IT automation uses software and technology to handle repetitive IT tasks automatically, reducing the need for manual work and accelerating processes like infrastructure management and application deployment. This transformation is essential for IT teams needing to scale efficiently, as seen in the case of Sogeti, a Managed Service Provider (MSP) that provides tech and engineering resources worldwide.
Sogeti had a crucial IT challenge to solve. The MSP operates in more than 100 locations globally and uses six different monitoring tools to monitor its customers’ environments. It was a classic example of tool sprawl and needing to scale where multiple teams of engineers relied on too many disparate tools to manage their customers’ environments. It soon became too arduous for the service provider to collect, integrate, and analyze the data from those tools.
Sogeti had teams of technicians managing different technologies, and they all existed in silos. But what if there was a way to combine those resources?
IT automation provided a solution.
After working with LogicMonitor, Sogeti replaced the bulk of its repeatable internal processes with automated systems and sequences. The result? Now, they could continue to scale their business with a view of those processes from a single pane of glass.
Conundrum cracked.
That’s just one example of how IT automation tools completely revolutionizes how an IT services company like an MSP or DevOps vendor can better execute its day-to-day responsibilities.
By automating repeatable, manual processes, IT enterprises streamline even the most complicated workflows, tasks, and batch processes. No human intervention is required. All it takes is the right tech to do it so IT teams can focus on more strategic, high-priority efforts.
But what exactly is IT automation? How does it work? What are the different types? Why should IT companies even care?
IT automation, explained
IT automation is the creation of repeated software processes to reduce or eliminate manual or human-initiated IT tasks. It allows IT companies with MSPs, DevOps teams, and ITOps teams to automate jobs, save time, and free up resources.
IT automation takes many forms but almost always involves software that triggers a repeated sequence of events to solve common business problems—for example, automating a file transfer. It moves from one system to another without human intervention or autogenerates network performance reports.
Almost all medium and large-sized IT-focused organizations use some automation to facilitate system and software processes, and smaller companies benefit from this tech, too. The most successful ones invest heavily in the latest tools and tech to automate an incredible range of tasks and processes to scale their business.
The production, agricultural, and manufacturing sectors were the first industries to adopt IT automation. However, this technology has since extended to niches such as healthcare, finance, retail, marketing, services, and more. Now, IT-orientated companies like MSPs and enterprise vendors can incorporate automation into their workflows and grow their businesses exponentially.
How does IT automation work?
The software does all the hard work. Clever programs automate tasks that humans lack the time or resources to complete themselves.
Developers code these programs to execute a sequence of instructions that trigger specific events from specific operating systems at specific times. For example, programming software so customer data from a customer relationship management system (CRM) generates a report every morning at 9 a.m. Users of those programs can then customize instructions based on their business requirements.
With so many benefits of IT automation, it’s no wonder that two-thirds of CFOs plan to accelerate the automation of repetitive tasks within their companies.
Why do businesses use IT automation?
IT-focused businesses use automation for various reasons:
- It makes life easier for tech teams. For example, engineers and technicians at MSP companies no longer have to execute tasks like network performance analysis, data security management, or reporting manually. The software takes care of everything for them so they can better focus their efforts on other tasks.
- It makes life easier for non-tech teams. Employees across all departments within an IT-focused organization benefit from automation because they can carry out responsibilities on software and systems with less manual work. For example, administrative employees in a DevOps consulting firm can generate payroll reports without manually entering information into a computer by hand.
- It helps CIOs and executives scale their businesses because other employees, such as engineers and MSP professionals, can complete jobs with minimum effort. Automation frees up tech resources and removes as much manual IT work as possible, allowing IT-centered organizations to improve their margins and grow.
- It helps CIOs and executives fulfill client-orientated objectives by improving service delivery. Automation can also advance productivity across an organization, which results in better service level agreement (SLA) outcomes. Again, the right automation software reduces as much manual work for tech teams so businesses can grow and carry out responsibilities more efficiently.
- It allows MSPs and other IT companies, especially smaller ones, to survive in ever-competitive environments. By automating IT processes, these enterprises can stay competitive with more tech resources and reduced manual labor.
- It allows for improved profitability in IT companies. For example, MSPs can onboard more clients without hiring new engineers. That’s because automated systems delegate tasks and resources seamlessly.
- It reduces costs for IT companies by saving time and improving operational efficiencies. For example, by freeing up human resources, enterprises can focus on generating more sales and revenue. As a result, CIOs and executives have more money to spend on labor and can add highly skilled IT professionals to their tech teams.
Key benefits of IT automation
IT automation delivers many advantages that extend beyond simple task delegation. Let’s look at a few benefits your organization will see.
Enhanced organizational efficiency
With the complexity of modern IT infrastructure, modern environments may handle thousands of requests daily—everything from password resets to system failures. Automation can help reduce the time it takes to handle many of those requests. For example, look at an IT telecommunications company with a lot of infrastructure. They can automate their network configuration process, cutting the deployment time from a few weeks to less than a day.
Reduce errors
Human error in IT environments can be costly. Errors can lead to unexpected system downtime, security breaches, and data entry errors—all of which you can avoid by standardizing consistency and standards through automation. Automation helps your team eliminate routine data entry and other tasks and greatly reduces the chance of human error. For example, your team may decide to create backup scripts for more complicated setups to ensure you always have reliable backups.
Faster service delivery
Automation helps speed up responses to common IT requests. If your IT team is stuck needing to perform every task manually, it increases incident response time and the length of time your customer waits on the other end of the line for a fix. Automation speeds up common tasks—setting up VPN access, account resets, report creation, and security scans—allowing your team to focus on finding the root cause of problems, deploying resources, and bringing systems back online.
Streamlined resource allocation
Your organization’s IT needs may fluctuate depending on how many users you have and their activities. A strict guide for resource usage may result in some users being unable to work efficiently because of slow systems. Automation can help by automating resource allocation. For cloud services, you can scale your servers based on demand, and for network traffic, you can dynamically adjust traffic routes based on usage.
Enhanced compliance and security
Automated systems can help your team maintain detailed audit trails and enforce consistent security policies. They can also help with continuous monitoring, allowing your team to get alerts immediately when your solution detects suspicious activity. Additionally, your IT systems can automatically generate compliance reports, such as SOC 2, for review, helping your team find potential problems and comply with audit requests.
Different IT automation types
IT companies benefit from various types of IT automation.
Artificial intelligence
A branch of computer science concerned with developing machines that automate repeatable processes across industries. In an IT-specific context, artificial intelligence (AI) automates repetitive jobs for engineers and IT staff, reduces the human error associated with manual labor, and allows companies to carry out tasks 24 hours a day.
Machine learning
Machine learning (ML) is a type of AI that uses algorithms and statistics to find real-time trends in data. This intelligence proves valuable for MSPs, DevOps, and ITOps companies. Employees can stay agile and discover context-specific patterns over a wide range of IT environments while significantly reducing the need for case-by-case investigations.
Robot process automation
Robot Process Automation (RPA) is a technology that instructs ‘robots’ (machines) to emulate various human actions. Although less common in IT environments than in AI and ML, RPA still provides value for MSPs and other professionals. For example, enterprises can use RPA to manage servers, data centers, and other physical infrastructure.
Infrastructure automation
IT infrastructure automation involves using tools and scripts to manage computing resource provisioning with manual intervention. This includes tasks like server provisioning, bandwidth management, and storage allocation. This allows for dynamic resource usage, with the most resources going to the users and applications with the most need.
How can businesses use IT automation?
A proper automation strategy is critical for IT companies. CIOs and executives should decide how to achieve automation within their organizations and then choose the right tools and technologies that facilitate these objectives.
Doing so will benefit your business in many ways.
- Improve your company’s operation by removing redundant tasks and freeing up time to work on more mission-critical jobs
- Enhance customer satisfaction by more quickly responding and resolving problems
- Improve employee satisfaction by making sure business systems stay online, helping meet their expectations and improving their ability to do their jobs
Here are some examples of how IT companies use automation:
Templating/blueprints
Companies can automate templates and blueprints, promoting the successful rollout of services such as network security and data center administration.
Workflow/technology integration
Automation allows companies to integrate technology with workflows. As a result, CIOs and executives complete day-to-day tasks more effectively with the latest hardware and software. For example, automating server management to improve service level management workflows proves useful if clients expect a particular amount of uptime from an MSP.
AI/ML integration
AI and ML might be hard for some companies to grasp at first. However, teams can learn these technologies over time and eventually combine them for even more effective automation within their organizations.
Auto-discovery
Automated applications like the LogicMonitor Collector, which runs on Linux or Windows servers within an organization’s infrastructure, use monitoring protocols to track processes without manual configuration. Users discover network changes and network asset changes automatically.
Auto-scaling
IT companies can monitor components like device clusters or a VM in a public cloud and scale resources up or down as necessary.
Automated remediation/problem resolution
Hardware and software can provide companies like MSPs with all kinds of problems (downtime, system errors, security vulnerabilities, alert storms, etc.). Automation, however, identifies and resolves infrastructure and system issues with little or no human effort.
Performance monitoring and reporting
Automation can automatically generate regular performance reports, SLA reports, compliance reports, and capacity planning forecasts. It can also generate automated alerting systems in case of problems and report trends to help your business with capacity planning.
Best practices for automation success
Successfully automating IT in business requires careful planning and thoughtful execution. Follow these best practices to avoid the common mistakes and maximize efficiency:
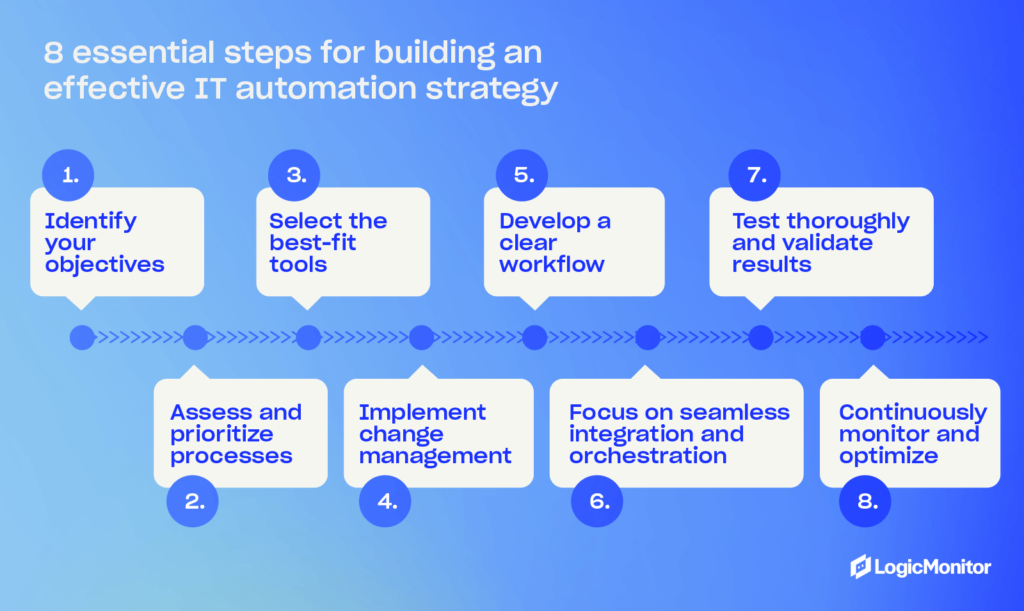
- Align automation and business goals: Don’t just start automating everything possible without a plan. Begin by identifying what you want to achieve with automation. Look for areas to reduce operational costs, improve service, and enhance customer satisfaction, and start with the areas that have the most impact and help you reach your goals. Consider asking stakeholders and employees about their biggest friction points and the ability to automate them.
- Start small: Investing in IT automation is an ongoing task, and you may not do things right the first time. Start small with quick wins. Learn what works for your business and pilot your initial automation tasks to test how they work. Eventually, begin scaling as you gain insights from smaller projects to inform larger, more impactful ones.
- Focus on security: Although your team may not be working with data manually as much, security is still a must with IT automation. Integrate secure protocols at every layer of your systems and processes. Look at your regulatory requirements to determine your needs, and regularly audit your systems to identify potential weaknesses.
- Document everything: If things go wrong, you need detailed records about your automation process. Create documents that detail every system, automation tools and scripts that belong to those systems, and common troubleshooting tips for quickly dealing with problems. Make documentation available to team members so all your team members can look up how things work and manage their designated automation systems.
- Monitor performance: Establish metrics that indicate the success of your automation efforts. Look for improvements in uptime, response time, and other performance data. Regularly look for areas that don’t meet your performance metrics and investigate areas of improvement.
IT Automation Pros and Cons
Here are some pros and cons of automation for those working in IT:
Pros
- Enhanced productivity (improved workflows, higher production rates, better use of technologies and human resources, freeing up IT resources, etc.).
- Better customer/client outcomes (improved SLAs, faster and more consistent services, higher-quality outputs, enhanced business relationships, etc.).
- Reduced total cost of ownership (auto-discovery tools prevent expensive errors, freeing up labor resources, automatic discovery of cost-cutting technologies, etc.).
Cons
- Automation requires an initial cost investment and engineers’ time to set up. That’s why IT-focused companies should choose a cost-effective automation platform that generates an ongoing return on investment.
- Some team members may find it difficult to adopt automation technologies. The best course of action is to select a simplified automation tool.
- Automation may amplify security issues. Software and configuration vulnerabilities can quickly spread in your organization before being detected, which means security considerations and testing must be done before introducing automation.
Read more: The Leading Hybrid Observability Powered by AI Platform for MSPs
Will IT automation replace jobs?
There’s a misconception that IT automation will cause job losses. While this might prove true for some sectors, such as manufacturing, IT-focused companies have little to worry about. That’s because automation tools don’t work in silos. Skilled IT professionals need to customize automation tools based on organizational requirements and client demands. MSPs that use ML, for example, need to define and determine the algorithms that identify real-time trends in data. ML models might generate data trends automatically, but MSPs still need to select the data sets that feed those models.
Even if automation takes over the responsibilities of a specific team member within an IT organization, executives can upskill or reskill that employee instead of replacing them. According to LogicMonitor’s Future of the MSP Industry Research Report, 95% of MSP leaders agree that automation is the key to helping businesses achieve strategic goals and innovation. By training employees who currently carry out manual tasks, executives can develop a stronger, higher-skilled workforce that still benefits from IT automation.
Future of IT automation
AI, machine learning, and cloud computing advancements are significantly altering how businesses manage their IT infrastructure. As these technologies continue to evolve, how you manage your business will change along with them.
