environments, comprehensive visibility is crucial for effective performance, security, and incident management.
- Generative AI is transforming IT operations at scale by delivering intelligent alert correlation, automated root cause analysis, and predictive incident management in plain language summaries which in turn takes the cognitive load off IT teams and allows them to focus on strategic responses rather than interpretation.
- LogicMonitor’s Edwin AI exemplifies next-gen AIOps innovation, especially how hybrid observability and AI-driven insights can converge to deliver autonomous IT operations.
Hybrid observability is the key to success in AI era
A key theme at Gartner IOCS centered on the growing complexity of IT environments and how organizations are adapting their observability strategies. As confidence in traditional IT delivery models declines, enterprises are shifting toward approaches that balance legacy systems with innovation demands.
The adoption of hybrid cloud architectures—combining on-premises, multi-cloud and hybrid cloud environments—has become mainstream, driven by varying requirements for performance, security, and cost optimization. While organizations have long struggled with data sprawl and tool fragmentation, these challenges become more pronounced in hybrid environments where teams must manage disconnected monitoring tools and siloed data across different infrastructure types, hampering effective incident response and decision-making.
Hybrid observability platforms have emerged as a crucial solution for managing this complexity by providing unified visibility across the distributed environments (including on-prem, IaaS, PaaS, SaaS, and containerized workloads). These platforms enable organizations to move from reactive to proactive operations by combining comprehensive data collection, intelligent anomaly detection and automation to enhance performance and reduce downtime.
Success stories like Topgolf, which consolidated ten separate tools into a single platform, demonstrate the tangible benefits of this approach—improved observability capabilities, enhanced user experience, and comprehensive technical visibility.
It’s also important to note that different industries have distinct cloud requirements driven by their specific regulatory, operational, and technical needs. For example, heavily regulated sectors like financial services and healthcare often maintain certain workloads on-premises or in private clouds to ensure compliance with data sovereignty requirements and maintain direct control over sensitive data.. Biotech companies may require on-premises or specialized cloud environments to handle compute-intensive workloads and protect intellectual property.
This diversity of needs underscores the importance of observability platforms that can provide consistent visibility regardless of where workloads run—whether on-premises, in private clouds, or across multiple public clouds. These platforms must be able to integrate with existing tools and workflows while providing contextualized insights that account for industry-specific compliance requirements and operational priorities..
The key takeaway was unambiguous: As IT becomes more complex, organizations need an observability platform that can understand, contextualize, and manage infrastructure effectively across all environments to succeed in today’s AI-driven world.

Next-gen AIOps is reshaping enterprise observability
In another notable session, leaders addressed another critical challenge: the overwhelming volume of alerts IT teams face daily. The numbers paint a stark picture of current challenges: IT teams spend 4-5 hours resolving each critical incident while wasting 30% of their time on non-critical alerts. Even more concerning, 70% of troubleshooting data remains unused.
Traditional alert management systems are falling short, creating fragmented insights and alert fatigue that lead to team burnout and delayed incident response. However, next-gen AIOps solutions are showing promising results. Organizations implementing AI-driven solutions report reducing alert noise by 80%, helping teams focus on truly critical issues.
The fusion of AI with modern observability platforms is paving the way for more autonomous IT operations through:
- Self-healing systems that automate common fixes
- Predictive analysis that spots problems before they impact services
- Unified visibility that helps teams quickly understand complex issues
The session highlighted Edwin AI as a prime example of this evolution. The solution uses advanced AI to analyze data from multiple monitoring systems, precisely locate errors, intelligently group related incidents, automate complex data analysis, and more. With an 80% reduction in alert volume, a 30% faster mean time to resolution (MTTR), and a 20% decrease in manual effort, the solution empowers IT teams to focus on critical issues, resolve them faster, and streamline routine tasks, all while minimizing future disruptions.
Together with the earlier insights on hybrid observability, it’s clear that AI-powered tools and comprehensive observability across hybrid environments aren’t just the future of IT operations—they’re essential right now. The challenges of modern IT demand immediate action, and these solutions are already transforming how organizations operate.

We are in an AI era; it’s time to embrace smarter IT operations.
Gartner IOCS 2024 highlighted a pivotal shift in IT operations, one that LogicMonitor is at the forefront of driving. The future lies in intelligent, AI-powered observability.
LogicMonitors’s Edwin AI exemplifies how generative AI and next-gen AIOps are shaping enterprise IT operations. By integrating advanced AI with hybrid observability across hybrid environments, Edwin AI is transforming how organizations resolve incidents, reduce alert fatigue, and automate complex analysis. For businesses ready to embrace this evolution, the path to more proactive, efficient, and autonomous IT operations is clear.
At LogicMonitor, we’re not just adapting to these changes; we’re leading the way. By empowering teams with modern solutions and AI-driven insights, we’re setting the stage for a new era of IT management—one where operational complexity is minimized, and smarter decision-making is the norm.