Here’s what to expect in the future of IT automation:
Intelligent automation
Traditional automation tools use a rules-based approach: a certain event (e.g., time of day, hardware failure, log events) triggers an action through the automation systems.
Advanced AI operations tools are changing that with their ability to predict future events based on data. That leads to more intelligent automation that doesn’t require a rules-based system. These systems understand natural language, recognize patterns, and make decisions based on real-time data. They allow for more responsive IT systems that anticipate and fix problems.
Hybrid cloud automation
The growing adoption of cloud environments—which include private, public, and on-prem resources—requires your business to adopt new strategies to manage infrastructure and automate tasks. You need tools that seamlessly integrate with all environments to ensure performance and compliance where the data resides.
Hybrid environments also allow for more flexibility and scalability for IT infrastructure. Instead of being limited by physical constraints, your business can use the cloud to scale computing resources as much as needed. Automated provisioning and deployment means you can do this at scale with minimal IT resources.
Edge computing automation
As workforces and companies become more distributed, your business needs a way to provide resources to customers and employees in different regions. This may mean a web service for customers or a way for employees to access business services.
Edge devices can help supply resources. Automation will help your business manage edge devices, process data on the edge, and ensure you offer performant applications to customers and employees who need them.
Choosing the right IT automation platform
Successful data-driven IT teams require technology that scales as their business does, providing CIOs and executives with ongoing value. LogicMonitor is the world’s only cloud-based hybrid infrastructure monitoring platform that automates tasks for IT service companies like MSPs.
LogicMonitor features include:
- An all-in-one monitoring platform that revolutionizes digital transformation for MSPs and DevOps/ITOps teams worldwide.
- Complete 360-degree visibility of utilization, network performance, resource consumption, cloud instances, and much more.
- Full observability of technologies and resources such as servers, data centers, and cloud-based environments.
- The ability to identify problems with legacy tools before they happen.
- Real-time reports and forecasts that reduce internal costs, improve SLA outcomes, and power engineers and other IT professionals.
- No additional hardware maintenance or technical resources. LogicMonitor is ready out of the box.
Final Word
IT automation has revolutionized the IT sector, reducing the manual responsibilities that, for years, have plagued this industry. MSPs no longer need to enter network performance data into multiple systems, physically inspect servers, manage and provision networks manually, analyze performance reports, or perform other redundant tasks manually. Automation does a lot of the hard work so that these IT professionals can focus on far more critical tasks. By incorporating cloud-based infrastructure monitoring, AI, machine learning, and other new technologies, your IT executives improve productivity, enhance workflows, reduce IT resources, promote better client outcomes, and reduce costs over time.
Application Performance Monitoring (APM) and Application Performance Management (APM) play critical roles in not only identifying and resolving performance bottlenecks but also in driving broader IT goals such as scalability, user satisfaction, and operational efficiency. By providing granular insights and a strategic approach, these practices empower teams to maintain high-performing applications and deliver exceptional digital experiences.
What is application performance management?
Application performance management refers to the broader view into how an application is using resources and how that allotment influences the user experience. (We discussed why it’s important to have a Digital Experience Monitoring (DEM)-enabled APM in this article).
By focusing on end-user satisfaction, APM empowers ITOps teams to prioritize performance enhancements that align with business objectives, such as reducing latency, improving scalability, and delivering a seamless digital experience.
What is application performance monitoring?
Imagine an athlete preparing for a baseball game. The athlete’s training routine and performance data (ex: batting average) can be likened to application performance monitoring. The athlete’s overall approach to managing their performance to achieving optimal results (ex: attending every team practice, analyzing then buying better equipment) can be likened to application performance management.
Application performance monitoring refers to the granular understanding of the products providing a detailed analysis of the performance, optimization, and reliability of an application’s infrastructure and components. Closely monitoring the functionality of each step and transaction of the application stack makes it easier for organizations to debug and improve the application. In the event of an application crash or failure, data provided by application performance monitoring allows ITOps teams to quickly pinpoint the source and resolve the issue.
Three Key Differences Between APM v APM
| Functionality/Feature | Application Performance Monitoring | Application Performance Management |
| Scope of Problem Analysis | Code-level: Focus on code-level problems within a specific application. Focuses on monitoring individual steps. May lack scalability for enterprise-wide application monitoring. | Broad: Focuses on individual steps from an end-user perspective. Offers insights into which applications require optimization then helps with those efforts. May be less effective for managing performance across a large number of applications simultaneously. |
| Data Collection | Collects time-oriented data, analyzing each step in a sequential manner. Beneficial for debugging code-level errors and identifying application-specific issues. | Collects a broad range of data with emphasis on user interaction with the system. Beneficial insights (ex: memory usage and CPU consumption) help identify root causes impacting end-users. |
| Performance Criteria Considerations | More focused on the performance of individual applications. Example: criteria such as time thresholds to determine if the application meets end goal requirements. | More focused on real-user monitoring, directly correlating with the end-user experience. Example: Analyzes overall user experience and resource utilization for specific applications to enhance the end-user experience. |
Application performance management use cases
Organizations use APM to know what is going on with resource consumption at the hardware, network, and software levels. This data helps ITOps teams improve resource allocation which helps reduce costs, improve scalability, and enhance overall performance.
Here are some other use cases for application performance management:
Business transaction analysis organizations use APM to monitor and analyze the end-to-end journey of a business transaction within the application. APM gives insight into the different transactions’ interactions with components and systems to help ITOps teams identify any sources of performance bottlenecks.
Root cause analysis of performance issues or failures within an application environment is correlated through data from different monitoring sources, such as logs, metrics, and traces. When the exact source of the performance problem is found, troubleshooting and resolution happens faster, and downtime is reduced or avoided.
Compliance and regulatory requirements for software application performance are more easily met when APM is monitoring and documenting them. Organizations can rely on APM to fill the critical role of providing an audit trail and documentation of their adherence to industry standards and regulations.
SLA management with APM allows organizations to monitor, measure and report on agreed-upon key performance metrics and levels against predefined SLA targets. This data is then used for SLA reporting and compliance.
Application Performance Monitoring use cases
Organizations can leverage APM to gain data-based visibility into the sources of bottlenecks, latency issues, and resource constraints within the infrastructure. APM’s data on response time, CPU usage, memory consumption, and network latency help pinpoint the root causes of application performance degradation.
Here are some other use cases for application performance monitoring:
Proactive issue detection uses APM to set up thresholds and alerts for key performance indicators such as slowing response times, spiking error rates, and other anomalies which can produce a negative digital user experience.
Capacity planning uses APM to focus on CPU usage, memory use, and disk I/O of applications. This data shows where infrastructure resources need to scale or be redistributed to prevent performance issues.
User experience monitoring tracks user interactions, session durations, and conversion rates to identify areas where improvements to the infrastructure can enhance the user experience.
Code-level performance analysis uses APM to profile code execution. This data empowers developers with the information needed to identify and diagnose performance bottlenecks (i.e. slower response times or high resource usage) within the application code.
Service level agreements (SLA) compliance and reporting tracks and alerts anomalies in uptime, response time, and error rates. This level of monitoring helps teams stay in compliance with identified SLA targets. APM is also used to produce compliance reports for stakeholders.
When organizations leverage APM, they gain deep visibility into their application infrastructure, enabling proactive monitoring, real-time diagnostics, and ultimately drive business success.
Application performance management and monitoring in cloud-native environments
Cloud-native and hybrid IT setups bring a new level of complexity to application performance. These environments often rely on microservices architectures and containerized applications, which introduce unique challenges for both monitoring and management.
Application architecture discovery and modeling
Before you can effectively use APM tools, it is crucial to have a clear understanding of your application’s architecture. This includes identifying all application components, such as microservices, containers, virtual machines, and infrastructure components like databases and data centers.
Once all components are identified, creating a dependency map can help visualize the interactions and dependencies between them.
Application performance management in cloud-native setups
Application performance management takes a broader approach by optimizing resource allocation and ensuring seamless interactions between microservices. In serverless environments, APM tools help teams allocate resources efficiently and monitor functions’ performance at scale. This holistic perspective allows IT teams to anticipate and resolve issues that could degrade the end-user experience across complex, distributed systems.
Application performance monitoring in cloud-native setups
Application performance monitoring focuses on tracking the health and performance of individual containers and microservices. Tools designed for cloud-native environments, such as those compatible with Kubernetes, provide detailed insights into metrics like container uptime, resource consumption, and service response times. By closely monitoring these components, IT teams can quickly identify and address issues that could impact the overall application.
Cloud-native environments demand a unified strategy where monitoring tools offer granular insights, and management practices align these insights with broader operational goals. This synergy ensures consistent application performance, even in the most dynamic IT ecosystems.
Application monitoring vs infrastructure monitoring
While application monitoring and infrastructure monitoring share the common goal of maintaining optimal IT performance, they differ significantly in focus and scope. Application monitoring is primarily concerned with tracking the performance, reliability, and user experience of individual applications. It involves analyzing metrics such as response times, error rates, and transaction durations to ensure that applications meet performance expectations and provide a seamless user experience.
Infrastructure monitoring, on the other hand, takes a broader approach by focusing on the health and performance of the underlying systems, including servers, networks, and storage. Metrics like CPU usage, memory consumption, disk I/O, and network throughput are key indicators in infrastructure monitoring, providing insights into the stability and efficiency of the environment that supports applications.
Both types of monitoring are essential for maintaining a robust IT ecosystem. Application monitoring ensures that end-users can interact with applications smoothly, while infrastructure monitoring ensures that the foundational systems remain stable and capable of supporting those applications. By combining both approaches, IT teams gain comprehensive visibility into their environments, enabling them to proactively address issues, optimize resources, and deliver consistent performance.
This cohesive strategy empowers organizations to align application and infrastructure health with business objectives, ultimately driving better user satisfaction and operational efficiency.
Best practices for implementing application performance management and monitoring
To get the most out of application performance monitoring (APM) and application performance management (APM), it’s crucial to adopt effective practices that align with your organization’s goals and infrastructure. Here are some best practices to ensure successful implementation:
- Set realistic thresholds and alerts
- Establish performance benchmarks tailored to your application’s typical behavior.
- Use monitoring tools to set dynamic alerts for critical metrics like response times, error rates, and resource utilization, avoiding alert fatigue.
- Focus on end-user experience
- Prioritize metrics that directly impact user satisfaction, such as page load times or session stability.
- Use management tools to allocate resources where they will enhance end-user interactions.
- Align management goals with business objectives
- Collaborate with business stakeholders to identify key performance indicators (KPIs) that matter most to your organization.
- Ensure monitoring and management efforts support broader goals like reducing downtime, optimizing costs, or meeting SLA commitments.
- Leverage data for continuous improvement
- Regularly analyze performance data to identify trends, recurring issues, and areas for optimization.
- Integrate findings into your development and operational workflows for ongoing enhancement.
- Incorporate AIOps and automation
- Use artificial intelligence for IT operations (AIOps) to detect patterns, predict anomalies, and automate incident responses.
- Streamline routine management tasks to focus on higher-value activities.
- Plan for cloud-native complexity
- Adopt tools that support microservices and containerized environments, ensuring visibility across dynamic infrastructures.
- Monitor both individual service components and their interactions within the broader application ecosystem.
- Document and share insights
- Maintain clear documentation of performance monitoring solution thresholds, resource allocation strategies, and incident resolutions.
- Share these insights with cross-functional teams to promote collaboration and alignment.
Drive application performance with LogicMonitor
While use cases vary between application performance monitoring and application performance management, they share a common goal: ensuring applications run efficiently and effectively. Application performance monitoring excels at providing detailed data feedback to proactively identify and resolve performance issues, while application performance management emphasizes broader strategies to align processes and people for sustained application success.
Together, these approaches form a comprehensive performance strategy that enhances both the user and developer experience. By leveraging both techniques, organizations can optimize their applications to meet business objectives and exceed user expectations.
Ready to elevate your application performance strategy? LogicMonitor’s APM solutions provide powerful insights by unifying metrics, traces, and logs into a single platform. With features like distributed tracing, push metrics API, and synthetics testing, LM APM enables faster troubleshooting, enhanced visibility, and superior end-user experiences.
Amazon Web Services (AWS) Kinesis is a cloud-based service that can fully manage large distributed data streams in real-time. This serverless data service captures, processes, and stores large amounts of data. It is a functional and secure global cloud platform with millions of customers from nearly every industry. Companies from Comcast to the Hearst Corporation are using AWS Kinesis.
What is AWS Kinesis?
AWS Kinesis is a real-time data streaming platform that enables businesses to collect, process, and analyze vast amounts of data from multiple sources. As a fully managed, serverless service, Kinesis allows organizations to build scalable and secure data pipelines for a variety of use cases, from video streaming to advanced analytics.
The platform comprises four key components, each tailored to specific needs: Kinesis Data Streams, for real-time ingestion and custom processing; Kinesis Data Firehose, for automated data delivery and transformation; Kinesis Video Streams, for secure video data streaming; and Kinesis Data Analytics, for real-time data analysis and actionable insights. Together, these services empower users to handle complex data workflows with efficiency and precision.
To help you quickly understand the core functionality and applications of each component, the following table provides a side-by-side comparison of AWS Kinesis services:
| Feature | Video streams | Data firehose | Data streams | Data analytics |
| What it does | Streams video securely for storage, playback, and analytics | Automates data delivery, transformation, and compression | Ingests and processes real-time data with low latency and scalability | Provides real-time data transformation and actionable insights |
| How it works | Uses AWS Management Console for setup; streams video securely with WebRTC and APIs | Connects to AWS and external destinations; transforms data into formats like Parquet and JSON | Utilizes shards for data partitioning and storage; integrates with AWS services like Lambda and EMR | Uses open-source tools like Apache Flink for real-time data streaming and advanced processing |
| Key use cases | Smart homes, surveillance, real-time video analytics for AI/ML | Log archiving, IoT data ingestion, analytics pipelines | Application log monitoring, gaming analytics, web clickstreams | Fraud detection, anomaly detection, real-time dashboards, and streaming ETL workflows |
How AWS Kinesis works
AWS Kinesis operates as a real-time data streaming platform designed to handle massive amounts of data from various sources. The process begins with data producers—applications, IoT devices, or servers—sending data to Kinesis. Depending on the chosen service, Kinesis captures, processes, and routes the data in real time.
For example, Kinesis Data Streams breaks data into smaller units called shards, which ensure scalability and low-latency ingestion. Kinesis Firehose, on the other hand, automatically processes and delivers data to destinations like Amazon S3 or Redshift, transforming and compressing it along the way.
Users can access Kinesis through the AWS Management Console, SDKs, or APIs, enabling them to configure pipelines, monitor performance, and integrate with other AWS services. Kinesis supports seamless integration with AWS Glue, Lambda, and CloudWatch, making it a powerful tool for building end-to-end data workflows. Its serverless architecture eliminates the need to manage infrastructure, allowing businesses to focus on extracting insights and building data-driven applications.
Security
Security is a top priority for AWS, and Kinesis strengthens this by providing encryption both at rest and in transit, along with role-based access control to ensure data privacy. Furthermore, users can enhance security by enabling VPC endpoints when accessing Kinesis from within their virtual private cloud.
Kinesis offers robust features, including automatic scaling, which dynamically adjusts resources based on data volume to minimize costs and ensure high availability. Furthermore, it supports enhanced fan-out for real-time streaming applications, providing low latency and high throughput.
Video Streams
What it is:
Amazon Video Streams offers users an easy method to stream video from various connected devices to AWS. Whether it’s machine learning, playback, or analytics, Video Streams will automatically scale the infrastructure from streaming data and then encrypt, store, and index the video data. This enables live, on-demand viewing. The process allows integrations with libraries such as OpenCV, TensorFlow, and Apache MxNet.
How it works:
The Amazon Video Streams starts with the use of the AWS Management Console. After installing Kinesis Video Streams on a device, users can stream media to AWS for analytics, playback, and storage. The Video Streams features a specific platform for streaming video from devices with cameras to Amazon Web Services. This includes internet video streaming or storing security footage. This platform also offers WebRTC support and connecting devices that use the Application Programming Interface.
Data consumers:
MxNet, HLS-based media playback, Amazon SageMaker, Amazon Rekognition
Benefits:
- There are no minimum fees or upfront commitments.
- Users only pay for what they use.
- Users can stream video from literally millions of different devices.
- Users can build video-enabled apps with real-time computer-assisted vision capabilities.
- Users can playback recorded and live video streams.
- Users can extract images for machine learning applications.
- Users can enjoy searchable and durable storage.
- There is no infrastructure to manage.
Use cases:
- Users can engage in peer-to-peer media streaming.
- Users can engage in video chat, video processing, and video-related AI/ML.
- Smart homes can use Video Streams to stream live audio and video from devices such as baby monitors, doorbells, and various home surveillance systems.
- Users can enjoy real-time interaction when talking with a person at the door.
- Users can control, from their mobile phones, a robot vacuum.
- Secure Video Streams provides access to streams using Access Management (IAM) and AWS Identity.
- City governments can use Video Streams to securely store and analyze large amounts of video data from cameras at traffic lights and other public venues.
- An Amber Alert system is a specific example of using Video Streams.
- Industrial uses include using Video Streams to collect time-coded data such as LIDAR and RADAR signals.
- Video Streams are also helpful for extracting and analyzing data from various industrial equipment and using it for predictive maintenance and even predicting the lifetime of a particular part.
Data firehose
What it is:
Data Firehose is a service that can extract, capture, transform, and deliver streaming data to analytic services and data lakes. Data Firehose can take raw streaming data and convert it into various formats, including Apache Parquet. Users can select a destination, create a delivery stream, and start streaming in real-time in only a few steps.
How it works:
Data Firehose allows users to connect with potentially dozens of fully integrated AWS services and streaming destinations. The Firehose is basically a steady stream of all of a user’s available data and can deliver data constantly as updated data comes in. The amount of data coming through may increase substantially or just trickle through. All data continues to make its way through, crunching until it’s ready for visualizing, graphing, or publishing. Data Firehose loads data onto Amazon Web Services while transforming the data into Cloud services that are basically in use for analytical purposes.
Data consumers:
Consumers include Splunk, MongoDB, Amazon Redshift, Amazon Elasticsearch, Amazon S3, and generic HTTP endpoints.
Benefits:
- Users can pay as they go and only pay for the data they transmit.
- Data Firehose offers easy launch and configurations.
- Users can convert data into specific formats for analysis without processing pipelines.
- The user can specify the size of a batch and control the speed for uploading data.
- After launching, the delivery streams provide elastic scaling.
- Firehose can support data formats like Apache ORC and Apache Parquet.
- Before storing, Firehose can convert data formats from JSON to ORC formats or Parquet. This saves on analytics and storage costs.
- Users can deliver their partitioned data to S3 using dynamically defined or static keys. Data Firehose will group data by different keys.
- Data Firehose automatically applies various functions to all input data records and loads transformed data to each destination.
- Data Firehose gives users the option to encrypt data automatically after uploading. Users can specifically appoint an AWS Key Management encryption key.
- Data Firehose features a variety of metrics that are found through the console and Amazon CloudWatch. Users can implement these metrics to monitor their delivery streams and modify destinations.
Use cases:
- Users can build machine learning streaming applications. This can help users predict inference endpoints and analyze data.
- Data Firehose provides support for a variety of data destinations. A few it currently supports include Amazon Redshift, Amazon S3, MongoDB, Splunk, Amazon OpenSearch Service, and HTTP endpoints.
- Users can monitor network security with Event Management (SIEM) tools and supported Security Information.
- Firehose supports compression algorithms such as Zip, Snappy, GZip, and Hadoop-Compatible Snappy.
- Users can monitor in real-time IoT analytics.
- Users can create Clickstream sessions and create log analytics solutions.
- Firehose provides several security features.
Data streams
What it is:
Data Streams is a real-time streaming service that provides durability and scalability and can continuously capture gigabytes from hundreds of thousands of different sources. Users can collect log events from their servers and various mobile deployments. This particular platform puts a strong emphasis on security. Data streams allow users to encrypt sensitive data with AWS KMS master keys and a server-side encryption system. With the Kinesis Producer Library, users can easily create Data Streams.
How it works:
Users can create Kinesis Data Streams applications and other types of data processing applications with Data Streams. Users can also send their processed records to dashboards and then use them when generating alerts, changing advertising strategies, and changing pricing.
Data consumers:
Amazon EC2, Amazon EMR, AWS Lambda, and Kinesis Data Analytics
Benefits:
- Data Streams provide real-time data aggregation after loading the aggregate data into a map-reduce cluster or data warehouse.
- Kinesis Data Streams feature a delay time between when records are put in the stream and when users can retrieve them, which is approximately less than a second.
- Data Streams applications can consume data from the stream almost instantly after adding the data.
- Data Streams allow users to scale up or down, so users never lose any data before expiration.
- The Client Library supports fault-tolerant data consumption and offers support for scaling support Data Streams applications.
Use cases:
- Data Streams can work with IT infrastructure log data, market data feeds, web clickstream data, application logs, and social media.
- Data Streams provides application logs and a push system that features processing in only seconds. This also prevents losing log data even if the application or front-end server fails.
- Users don’t batch data on servers before submitting it for intake. This accelerates the data intake.
- Users don’t have to wait to receive batches of data but can work on metrics and application logs as the data is streaming in.
- Users can analyze site usability engagement while multiple Data Streams applications run parallel.
- Gaming companies can feed data into their gaming platform.
Data analytics
What it is:
Data Analytics provides open-source libraries such as AWS service integrations, AWS SDK, Apache Beam, Apache Zeppelin, and Apache Flink. It’s for transforming and analyzing streaming data in real time.
How it works:
Its primary function is to serve as a tracking and analytics platform. It can specifically set up goals, run fast analyses, add tracking codes to various sites, and track events. It’s important to distinguish Data Analytics from Data Studio. Data Studio can access a lot of the same data as Data Analytics but displays site traffic in different ways. Data Studio can help users share their data with others who are perhaps less technical and don’t understand analytics well.
Data consumers:
Results are sent to a Lambda function, Kinesis Data Firehose delivery stream, or another Kinesis stream.
Benefits:
- Users can deliver their streaming data in a matter of seconds. They can develop applications that deliver the data to a variety of services.
- Users can enjoy advanced integration capabilities that include over 10 Apache Flink connectors and even the ability to put together custom integrations.
- With just a few lines of code, users can modify integration abilities and provide advanced functionality.
- With Apache Flink primitives, users can build integrations that enable reading and writing from sockets, directories, files, or various other sources from the internet.
Use cases:
- Data Analytics is compatible with the AWS Glue Schema Registry. It’s serverless and lets users control and validate streaming data while using Apache Avro schemes. This is at no additional charge.
- Data Analytics features APIs in Python, SQL, Scala, and Java. These offer specialization for various use cases, such as streaming ETL, stateful event processing, and real-time analytics.
- Users can deliver data to the following and implement Data Analytics libraries for Amazon Simple Storage Service, Amazon OpenSearch Service, Amazon DynamoDB, AWS Glue Schema Registry, Amazon CloudWatch, and Amazon Managed Streaming for Apache Kafka.
- Users can enjoy “Exactly Once Processing.” This involves using Apache Flink to build applications in which processed records affect results. Even if there are disruptions, such as internal service maintenance, the data will still process without any duplicate data.
- Users can also integrate with the AWS Glue Data Catalog store. This allows users to search multiple AWS datasets
- Data Analytics provides the schema editor to find and edit input data structure. The system will recognize standard data formats like CSV and JSON automatically. The editor is easy to use, infers the data structure, and aids users in further refinement.
- Data Analytics can integrate with both Amazon Kinesis Data Firehose and Data Streams. Pointing data analytics at the input stream will cause it to automatically read, parse, and make the data available for processing.
- Data Analytics allows for advanced processing functions that include top-K analysis and anomaly detection on the streaming data.
AWS Kinesis vs. Apache Kafka
In data streaming solutions, AWS Kinesis and Apache Kafka are top contenders, valued for their strong real-time data processing capabilities. Choosing the right solution can be challenging, especially for newcomers. In this section, we will dive deep into the features and functionalities of both AWS Kinesis and Apache Kafka to help you make an informed decision.
Operation
AWS Kinesis, a fully managed service by Amazon Web Services, lets users collect, process, and analyze real-time streaming data at scale. It includes Kinesis Data Streams, Kinesis Data Firehose, and Kinesis Data Analytics. Conversely, Apache Kafka, an open-source distributed streaming platform, is built for real-time data pipelines and streaming applications, offering a highly available and scalable messaging infrastructure for efficiently handling large real-time data volumes.
Architecture
AWS Kinesis and Apache Kafka differ in architecture. Kinesis is a managed service with AWS handling the infrastructure, while Kafka requires users to set up and maintain their own clusters.
Kinesis Data Streams segments data into multiple streams via sharding, allowing each shard to process data independently. This supports horizontal scaling by adding shards to handle more data. Kinesis Data Firehose efficiently delivers streaming data to destinations like Amazon S3 or Redshift. Meanwhile, Kinesis Data Analytics offers real-time data analysis using SQL queries.
Kafka functions on a publish-subscribe model, whereby producers send records to topics, and consumers retrieve them. It utilizes a partitioning strategy, similar to sharding in Kinesis, to distribute data across multiple brokers, thereby enhancing scalability and fault tolerance.
What are the main differences between data firehose and data streams?
One of the primary differences is in each building’s architecture. For example, data enters through Kinesis Data Streams, which is, at the most basic level, a group of shards. Each shard has its own sequence of data records. Firehose delivery stream assists in IT automation, by sending data to specific destinations such as S3, Redshift, or Splunk.
The primary objectives between the two are also different. Data Streams is basically a low latency service and ingesting at scale. Firehose is generally a data transfer and loading service. Data Firehose is constantly loading data to the destinations users choose, while Streams generally ingests and stores the data for processing. Firehose will store data for analytics while Streams builds customized, real-time applications.
Detailed comparisons: Data Streams vs. Firehose
AWS Kinesis Data Streams and Kinesis Data Firehose are designed for different data streaming needs, with key architectural differences. Data Streams uses shards to ingest, store, and process data in real time, providing fine-grained control over scaling and latency. This makes it ideal for low-latency use cases, such as application log processing or real-time analytics. In contrast, Firehose automates data delivery to destinations like Amazon S3, Redshift, or Elasticsearch, handling data transformation and compression without requiring the user to manage shards or infrastructure.
While Data Streams is suited for scenarios that demand custom processing logic and real-time data applications, Firehose is best for bulk data delivery and analytics workflows. For example, Firehose is often used for IoT data ingestion or log file archiving, where data needs to be transformed and loaded into a storage or analytics service. Data Streams, on the other hand, supports applications that need immediate data access, such as monitoring dashboards or gaming platform analytics. Together, these services offer flexibility depending on your real-time streaming and processing needs.
Why choose LogicMonitor?
LogicMonitor provides advanced monitoring for AWS Kinesis, enabling IT teams to track critical metrics and optimize real-time data streams. By integrating seamlessly with AWS and CloudWatch APIs, LogicMonitor offers out-of-the-box LogicModules to monitor essential performance metrics, including throughput, shard utilization, error rates, and latency. These metrics are easily accessible through customizable dashboards, providing a unified view of infrastructure performance.
With LogicMonitor, IT teams can troubleshoot issues quickly by identifying anomalies in metrics like latency and error rates. Shard utilization insights allow for dynamic scaling, optimizing resource allocation and reducing costs. Additionally, proactive alerts ensure that potential issues are addressed before they impact operations, keeping data pipelines running smoothly.
By correlating Kinesis metrics with data from on-premises and other cloud performance services, LogicMonitor delivers holistic observability. This comprehensive view enables IT teams to maintain efficient, reliable, and scalable Kinesis deployments, ensuring seamless real-time data streaming and analytics.
The scene is familiar to any IT operations professional: the dreaded 3 AM call, multiple monitoring tools showing conflicting status indicators, and teams pointing fingers instead of solving problems. For managed service providers (MSPs) supporting hundreds or thousands of customers, this challenge multiplies exponentially. But at AWS re:Invent 2024, Synoptek’s team revealed how they’ve fundamentally transformed this reality for their 1,200+ customer base through AI-powered observability.
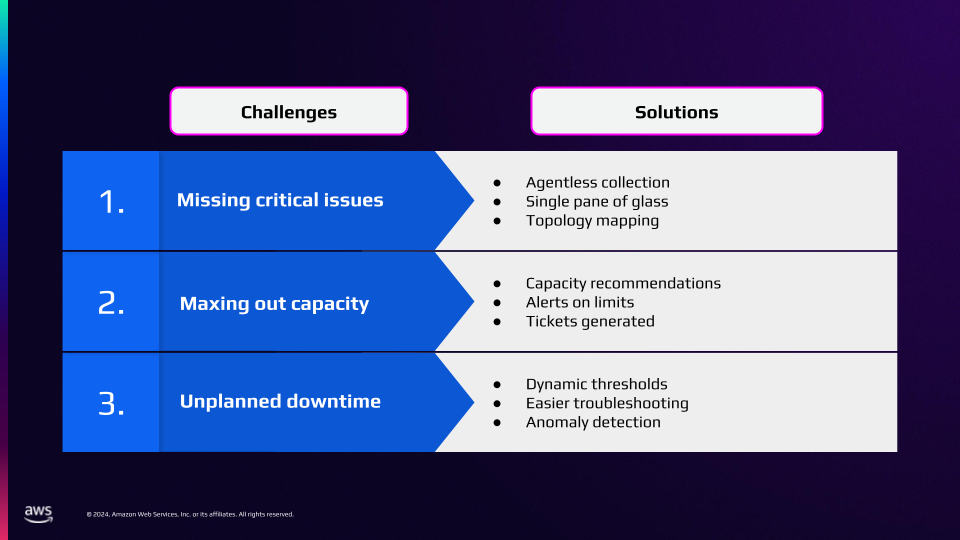
The true cost of tool sprawl: When more tools mean more problems
“In the before times, our enterprise operations center was watching six different tools looking for alerts and anomalies,” shares Mike Hashemi, Systems Integration Engineer at Synoptek.
This admission resonates with MSPs worldwide, where operating with multiple disparate tools has become an accepted, if painful, norm.
The true cost of this approach extends far beyond simple tool licensing. Neetin Pandya, Director of Cloud Operations at Synoptek, paints a stark picture of the operational burden: “If we have more than thousand plus customers, then we need one or two engineers with the same skill set into different shifts…three engineers for a single tool, every time.” This multiplication of specialized staff across three shifts creates an unsustainable operational model, both financially and practically.
The complexity doesn’t end with staffing. Each monitoring tool brings its own training requirements, maintenance overhead, and integration challenges.
Case in point: when different tools show conflicting statuses for the same device, engineers waste precious time simply verifying if alerts are real instead of solving actual problems. This tool sprawl creates a perfect storm of increased response times, decreased service quality, and frustrated customers.
Breaking free from traditional constraints
Synoptek’s transformation began with a fundamental shift in their monitoring approach. Rather than managing multiple agent-based tools, they moved to an agentless architecture that could monitor anything generating data, regardless of its location or connection method.
Hashemi shares a powerful example: “We had a device that was not network connected. But it was connected to a Raspberry Pi via serial cable…they realized that they had to watch that separate from the monitoring system. And they said, ‘Hey, can we get this in there?’ And I said, ‘yeah, absolutely, no problem.'”
This flexibility with LogicMonitor’s hybrid observability powered by AI platform, LM Envision, proves crucial for MSPs who need to support diverse client environments and unique monitoring requirements. But the real breakthrough came with the implementation of dynamic thresholds and AI-powered analysis.
Traditional static thresholds, while simple to understand, create a constant stream of false positives that overwhelm operations teams. “If a server CPU spikes up for one minute, drops back down, it’s one CPU in a cluster… you’re going to get an alert, but who cares? The cluster was fine,” Hashemi explains. The shift to dynamic thresholds that understand normal behavior patterns has dramatically reduced this noise.
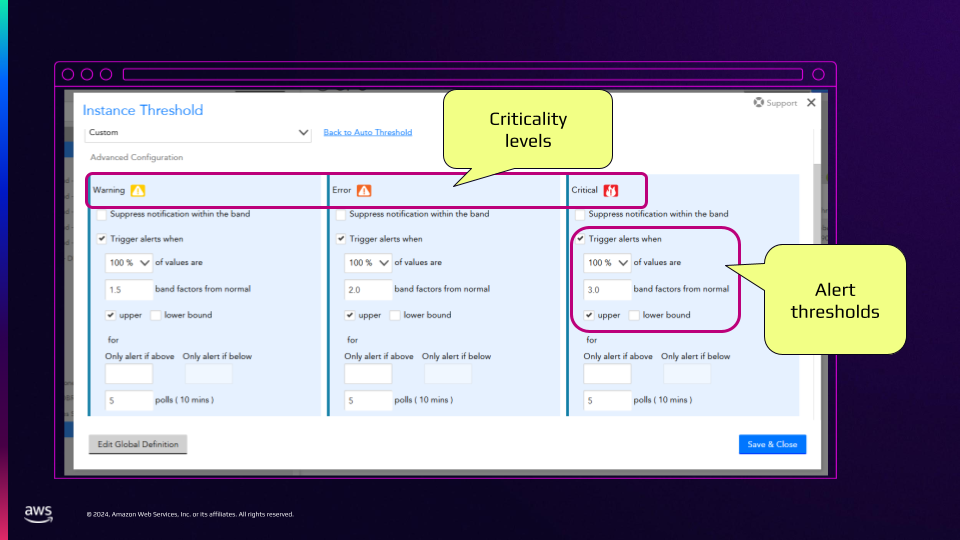
The cost optimization breakthrough
Perhaps the most compelling aspect of Synoptek’s transformation emerged in an unexpected area: cloud cost optimization. Pandya describes a common scenario that plagues many organizations: “For a safer side, what they do, they can just double the size and put it and deploy at that time. And they don’t know, and they are putting a lot of monthly recurring costs.”
Through comprehensive monitoring and analysis of resource utilization patterns, Synoptek has helped clients achieve an average of 20% reduction in cloud costs. This isn’t just about identifying underutilized resources; it’s about understanding usage patterns over time and making data-driven decisions about resource allocation.
The AI revolution: Empowering teams, not replacing them
The implementation of AI-powered operations will mark a fundamental shift in how Synoptek delivers services, with early indications pointing towards at least an 80% reduction in alert noise. But what happens to Level 1 engineers when alert volumes drop so dramatically? Synoptek saw an opportunity for evolution.
“Our L1 engineers who are appointed to see the continuous monitoring, that is no longer needed. We put them into more proactive or business strategic work…especially into DevOps operations support,” Pandya explains. This transformation represents a crucial opportunity for MSPs to elevate their service offerings while improving employee satisfaction and retention.
A new era for managed services providers
As Pandya concludes, “The biggest benefit is not only monitoring the cloud platform, we can manage all of our hyperscale and hybrid platforms as well. And it’s all in one place.” This unified approach, powered by AI and automation, represents the future of managed services.
The transformation journey isn’t without its challenges. Success requires careful planning, from selecting the right pilot clients to training teams on new capabilities. But the results, like improved service levels, reduced costs, and more strategic client relationships, make the effort worthwhile.
For MSPs watching from the sidelines, the message is clear: the future of IT operations lies not in having more tools or more data, but in having intelligent systems that can make sense of it all. The key is to start the journey now, learning from successful transformations like Synoptek’s while adapting the approach to specific business needs and client requirements.
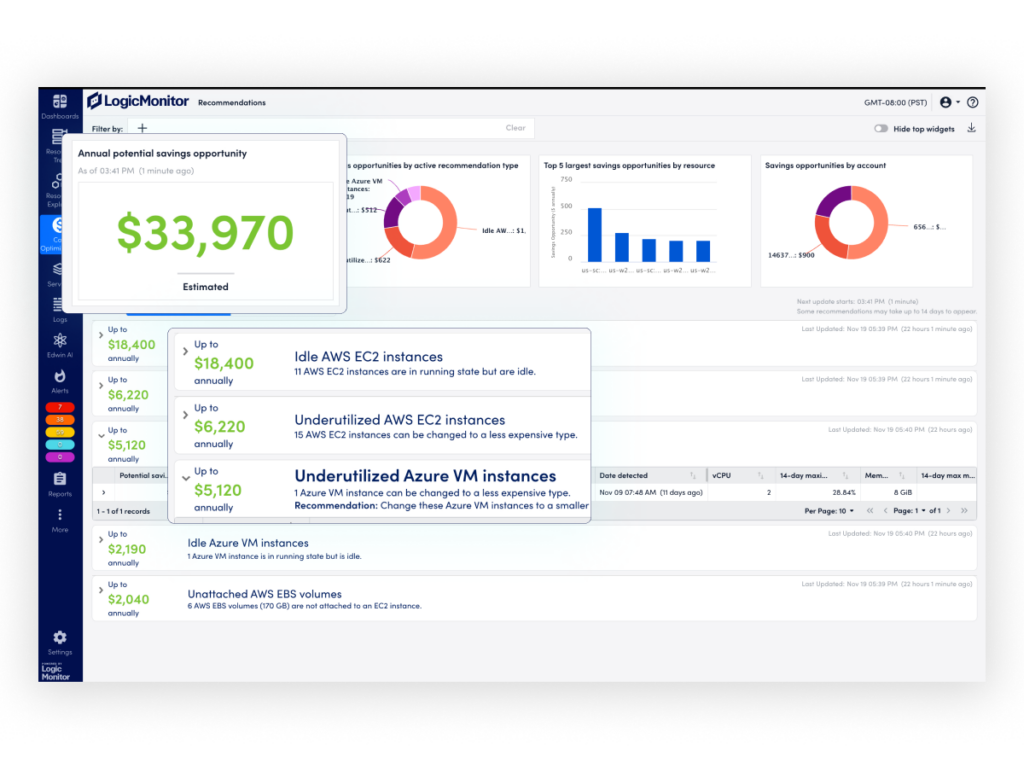
Managing Azure costs while ensuring performance and scalability can be a complex, resource-intensive process, especially when cost management tools are pieced together and used separately from monitoring solutions. To address this challenge, LogicMonitor is excited to announce cost-savings recommendations for Microsoft Azure compute and storage resources, simplifying cloud cost management with integrated insights.
This enhancement is part of the LogicMonitor Cost Optimization offering, first introduced in May 2024, which helps ITOps and CloudOps teams to manage hybrid cloud performance with cost efficiency. By showcasing deep multi-cloud billing visibility and AI-powered recommendations, Cost Optimization simplifies cloud investment management and maximizes ROI.
Integrated into LogicMonitor’s Hybrid Observability platform, LM Envision, Cost Optimization pairs continuous telemetry from AWS and Azure environments with proactive insights to intelligently manage performance and costs—ensuring teams stay focused on business value.
For example, when new features are put into production, teams might encounter excess compute from auto-scaling, resulting in potentially massive excess costs depending on the scope of the application. Cost Optimization will show early cost increases for the application, so teams can remediate before bills are generated.
Significantly reduce Azure expenses
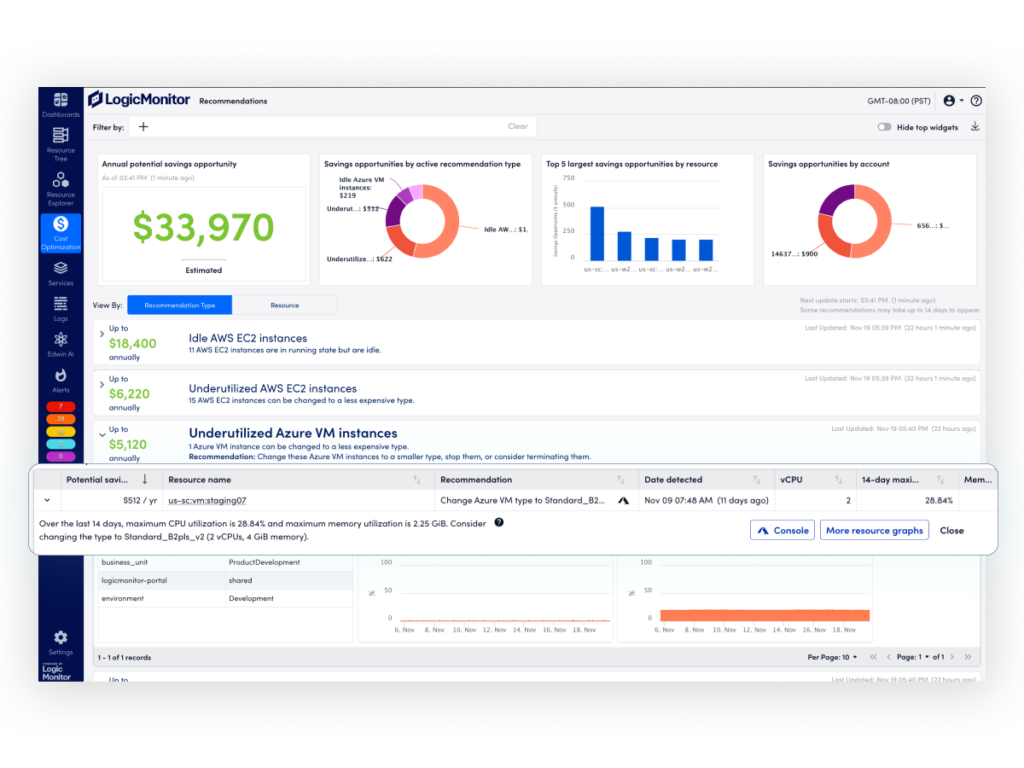
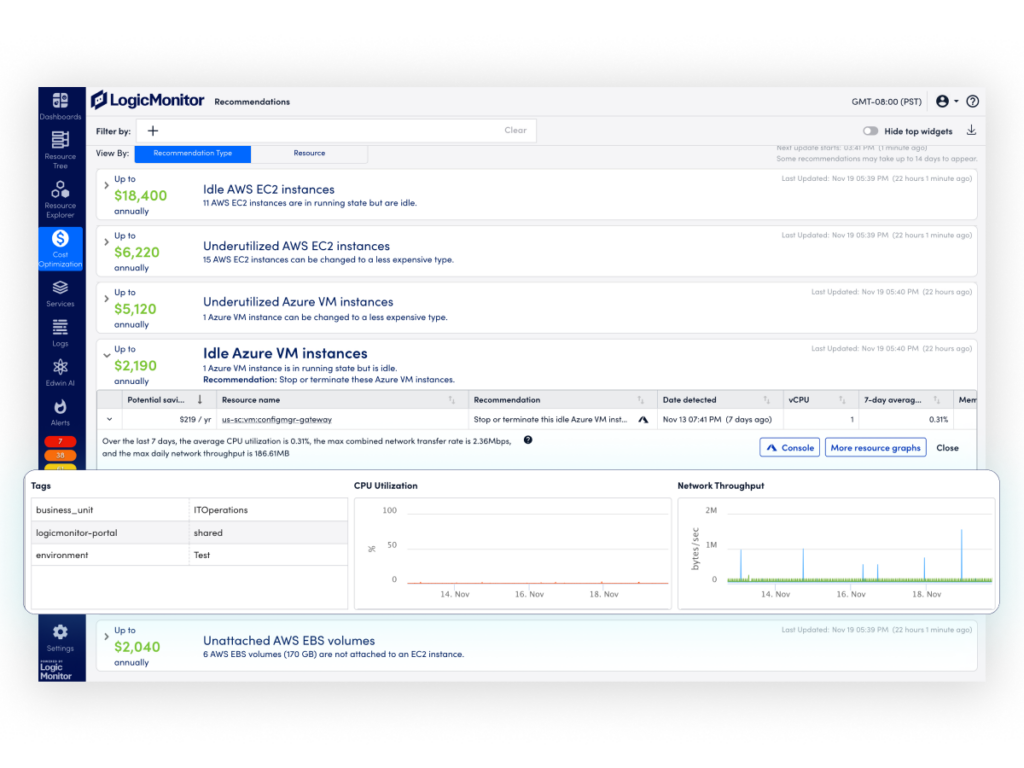
Azure’s scalability makes it a trusted choice for enterprises and MSPs to deploy their mission-critical workloads and applications, but without proactive cost monitoring, cloud spending can quickly spiral out of control. Common issues like over-provisioned virtual machines (VMs), unused storage, and unmanaged resources inflate expenses and divert IT teams like yours from their strategic goals. Manually and reactively researching and changing instances and capacity is time-consuming.
LM Envision addresses these challenges by continuously discovering Azure resources, collecting data and insights, and delivering AI-powered recommendations to optimize Azure compute and storage costs.
AI-powered recommendations drive resource efficiency
Our platform analyzes Azure compute and storage usage patterns using AI-driven algorithms and automation to:
- Reduce Azure expenses: Clearly see potential cost savings associated with each recommendation.
- Right-size resources: Adjust VM sizes and configurations based on historical performance data and current resource allocation, ensuring optimal usage and investment without compromising performance.
Eliminate waste: Identify idle or underused resources, such as unattached disks or underutilized storage, to help eliminate wasteful spend.
Explore cost optimization role-based access controls in detail.
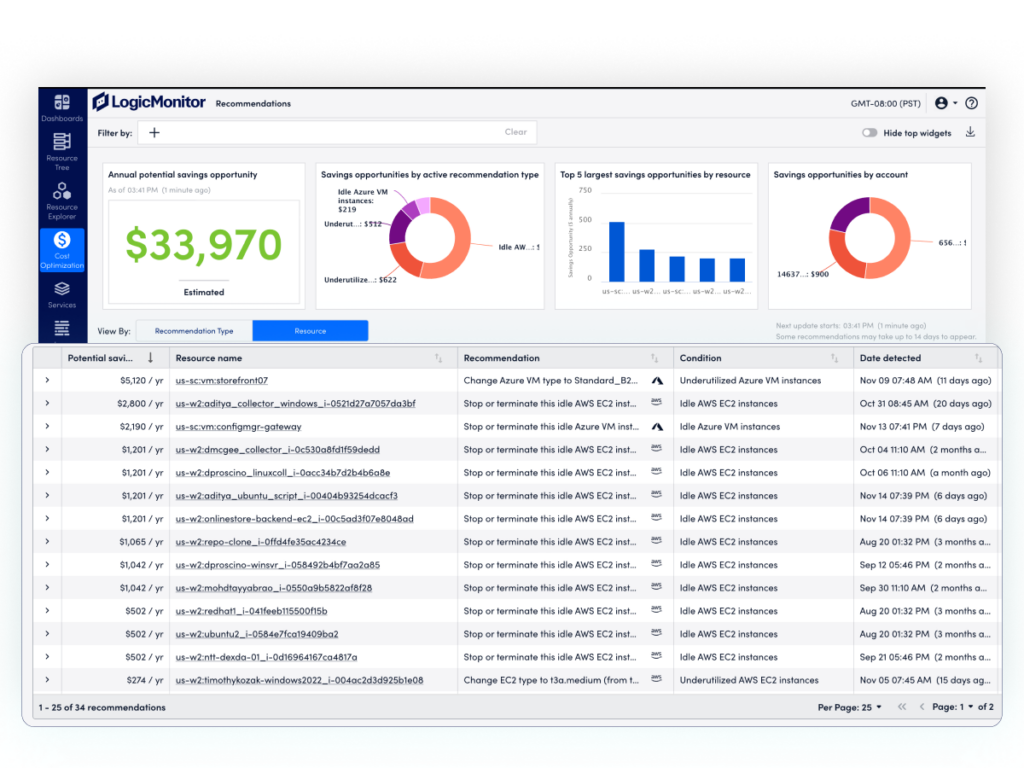
Azure cost reduction benefits for Platform Engineering and Operations teams
- Simple setup: LM Envision’s cost-savings recommendations are based on the Azure resource data we already monitor—no additional setup is required
- Deep context: Navigate to resource details with a direct connection into your Azure portal in just one click. Determine how to implement the recommendation so that business processes remain always on.
- Improved budget predictability: Reduce surprise costs and allocate resources effectively, enabling better collaboration with finance teams.
FinOps principles for Platform Engineering and Operations teams
Cost Optimization integrates FinOps principles directly into the workflows of Platform Engineering and Operations teams without a separate tool. Operations teams are empowered to manage Azure costs and collaborate with financial stakeholders. As a result, customers gain hybrid cloud efficiencies in one observability tool versus deploying multiple tools and piecing together information.
For financial stakeholders, Cost Optimization offers data-driven clarity into cloud expenditures, fostering accountability and strategic decision-making.
Start saving with LogicMonitor today
Azure cost optimization doesn’t have to be complex. LM Envision’s AI-powered recommendations simplify the process, driving significant savings and improving cloud efficiency. All of this happens while ensuring your Azure investments deliver long-term value.
Ready to see the difference LogicMonitor can make for your Azure environment? Contact us to learn more about transforming your approach to cloud cost management.
Keeping a network in top shape is essential, especially when a single bottleneck can slow down the whole operation. Troubleshooting network problems quickly keeps network performance on track, and NetFlow delivers advanced network services to organizations. This gives network admins and engineers real-time traffic visibility that helps track bandwidth and resolve issues before they become headaches—while also boosting performance.
By tapping into built-in NetFlow on routers and switches, you can get a front-row view of what’s actually happening across your network. This guide dives into everything you need to know about how to effectively use a NetFlow traffic analyzer to track bandwidth usage, identify traffic bottlenecks, and optimize network performance, giving your IT teams the tools to address issues before they impact users.
This article will touch base on the following areas:
- NetfFlow versions and flow record
- Key applications of NetfFlow
- Monitoring NetFlow data
- Insights gained through NetFlow monitoring
What is a NetFlow traffic analyzer?
A NetFlow traffic analyzer is a powerful tool that provides deep insights into network traffic patterns by analyzing NetFlow data generated by network devices. This tool helps network engineers and administrators monitor bandwidth, detect anomalies, and optimize network performance in real-time. Analyzing NetFlow data shows where bandwidth is used, by whom, and for what purpose, giving IT teams critical visibility to troubleshoot and manage network traffic effectively.
Understanding NetFlow
NetFlow is a network protocol developed by Cisco Systems to collect detailed information about IP traffic. Now widely used across the industry, NetFlow captures data such as source and destination IP addresses and ports, IP protocol, and IP service types. Using this data, network teams can answer essential questions, such as:
- Who is using the bandwidth? (Identifying users)
- What is consuming bandwidth? (Tracking applications)
- How much bandwidth is being used? (Highlighting “Top Talkers”)
- When is the peak bandwidth usage? (Monitoring top flows)
- Where are bandwidth demands the highest? (Analyzing network interfaces)
What is NetFlow data?
NetFlow data refers to the specific information the NetFlow protocol captures to track and analyze network behavior. It acts like a blueprint of network traffic, detailing everything you need to know about how data moves through your network. By breaking down source, destination, and flow details, NetFlow data allows network administrators to pinpoint the who, what, where, when, and how of bandwidth usage.
The evolution of NetFlow and Flow Records
NetFlow has come a long way since its start, with multiple versions introducing new capabilities to meet the growing demands of network monitoring. Each iteration brought enhanced features to capture and analyze network traffic, with NetFlow v5 and NetFlow v9 currently being the most commonly used versions. NetFlow v5 was an early standard, capturing a fixed set of data points per packet. NetFlow v9, however, introduced a more adaptable template-based format, including additional details like application IDs.
The most recent iteration, IPFIX (often called NetFlow v10), is an industry-standard version offering even greater flexibility. IPFIX expanded data fields and data granularity, making it possible to gather highly specific network metrics, such as DNS query types, retransmission rates, Layer 2 details like MAC addresses, and much more.
The core output of each version is the flow record, which is a detailed summary of each data packet’s key fields, like source and destination identifiers. This flow is exported to the collector for further processing, offering IT teams the granular data they need to make informed decisions and address network challenges efficiently.
How to monitor network traffic using a NetFlow analyzer
Monitoring network traffic with a NetFlow analyzer enables IT teams to capture, analyze, and visualize flow data, helping them track bandwidth usage and detect inefficiencies across the network. Here’s a breakdown of the key components in this process:
Flow exporter
A network device, such as a router or firewall, acts as the flow exporter. This device collects packets into flows, capturing essential data points like source and destination IPs. Once accumulated, it forwards the flow records to a flow collector through UDP packets.
Flow collector
A flow collector, such as LogicMonitor’s Collector, is a central hub for all exported flow data. It gathers records from multiple flow exporters, bringing network visibility across all devices and locations together in one place. With everything in one spot, admins can analyze network traffic without the hassle of manually aggregating data.
Flow analyzer
Like LogicMonitor’s Cloud Server, the flow analyzer processes the collected flow data and provides detailed real-time network traffic analysis. This tool helps you zero in on bandwidth-heavy users, identify latency issues, and locate bottlenecks. By linking data across interfaces, protocols, and devices, LogicMonitor’s flow analyzer gives teams real-time insights to keep traffic moving smoothly and prevent disruptions.
Real-time network traffic analysis across environments
When dealing with interconnected networks, real-time analysis of network traffic helps you better understand your data flows, manage your bandwidth, and maintain ideal conditions across on-premises, cloud, and hybrid IT environments. A NetFlow analyzer lets LogicMonitor users track data flow anywhere they need to examine it and optimize traffic patterns for current and future network demands.
Real-time traffic analysis for on-premises networks
For on-prem systems, LogicMonitor’s NetFlow analysis gives you immediate insights into local network behavior. It pinpoints peak usage times and highlights applications or devices that may be using more bandwidth than they should. This real-time visibility helps you prioritize bandwidth to avoid bottlenecks and get the most out of your on-site networks.
Cloud network traffic monitoring in real-time
In a cloud environment, real-time monitoring gives you a deep look into traffic flows between cloud-native applications and resources, helping you manage network traffic with precision. LogicMonitor’s NetFlow analysis identifies high-demand services and simplifies bandwidth allocation across cloud instances, ensuring smooth data flow between applications.
Traffic analysis in hybrid cloud networks
In a hybrid cloud environment, data constantly moves between on-premises and cloud-based resources, making the LogicMonitor real-time network traffic analysis even more critical. Our NetFlow analyzer tracks data flows across both private and public cloud networks, providing real-time visibility into how traffic patterns impact bandwidth. Using real-time monitoring and historical data trends, our tools enable network administrators to ensure network resilience, manage traffic surges, and improve overall network efficiency in complex hybrid cloud settings.
LogicMonitor’s flow analyzer lets IT teams spot high-traffic areas and identify the root causes of slowdowns and bottlenecks. Armed with this information, admins can proactively adjust bandwidth allocation or tweak routing protocols to prevent congestion. This type of traffic analysis optimizes bandwidth utilization across all types of environments, supporting smooth data transfer between systems.
Why use a NetFlow traffic analyzer for your network?
A NetFlow traffic analyzer does more than just monitor your network—it gives you real-time visibility into the performance and security needed to keep everything running smoothly. With insights that help optimize network efficiency and troubleshoot issues before they become disruptions, NetFlow monitoring is an invaluable tool for keeping your network in top shape. Here’s a look at some key ways NetFlow monitoring can drive network efficiency and keep everything running smoothly:
1. Clear network visibility
A NetFlow traffic analyzer gives network admins real-time visibility into traffic flows, making it easy to see who’s using bandwidth and which apps are hogging resources. With live insights like these, admins can jump on performance bottlenecks before they become full-blown issues, ensuring users experience a smooth, seamless network. Using this data, you can quickly predict QoS (Quality Of Service) and direct resources based on users. You can also prevent network exposure to malware risks and intruders.
2. Root cause analysis of network issues
NetFlow monitoring makes finding the root cause of network slowdowns much easier. When users experience delays accessing applications, NetFlow data gives you a clear view of where your problem might be located. By analyzing traffic patterns, packet drops, and response times, your team can pinpoint which device, application, or traffic bottleneck is causing the lag. Your teams can use this data to resolve the problem at its source, keeping the network humming and users unaware.
3. Bandwidth optimization and performance troubleshooting
NetFlow data drills down into bandwidth usage across interfaces, protocols, and applications, helping you spot “top talkers”—the heaviest bandwidth users—on the network. With this detailed view, IT teams can quickly decide if high-usage traffic is relevant or needs adjusting. This helps balance resources efficiently, boosting overall network performance.
4. Forecasting bandwidth utilization and capacity planning
NetFlow data isn’t just for today’s needs; it helps IT teams look ahead. By analyzing traffic patterns over time, admins can forecast future bandwidth requirements, giving them the insight to plan capacity strategically. This proactive approach ensures your network can handle peak traffic times without slowdowns, keeping performance steady in the long run.
5. Identification of Security Breach
A NetFlow traffic analyzer is invaluable for detecting potential security threats, from unusual traffic spikes to unauthorized access attempts. Many types of security attacks consume network resources and cause anomalous usage spikes, which might mean a security breach. NetFlow data enables admins to monitor, receive alerts, and investigate suspicious patterns in real-time, addressing issues before they become security breaches.
Key insights from LogicMonitor’s NetFlow monitoring
Using LogicMonitor’s NetFlow Monitoring, one can get valuable insights on the below data points:
- Bandwidth Utilization
Identify the network conversation from the source and destination IP addresses and traffic path in the network from the Input and Output interface information.
- Top Flows and Top Talkers
Identify Top N applications, Top Source/Destination Endpoints, and protocols consuming the network bandwidth.
- Consumers of the Bandwidth
Keep track of interface details and statistics of top talkers and users. This can help determine the origin of an issue when it’s reported.
- Bandwidth Hogging
Analyze historical data to examine incident patterns and their impact on total network traffic through the packet and octet count.
- ToS and QoS Analysis
Using ToS (Type of Service), ensure the right priorities are provided to the right applications. Verify the Quality of Service (QoS) levels achieved to optimize network bandwidth for the specific requirements.
- IPv6 Traffic Monitoring
LogicMonitor’s NetFlow Monitoring provides out-of-the-box support for a mix of IPv4 and IPv6 environments and the flexibility to differentiate TopN flows in each protocol. IPv6 adoption is gaining significant traction in the public sector, large-scale distribution systems, and companies working with IoT infrastructures.
- Applications Classification through NBAR2
Network-Based Application Recognition (NBAR) provides an advanced application classification mechanism using application signatures, databases, and deep packet inspection. Enabling NBAR on specific devices directly within the network accomplishes this.
NetFlow traffic analyzer vs. other network monitoring tools
Each network monitoring tool brings its own strengths to the table, but NetFlow stands out when you need detailed traffic insights. With its ability to capture entire traffic flows, track bandwidth usage, and provide real-time visibility down to the user level, NetFlow is uniquely suited for in-depth network analysis. Here’s how NetFlow stacks up to other common methods:
- SNMP (Simple Network Management Protocol): SNMP is a popular go-to for device monitoring, providing valuable status data, such as device health and connectivity. However, unlike NetFlow, it doesn’t offer the granularity to drill down into specific traffic flows or analyze bandwidth by user or application.
- sFlow: sFlow offers real-time network monitoring similar to NetFlow but samples traffic instead of tracking every packet. This is helpful in high-speed networks with massive data volumes. NetFlow’s detailed traffic records provide a fuller view, making it the preferred choice of many admins and engineers for in-depth traffic analysis.
- Packet sniffers: Packet sniffers, like Wireshark, capture every packet for deep packet inspection and troubleshooting. While packet sniffers are great for precise packet analysis, they’re resource-heavy, less scalable, and lack NetFlow’s high-level summary, making NetFlow better suited for long-term traffic analysis and monitoring.
Choosing the right NetFlow traffic analyzer for your network
A NetFlow traffic analyzer is no place to cut corners. When choosing a traffic analysis tool, consider factors like network size, complexity, and scalability. The right NetFlow analyzer will simplify monitoring, enhance capacity planning, and support a complex network’s performance needs. Keep these features in mind when selecting your traffic analysis tool:
- Scalability: Plan for growth. Select a solution that can keep up as your network expands. For example, LogicMonitor’s NetFlow analyzer supports a range of network sizes while maintaining high performance.
- Integration: Compatibility is key. Choose a tool that integrates smoothly with your existing infrastructure, including network devices, software, and other bandwidth monitoring tools. This ensures better data flow and fewer integration hurdles.
- Ease of use: Sometimes, simplicity is best. An intuitive interface and easy-to-navigate dashboards streamline network management. Look for tools with customizable dashboards, like LogicMonitor, to make data visualization and metric tracking more accessible for your team.
Leveraging historical data from a NetFlow analyzer for trend analysis
A NetFlow analyzer does more than keep tabs on what’s happening right now—it also builds a rich library of historical data that’s invaluable for understanding network patterns over time. Harnessing historical NetFlow data transforms your network management from reactive to proactive, giving your team the foresight to stay ahead of network demands and keep performance steady. Analyzing traffic trends allows you to catch usage shifts, pinpoint recurring bottlenecks, and anticipate future bandwidth needs. Here’s how trend analysis is a game-changer for network management:
- Capacity planning: Historical data better prepares you for growth. Analyzing traffic patterns lets you predict when and where you might need to expand your network, helping you avoid unexpected slowdowns and allocate resources where your system needs them most.
- Issue prevention: Spotting patterns in past issues can reveal weak spots. By identifying trends in packet loss, latency spikes, or high bandwidth usage, your team can address problem areas and prevent potential disruptions.
- Optimizing resource allocation: Historical data helps you understand not only peak usage times but also which applications or users consistently consume a lot of bandwidth. With these insights, you can fine-tune resource allocation to maintain smooth network performance, even as demands evolve.
Customizing LogicMonitor’s NetFlow dashboards for better insights
Personalizing NetFlow dashboards is key to tracking the metrics that matter most to your network. With personalized dashboards and reports, LogicMonitor’s NetFlow capabilities provide a clear view of your network’s performance and use filters to narrow down metrics that impact network reliability. LogicMonitor makes it easy to set up custom views, helping you keep essential data at your fingertips.
- Tailored tracking: Customize dashboards to display specific metrics, such as top talkers, application performance, or interface traffic. Your team can monitor critical elements without sifting through unnecessary information by zeroing in on relevant data.
- Detailed reporting: You can generate reports that match your organization’s needs, from high-level summaries to deep-dive analytics. Custom reports let you focus on trends, performance, and usage patterns—whether you’re managing day-to-day operations or planning for growth.
Threshold alarms and alerts
LogicMonitor’s NetFlow analyzer lets you configure threshold alarms and alerts that enable your team to monitor network performance and detect anomalies in real-time. These alerts immediately flag unusual activity, such as bandwidth spikes or sudden drops in traffic, helping your team react quickly and keep network disruptions at bay. Here are a few ways that threshold alarms and alerts work to enhance monitoring:
- Customizable thresholds: Set individual thresholds for various traffic metrics, including bandwidth usage, latency, or protocol-specific data flows. Customization lets you tailor alerts to align with your network’s normal behavior, so you’re only notified when activity deviates from the expected range.
- Real-time alerts: LogicMonitor’s real-time alerts let you know the moment traffic deviates from set parameters. This instant feedback lets you respond quickly to potential issues, avoiding outages, slowdowns, or security vulnerabilities.
- Incident prioritization: By configuring alerts based on severity levels, you can prioritize responses according to the potential impact. You can set critical alerts to escalate instantly for immediate action, while you can document less urgent instances for review, keeping your team focused where they’re needed most.
- Performance tuning: Use historical data to fine-tune thresholds over time. Analyzing past trends helps optimize threshold settings, minimizing false alarms and improving accuracy for current network conditions.
Common network issues solved by NetFlow traffic analyzers
A NetFlow traffic analyzer is a powerful tool for spotting and resolving common network issues that can slow down or even compromise performance. Here’s a look at some of the most frequent network problems it addresses, along with how NetFlow data supports quick troubleshooting and issue resolution:
Bandwidth hogging
Heavy bandwidth usage, or “bandwidth hogging,” is a common culprit behind slow network speeds. NetFlow lets you see the heaviest bandwidth users, enabling your IT team to track which applications, devices, or users use the most resources. With this information, admins can adjust traffic flow to ensure everyone gets the necessary bandwidth.
Application slowdowns
Slow applications can get in the way of productivity. By analyzing NetFlow data, you can pinpoint the exact source of the slowdown, whether it’s high traffic volume, network latency, or misconfigured settings. With targeted data on hand, your team can quickly address the root cause of lagging applications and restore performance.
Network congestion and bottlenecks
Traffic congestion is especially common during peak usage times. NetFlow data highlights areas of high traffic density, helping admins identify and manage bottlenecks in real-time. By analyzing traffic flows across devices and interfaces, IT teams can reroute traffic or adjust resources to reduce congestion and keep data flowing smoothly.
Security threats and unusual activity
Unexpected traffic patterns can be an early warning sign of security threats, like DDoS attacks or unauthorized access attempts. NetFlow data enables IT teams to monitor and investigate unusual activity as it’s happening. With instant alerts and historical traffic records, teams can quickly detect, analyze, and shut down suspicious behavior before it escalates into a security breach.
Resource misallocation
Sometimes, network issues come down to how resources are allocated. NetFlow helps administrators track traffic by specific protocols or applications, enabling more precise resource distribution. By understanding actual usage patterns, IT can allocate bandwidth and prioritize applications more effectively, ensuring that critical services are always well supported.
In tackling these common network challenges, NetFlow’s data-driven insights let you respond proactively, keeping networks running efficiently and securely while reducing the risk of interruptions.
Take control of your network with NetFlow analysis
NetFlow for your network management is about staying proactive, enhancing performance, and making informed decisions based on real data. A NetFlow traffic analyzer equips your team with the insights they need to keep your networks operating securely and efficiently. With LogicMonitor’s AI-powered, customizable dashboards and threshold alerts, you’re fully prepared to track bandwidth usage, detect anomalies, and get ahead of issues before they impact the user experience.
OpenShift is a platform that allows developers, operations engineers, or even DevOps professionals to run containerized applications and workloads. It is best described as a cloud-based container orchestration platform, although an “on-prem” version is also possible.
Under the hood, it’s powered by Kubernetes, but an additional architectural layer makes life simpler for DevOps teams. OpenShift is from enterprise software specialist Red Hat and provides a range of automation options and lifecycle management, regardless of where you run your applications.
OpenShift architecture runs in any environment. The OS is usually Linux, but it also can use Centos. On top of that is the standard Kubernetes layer. However, there’s also an additional layer transforming Kubernetes into OpenShift.
OpenShift versions
Red Hat’s OpenShift container platform comes in a few different “flavors,” as IBM likes to call them. OKD or Origin Key Distribution powers an open-source version. OpenShift’s payable versions come with dedicated support, but only within the version lifecycle. For example, OpenShift 4.12 went live on January 17, 2023, and is supported until January 2025.
Why is OpenShift so popular?
OpenShift provides a range of enterprise-ready services straight out of the box. Plenty of other container orchestration services are available, such as Amazon EKS or the Google Kubernetes Engine (GKE). However, with any of these, businesses often need to invest in multiple additional services to make them useful as a full deployment and delivery solution.
OpenShift is a more desirable solution for enterprises that want to be able to build, deploy, and scale fast using a single platform.
How OpenShift differs from other container orchestration platforms
Other container orchestration platforms are aimed at everyone, from individual developers to SMEs, but OpenShift is marketed toward large enterprises. OpenShift empowers businesses to shift to cloud-native development and embrace continuous integration and delivery (CI/CD). Various levels of automation simplify day-to-day tasks and free up DevOps to spend time on other tasks. The platform includes features designed to facilitate faster deployment, plus a full suite of services.
Unlike many competitors, OpenShift provides extensive integrated services that support the full application lifecycle out of the box. Let’s examine a couple of popular OpenShift competitors.
- Docker Swarm is known for its simplicity and ease of use, appealing to smaller teams or projects that need straightforward container management without complex setup. However, it lacks the robust CI/CD capabilities and advanced security features that OpenShift offers.
- Amazon EKS and Amazon GKE provide scalable, cloud-native Kubernetes environments that are tightly integrated with their respective cloud platforms. While they offer powerful options for teams already using AWS or Google Cloud, they often require supplementary services. OpenShift’s all-in-one approach delivers built-in developer tools, automation for CI/CD, and strong multi-cloud and hybrid support.
Architectural components of OpenShift
OpenShift’s multi-layered architecture combines infrastructure and service layers with a structured node system to ensure flexibility, scalability, and performance across various environments.
Layer types
- Infrastructure layer: This foundational layer is the launchpad for deployment across physical, virtual, or cloud-based setups. Compatible with major public clouds like AWS, Azure, and GCP, it abstracts hardware quirks to provide a seamless environment for containerized apps.
- Service layer: Built on Kubernetes, the service layer powers OpenShift’s core. Packed with Red Hat’s integrated tools for monitoring, logging, and automation, it acts as a central command hub—managing networking, storage, and security. Plus, built-in CI/CD pipelines keep development and deployment fast and friction-free.
Node types
In OpenShift, nodes are the backbone of the cluster, working together to stay organized and efficiently manage workloads:
- Master nodes: The brains of the operation, master nodes handle API requests, coordinate workloads, and allocate resources across the infrastructure.
- Infrastructure nodes: Dedicated to essential service components, such as routing, image registries, and monitoring, infrastructure nodes free up worker nodes so they can focus solely on running your apps.
- Worker nodes: Running the containerized applications, worker nodes keep workloads balanced across the cluster to maintain high performance and ensure that reliability never wavers.
By combining these layers and nodes, OpenShift simplifies operational complexity without sacrificing scalability or security. This powerful mix lets enterprises confidently approach cloud-native development by utilizing built-in CI/CD, observability, and strong security practices to support every stage of the application lifecycle.
OpenShift vs. Kubernetes
Both OpenShift and Kubernetes offer powerful container orchestration, except OpenShift builds on Kubernetes with additional enterprise-ready features. Let’s take a closer look at how these platforms compare in terms of functionality, setup, and support.
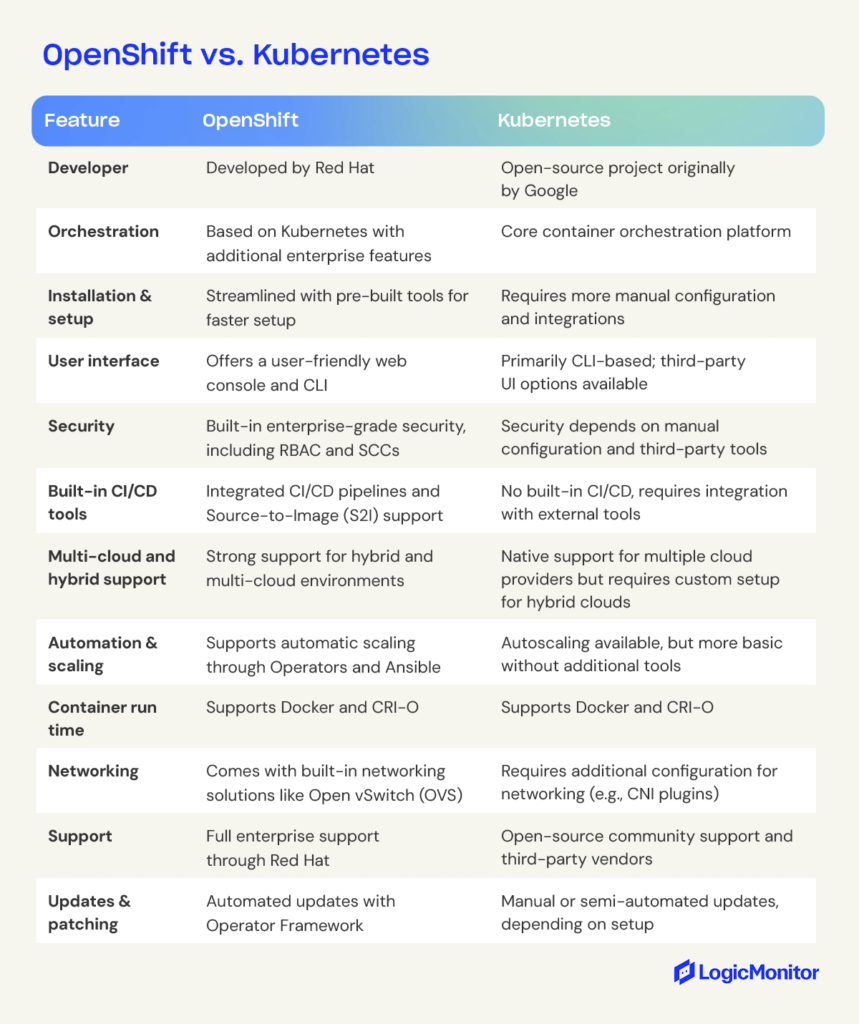
Key features of OpenShift
OpenShift utilizes image streams to shift container images to the cluster. Image streams allow changes to occur via automation. Basically, as soon as any alteration occurs in the source code, an image stream allows a developer to push those changes through with minimal application downtime.
On the monitoring and automation side, OpenShift has some serious tools for streamlined management. Built-in monitoring dives deep into container performance, resource usage, and troubling issues you might encounter, helping DevOps pinpoint and remedy bottlenecks quickly.
On the automation side, OpenShift uses Operators and Ansible Playbooks to handle routine management tasks and scale infrastructure. Operators act like custom helpers that simplify deployment and maintenance, while Ansible Playbooks add scripting power, letting teams easily spin up new nodes or containers.
Since OpenShift is cloud-based, it plays well with any infrastructure, making it ideal for multi-platform development. Developers don’t have to constantly shift how they code to match different ecosystems. Plus, OpenShift includes upstream Kubernetes and Linux CoreOS, delivering an all-in-one solution right out of the box.
Best practices for monitoring
Built-in tools like Prometheus and Grafana are great for tracking container health and resource usage, while external tools like Dynatrace bring real-time insights and anomaly detection for enhanced observability. Dynatrace’s integration with OpenShift helps teams monitor app health, dependencies, and resource demands, giving them a proactive option for tackling issues.
With OpenShift 4.12, new features like IBM Secure Execution, pre-existing VPC setups, and custom cluster installations improve monitoring and automation capabilities, making it even better suited for the continual demands and unique needs of enterprise environments.
Benefits of OpenShift
One of OpenShift’s standout advantages is its support for hybrid and multi-cloud environments. This allows you to launch and manage applications seamlessly across a mix of on-prem, private, and public cloud environments. This flexibility helps avoid vendor lock-in, balance workloads between environments, and give you value for your cost with top-notch performance.
Seamless integration across platforms
OpenShift’s consistent Kubernetes-based foundation makes it easier to deploy, manage, and scale applications across cloud providers and on-premises data centers. With built-in automation tools like Operators and Ansible Playbooks, OpenShift maintains application consistency and performance across different platforms, providing users a uniform experience even in complex multi-cloud deployments.
Hybrid Cloud benefits
If your business embraces a hybrid cloud, OpenShift offers tools for optimizing resources and scaling applications between on-prem and cloud environments. Its hybrid support enables you to keep critical workloads on-prem while taking advantage of the cloud’s scalability and cost efficiency. OpenShift’s centralized management is all about simplicity and efficiency, giving DevOps cloud and on-prem resource management with a single console.
Streamlined operations
With its unified management console and automation features, OpenShift enables your team to deploy updates across multiple environments without needing custom solutions for each platform. This reduces operational overhead and helps you stay agile, making OpenShift a compelling option for organizations moving toward cloud-native development.
Use case example: financial services
A financial institution looking to maximize operational efficiency while meeting regulatory requirements could use OpenShift’s multi-cloud support to manage sensitive data in an on-prem environment while launching customer-facing applications in the cloud. This setup balances security with scalability, letting them respond rapidly to changing customer needs without compromising data protection.
Scaling with OpenShift
Scalability can be a challenge as apps acquire larger user bases or need to perform additional tasks. OpenShift supports the deployment of large clusters or additional hosts and even provides recommended best practices to assure persistent high performance even as applications grow. For example, the default cluster network is:
cidr 10.128.0.0/14
However, this network only allows clusters of up to 500 nodes. OpenShift documentation explains how to switch to one of the following networks:
10.128.0.0/12 or 10.128.0.0/10
These networks support the creation of clusters with more than 500 nodes.
OpenShift allows developers to create “stacks” of containers without reducing performance or speed.
OpenShift also utilizes other tools in its tech stack to support scaling, such as Ansible Playbooks. Ansible is an open-source infrastructure automation tool that Red Hat initially developed. By taking advantage of Ansible Playbooks, OpenShift allows developers to create a new host speedily and bring it into the cluster, simplifying scaling up or down.
OpenShift security
OpenShift is built with enterprise security in mind, supporting secure deployment and scaling while also protecting the development infrastructure. Considering cyberattacks surged by 30% year-over-year in Q2 2024, reaching an average of 1,636 attacks per organization per week, this is a key benefit for many developers.
With built-in support for Role-Based Access Control (RBAC) and Security Context Constraints (SCCs), OpenShift lets you enforce strict access control policies, giving only authorized users access to specific resources. OpenShift’s security framework also integrates seamlessly with many existing corporate identity management systems, providing Single Sign-On (SSO) capabilities that make user management even easier.
Automated security updates and patching
One of OpenShift’s most outstanding security features is its automated updates and patching. By making these tasks automatic, OpenShift reduces the possibility of security risks that tend to go along with outdated software versions or configurations. This reduces the likelihood of vulnerabilities in your production environments. Through frameworks like Operators, OpenShift manages updates for both the platform and applications it supports, enabling DevOps teams to keep security measures current with little to no manual intervention.
Network and data protection
OpenShift offers several powerful network security features, including encrypted communication between containers and stringent network traffic flow restriction policies to reduce exposure. It also offers data encryption both at rest and in transit, helping to keep sensitive information protected throughout its lifecycle.
Security across hybrid and multi-cloud environments
For organizations with hybrid and multi-cloud architectures, OpenShift ensures that security policies are consistent across environments, giving teams unified security protocols to manage applications. OpenShift’s multi-environment security supports compliance while retaining the flexibility of a hybrid cloud, making it especially valuable if your company handles sensitive data that has to comply with regulatory standards.
OpenShift use cases
OpenShift is ideal for modernizing existing apps as well as creating new ones. It transforms the deployment of upgrades and changes, allowing for effortless scaling. Because OpenShift runs on any cloud, it effectively future-proofs applications while ensuring they remain secure and stable. Use cases include:
- Lifting and shifting existing web apps into containerized environments
- Developing cloud-native applications
- Creating apps via distributed microservices
- Quickly add a new service or feature to an existing app
This last point is a key feature of continuous integration and continuous delivery (CI/CD) and is vital for retaining an engaged user base.
Industry use cases
OpenShift is widely adopted across industries, offering flexibility, security, and scalability that make it a top choice for diverse applications:
Financial services: Financial institutions benefit from OpenShift’s security features, ensuring compliance with GDPR and PCI DSS regulations. Banks can keep sensitive data secure on-premises by utilizing hybrid cloud capabilities while deploying customer-facing applications in the cloud. For example, a financial institution in Peru used OpenShift to regularly increase the number of services available to users, reducing the need for in-branch visits and cutting transaction costs by 3%.
Healthcare: Healthcare providers rely on OpenShift to maintain HIPAA compliance and secure patient data across on-premises and cloud environments. OpenShift’s RBAC, SCCs, and data encryption help keep patient data protected at all stages. Another helpful feature is OpenShift’s automated updating, which reduces the need for manual patching, freeing IT resources to focus on other critical tasks.
Retail: In retail, OpenShift empowers companies to build and scale e-commerce platforms quickly, providing a sturdy foundation for handling high traffic volumes during peak times. With CI/CD automation, retailers can update their online stores and integrate new features as often as necessary to keep up with market demands, giving their customers a more pleasant shopping experience.
Implementing continuous integration and delivery (CI/CD)
CI/CD is a growing development approach that uses automation to ensure app updates and adjustments happen as quickly as possible with minimal downtime. Containerized development environments already support continuous integration—the rapid testing and deployment of small code changes—by allowing tests to occur in isolation prior to deployment. Thanks to its simplified interface, OpenShift makes CI/CD pipelines even more efficient by reducing the risk of human error and helping developers maintain consistent processes.
Research shows that even though the benefits of CI/CD are clear, not all organizations are confident of their ability to make this shift. OpenShift could help businesses maximize their digital transformation efforts by empowering developers to embrace the CI/CD culture and get apps to users faster.
OpenShift provides templates for objects and utilizes Jenkins jobs and pipelines to improve automation and promote CI/CD for all application development and deployment. For those comparing Jenkins tools for CI/CD, this article on Jenkins vs. Jenkins X can help clarify which solution best fits your needs.
How to set up and deploy using an OpenShift cluster
Firstly, a developer or DevOps professional needs to get access to OpenShift. You can download and manage the free version yourself, but the fully managed version needs to be purchased from Red Hat. When you subscribe to a hosted version of OpenShift, you’ll get the secure credentials needed to deploy the OpenShift environment.
The simplest way to interact with OpenShift is via the web console. There is also an oc command-line tool.
Before deploying any application, you must create a “project.” This contains everything related to the application.
At this point, you can also use the web console to add collaborators.
You can deploy applications to OpenShift clusters via various methods, including:
- Using an existing container image hosted outside the OpenShift cluster
- Importing an existing container image into an image registry within the OpenShift cluster
- Using source code from a Git repository hosting service
OpenShift also provides templates to simplify the deployment of apps with multiple components. Within the template, you can set your own parameters to exercise complete control over the deployment process. To access these, use the console’s “Add to Project” function. There’s a whole section here dedicated to CI/CD.
To enter image stream tags, use the “Deploy Image” tab in the console or “oc new-app” in the CLI. You can monitor or even scale up from here by adding more instances of that container image.
Wrapping up
Red Hat provides extensive resources to support teams deploying and optimizing OpenShift, making it easier to get the best from this platform. With robust automation and security features and its support for hybrid and multi-cloud environments, OpenShift proves to be a powerful solution for modern app development and deployment. OpenShift enables you to confidently scale, secure, and streamline applications, creating an agile and resilient infrastructure that meets today’s evolving demands.
NetApp, formerly Network Appliance Inc., is a computer technology company specializing in data storage and management software.
Known for its innovative approach to data solutions, NetApp provides comprehensive cloud data services to help businesses efficiently manage, secure, and access their data across diverse environments. Alongside data storage, NetApp offers advanced management solutions for applications, enabling organizations to streamline operations and enhance data-driven decision-making across hybrid and multi-cloud platforms.
What is NetApp?
NetApp is a computer technology company that provides on-premises storage, cloud services, and hybrid data services in the cloud. Its hardware includes storage systems for file, block, and object storage. It also integrates its services with public cloud providers. NetApp’s services offer solutions for data management, enterprise applications, cybersecurity, and supporting AI workloads. Some of its main products include different storage software and servers.
NetApp has developed various products and services, and according to Gartner, was ranked the number one storage company in 2019. The following includes detailed definitions of NetApp’s key terms and services.
Azure NetApp is a popular shared file-storage service used for migrating POSIX-compliant Linux and Windows applications, HPC infrastructure, databases, SAP HANA, and enterprise web applications.
Why choose NetApp?
NetApp provides organizations with advanced data storage and management solutions designed to support diverse IT environments, from on-premises to multi-cloud. For businesses looking to enhance their infrastructure, NetApp offers several key advantages:
- Cost efficiency: NetApp’s tools help optimize cloud expenses, enabling companies to manage data growth without excessive costs, while its efficient storage solutions reduce overall spending.
- Scalability: Built to grow with your business, NetApp’s services seamlessly scale across cloud, hybrid, and on-premises environments, making it easier to expand as data needs evolve.
- Enhanced security: NetApp prioritizes data protection with features designed to defend against cyber threats, ensuring high levels of security for critical information.
- Seamless cloud integration: With strong support for leading cloud providers like Google Cloud Platform (GCP) and AWS, NetApp simplifies hybrid cloud setups and provides smooth data migration across platforms.
Understanding the dos and don’ts of NetApp monitoring can help you maximize its benefits. By selecting NetApp, IT professionals and decision-makers can leverage streamlined data management, improved performance, and flexible integration options that fit their organization’s unique needs.
What are NetApp’s key services?
NetApp offers several important services and products to help customers meet their data storage and management goals.
Ansible
Ansible is a platform for automating networking, servers, and storage. This configuration management system enables arduous manual tasks to become repeatable and less susceptible to mistakes. The biggest selling points are that it’s easy to use, reliable, and provides strong security.
CVO
CVO (Cloud Volumes ONTAP) is a type of storage delivering data management for block and file workloads. This advanced storage allows you to make the most of your cloud expenses while improving application performance. It also helps with compliance and data protection.
Dynamic Disc Pool
Dynamic Disc Pool technology (DDP) addresses the problem of RAID rebuild times and the potential increase in disk failure and reduced performance this may cause. DDP delivers prime storage solutions while maintaining performance. The technology can rebuild up to four times more quickly while featuring exceptional data protection. DDP allows you to group similar disks in a pool topology with faster rebuilds than RAID 5 or 6.
For more on monitoring disk performance and latency in NetApp environments, explore how LogicMonitor visualizes these metrics to optimize storage efficiency.
FAS
FAS (Fabric Attached Storage) is a unified storage platform in the cloud. FAS is one of the company’s core products. NetApp currently has six models of storage to choose from, allowing users to select the best model that meets their organization’s storage needs. These products consist of storage controllers with shelves made of hard disk enclosures. In some entry-level products, the storage controller contains the actual drives.
Flexpod
Flexpod is a type of architecture for network, server, and storage components. The components of a Flexpod consist of three layers: computing, networking, and storage. Flexpod allows users to select specific components, making it ideal for almost any type of business. Whether you’re looking for rack components or optimizing for artificial intelligence, Flexpod can help you put together the architecture your organization needs.
FlexCache
FlexCache offers remote simplified file distribution. It can also improve WAN usage with lower bandwidth costs and latency. You can distribute through multiple sites. FlexCache provides a more significant storage system ROI, improves the ability to handle workload increases, and limits remote access latency. It’s also easier to scale out storage performance with read-heavy applications. ONTAP Select running on 9.5 versions or later, FAS, and AFF support FlexCache.
OnCommand (OCI)
An OnCommand Insight Server (OCI) provides access to storage information and receives updates involving environment changes from acquisition units. The updates pass through a secure channel and then go to storage in the database. OCI can simplify virtual environments and manage complex private cloud systems. OCI allows analysis and management across networks, servers, and storage in both virtual and physical environments. It specifically enables cross-domain management.
OnCommand has two different Acquisition units. These are the Local Acquisition Unit (LAU), which you can install along with the OnCommand Insight Server, and the Remote Acquisition Unit (RAU). This one is optional. You can install it on a single remote server or several servers.
ONTAP
This is the operating system for hybrid cloud enhancement that helps with staffing, data security, and promoting future growth. New features for ONTAP include greater protection from ransomware, simplification for configuring security profiles, and more flexibility for accessing storage.
StorageGRID
If your organization has large data sets to store, StorageGrid is a solution that can help you manage the data cost-efficiently. StorageGrid offers storage and management for large amounts of unstructured data. You can reduce costs and optimize workflows when you place content in the correct storage tier. Some of the reviews for NetApp StorageGRID state that three of its best features are its valuable backup features, easy deployment, and cost-effectiveness.
Snapshot
Snapshots are designed to help with data protection but can be used for other purposes. NetApp snapshots are for backup and restoring purposes. When you have a snapshot backup, you save a specific moment-in-time image of the Unified database files in case your data is lost or the system fails. The Snapshot backup is periodically written on an ONTAP cluster. This way, you’ll have an updated copy.
Solidfire
Solidfire is one of NetApp’s many acquisitions, as it took over the company in January 2016. Solidfire uses the Element operating system for its arrays. This NetApp product provides all-flash storage solutions. SolidFire is not as successful as other products at NetApp; ONTAP, in particular, overshadows SolidFire. Some industry professionals may question how long SolidFire will continue as a NetApp product. So far, SolidFire is still a private cloud hardware platform.
Trident
Trident is an open-source project that can meet your container application demands. It utilizes Kubernetes clusters as pods. This offers exceptional storage services and allows containerized apps to consume storage from different sources. Trident provides full support as an open-source project and uses industry-standard interfaces. These interfaces include the Container Storage Interface.
NetApp’s integration with public cloud platforms
NetApp’s solutions are designed to support organizations working across hybrid and multi-cloud environments, offering seamless compatibility with major cloud providers like GCP and AWS. NetApp’s tools, including CVO and StorageGRID, enable efficient data management, transfer, and protection, ensuring that businesses can maintain control of their data infrastructure across platforms.
- CVO: CVO offers data management across cloud environments by combining NetApp’s ONTAP capabilities with public cloud infrastructure. This solution allows organizations to optimize cloud storage costs and manage data protection, compliance, and performance. For example, a company using CVO with GCP can streamline its data backup processes, reducing both costs and latency by storing frequently accessed data close to applications.
- StorageGRID: Designed for storing large amounts of unstructured data, StorageGRID enables multi-cloud data management with the flexibility to tier data across cloud and on-premises environments. By supporting object storage and efficient data retrieval, StorageGRID allows businesses to manage compliance and access requirements for big data applications. A healthcare organization, for example, could use StorageGRID to store and retrieve extensive medical records across both private and public cloud environments, ensuring secure and compliant access to data when needed.
With NetApp’s hybrid and multi-cloud capabilities, businesses can reduce the complexity of managing data across cloud platforms, optimize storage expenses, and maintain compliance, all while ensuring data accessibility and security across environments.
What are NetApp’s key terms?
To understand how NetApp works, it’s necessary to know some of its terminology and product selections. The following are some basic terms and products with brief definitions.
Aggregate
An aggregate is a collection of physical disks you can organize and configure to support various performance and security needs. According to NetApp, if your environment contains certain configurations, you’ll need to create aggregates manually. A few of these configurations include flash pool aggregates and MetroCluster configurations.
Cluster MTU
This feature enables you to configure MTU size by using an ONTAP Select multi-node cluster. An MTU is the maximum transmission unit size that specifies the jumbo frame size on 10 Gigabit interfaces as well as 1 Gigabit Ethernet. Using the ifconfig command, you can select the particular MTU size for transmission between a client and storage.
FlexVol Volume
FlexVol volumes are a type of volume that generally connects to each of its containing aggregates. Several FlexVol volumes can receive their storage sources from a single aggregate. Since these volumes are separate from the aggregates, you can dynamically change the size of each FlexVol volume without a disruption in the environment.
Initiator
An initiator is a port for connecting with a LUN. You can select an iSCSI hardware or software adapter or an FC. The ONTAP System Manager enables you to manage initiator groups. If you want to control which LIFs each initiator has access to, you can do this with portsets.
IOPS
IOPS measures how many Input/Output operations per second occur. You would generally use IOPS to measure your storage performance in units of bytes for read or write operations. You’ll sometimes need different IOP limits in various operations that are in the same application.
License Manager
This software component is part of the Deploy administration utility. This is an API you can use to update an IP address when the IP address changes. To generate a file, you need to use the License Lock ID (LLID) and the capacity pool license serial number.
LUN
LUNs are block-based storage objects that you can format in various ways. They work through the FC or iSCSI protocol. ONTAP System Manager is able to help you create LUNS if there is available free space. There are many ways you can use LUNs; for example, you might develop a LUN for a QTree, volume, or aggregate that you already have.
Multiple Cluster Systems
If you need an at-scale system for a growing organization, you’ll want to consider NetApp systems that have multiple clusters. A cluster consists of grouped nodes to create scalable clusters. This is done primarily to use the nodes more effectively and distribute the workload throughout the cluster. An advantage of having clusters is to provide continuous service for users even if an individual node goes offline.
ONTAP Select Cluster
You can create clusters with one, two, four, six, or even eight nodes. A cluster with only one node doesn’t produce any HA capability. Clusters with more than one node, however, will have at least one HA pair.
ONTAP Select Deploy
You can use this administration utility to deploy ONTAP Select clusters. The web user interface provides access to the Deploy utility. The REST API and CLI management shell also provide access.
Qtrees
Qtrees are file systems that are often subdirectories of a primary directory. You might want to use qtrees if you’re managing or configuring quotas. You can create them within volumes when you need smaller segments of each volume. Developing as many as 4,995 qtrees in each internal volume is possible. Internal volumes and qtrees have many similarities. Primary differences include that qtrees can’t support space guarantees or space reservations. Individual qtrees also can’t enable or disable snapshot copies. Clients will see the qtree as a directory when they access that particular volume.
Snapshot Copy
Snapshot copy is a read-only image that captures a moment-in-time of storage system volume. The technology behind ONTAP Snapshot enables the image to take up a minimum of storage space. Instead of copying data blocks, ONTAP creates Snapshot copies by referencing metadata. You can recover LUNS, contents of a volume, or individual files with a Snapshot copy.
SnapMirror
This replication software runs as a part of the Data ONTAP system. SnapMirror can replicate data from a qtree or a source volume. It’s essential to establish a connection between the source and the destination before copying data with SnapMirror. After creating a snapshot copy and copying it to the destination, the result is a read-only qtree or volume containing the same information as the source when it was last updated.
You will want to use SnapMirror in asynchronous, synchronous, or semi-synchronous mode. If at the qtree level, SnapMirror runs only in asynchronous mode. Before setting up a SnapMirror operation, you need a separate license and must enable the correct license on the destination and source systems.
Storage Pools
Storage pools are data containers with the ability to hide physical storage. Storage pools increase overall storage efficiency. The benefit is that you may need to buy fewer disks. The drawback is disk failure can have a ripple effect when several are members of the same storage pool.
System Manager
If you’re just beginning to use NetApp and need a basic, browser-based interface, you may want to consider the OnCommand System Manager. System Manager includes detailed tables, graphs, and charts for tracking past and current performance.
Discover the power of NetApp with LogicMonitor
NetApp provides valuable data and storage services to help your organization access and manage data throughout multi-cloud environments more efficiently. With various products and services, NetApp enables you to put together the data management and storage solutions that meet your organization’s needs.
As a trusted NetApp technology partner, LogicMonitor brings automated, insightful monitoring to your NetApp environment. Transition seamlessly from manual tracking to advanced automated monitoring and gain access to essential metrics like CPU usage, disk activity, and latency analysis—all without configuration work.
With LogicMonitor’s platform, your team can focus on strategic goals, while LogicMonitor ensures efficient and precise monitoring across your NetApp systems, including ONTAP.
Monitoring once provided straightforward insights into IT health: you collected data, identified metrics to monitor, and diagnosed issues as they arose. However, as IT infrastructure evolves with cloud, containerization, and distributed architectures, traditional monitoring can struggle to keep pace. Enter observability, a methodology that not only enhances visibility but also enables proactive issue detection and troubleshooting.
Is observability simply a buzzword, or does it represent a fundamental shift in IT operations? This article will explore the differences between monitoring and observability, their complementary roles, and why observability is essential for today’s IT teams.
In this blog, we’ll cover:
- What is monitoring?
- What is observability?
- Key differences between monitoring vs. observability
- How observability and monitoring work together
- Steps for transitioning from monitoring to full observability
What is monitoring?
Monitoring is the practice of systematically collecting and analyzing data from IT systems to detect and alert on performance issues or failures. Traditional monitoring tools rely on known metrics, such as CPU utilization or memory usage, often generating alerts when thresholds are breached. This data typically comes in the form of time-series metrics, providing a snapshot of system health based on predefined parameters.
Key characteristics of monitoring:
- Reactive by nature: Monitoring often triggers alerts after an issue has already impacted users.
- Threshold-based alerts: Notifications are generated when metrics exceed specified limits (e.g., high memory usage).
- Primary goal: To detect and alert on known issues to facilitate quick response.
An example of monitoring is a CPU utilization alert that may notify you that a server is under load, but without additional context, it cannot identify the root cause, which might reside elsewhere in a complex infrastructure.
What is observability?
Observability goes beyond monitoring by combining data analysis, machine learning, and advanced logging to understand complex system behaviors. Observability relies on the three core pillars—logs, metrics, and traces—to provide a holistic view of system performance, enabling teams to identify unknown issues, optimize performance, and prevent future disruptions.
Key characteristics of observability:
- Proactive approach: Observability enables teams to anticipate and prevent issues before they impact users.
- Unified data collection: Logs, metrics, and traces come together to offer deep insights into system behavior.
- Root cause analysis: Observability tools leverage machine learning to correlate data, helping identify causation rather than just symptoms.
An example of observability: In a microservices architecture, if response times slow down, observability can help pinpoint the exact microservice causing the issue, even if the problem originated from a dependency several layers deep.
For a deeper understanding of what observability entails, check out our article, What is O11y? Observability explained.
Key differences of monitoring vs. observability
Monitoring and observability complement each other, but their objectives differ. Monitoring tracks known events to ensure systems meet predefined standards, while observability analyzes outputs to infer system health and preemptively address unknown issues.
| Aspect | Monitoring | Observability |
| Purpose | To detect known issues | To gain insight into unknown issues and root causes |
| Data focus | Time-series metrics | Logs, metrics, traces |
| Approach | Reactive | Proactive |
| Problem scope | Identifies symptoms | Diagnoses causes |
| Example use case | Alerting on high CPU usage | Tracing slow requests across microservices |
Monitoring vs. observability vs. telemetry vs. APM
Monitoring and observability are not interchangeable terms, but they do work together to achieve a common goal. Monitoring is an important aspect of an observability workflow, as it allows us to track the state of our systems and services actively. However, monitoring alone cannot provide the complete picture that observability offers.
Observability encompasses both monitoring and telemetry as it relies on these components to gather data and analyze it for insights into system behavior. Telemetry provides the raw data that feeds into the analysis process, while monitoring ensures that we are constantly collecting this data and staying informed about any changes or issues in our systems. Without telemetry and monitoring, observability cannot exist.
Application Performance Monitoring (APM) tools give developers and operations teams real-time insights into application performance, enabling quick identification and troubleshooting of issues. Unlike traditional monitoring, APM offers deeper visibility into application code and dependencies.
How monitoring and observability work together
Monitoring and observability are complementary forces that, when used together, create a complete ecosystem for managing and optimizing IT systems. Here’s a step-by-step breakdown of how these two functions interact in real-world scenarios to maintain system health and enhance response capabilities.
Monitoring sets the foundation by tracking known metrics
Monitoring provides the essential baseline data that observability builds upon. Continuously tracking known metrics ensures that teams are alerted to any deviations from expected performance.
- Example: Monitoring tools track key indicators like CPU usage, memory consumption, and response times. When any of these metrics exceed set thresholds, an alert is generated. This serves as the initial signal to IT teams that something may be wrong.
Observability enhances monitoring alerts with contextual depth
Once monitoring generates an alert, observability tools step in to provide the necessary context. Instead of simply reporting that a threshold has been breached, observability digs into the incident’s details, using logs, traces, and correlations across multiple data sources to uncover why the alert occurred.
- Example: If monitoring triggers an alert due to high response times on a specific service, observability traces can reveal dependencies and interactions with other services that could be contributing factors. Analyzing these dependencies helps identify whether the latency is due to a database bottleneck, network congestion, or another underlying service.
Correlating data across monitoring and observability layers for faster troubleshooting
Monitoring data, though essential, often lacks the detailed, correlated insights needed to troubleshoot complex, multi-service issues. Observability integrates data from various layers—such as application logs, user transactions, and infrastructure metrics—to correlate events and determine the root cause more quickly.
- Example: Suppose an e-commerce application shows a spike in checkout failures. Monitoring flags this with an error alert, but observability allows teams to correlate the error with recent deployments, configuration changes, or specific microservices involved in the checkout process. This correlation can show, for instance, that the issue started right after a specific deployment, guiding the team to focus on potential bugs in that release.
Machine learning amplifies alert accuracy and reduces noise
Monitoring generates numerous alerts, some of which are not critical or might even be false positives. Observability platforms, particularly those equipped with machine learning (ML), analyze historical data to improve alert quality and suppress noise by dynamically adjusting thresholds and identifying true anomalies.
- Example: If monitoring detects a temporary spike in CPU usage, ML within the observability platform can recognize it as an expected transient increase based on past behavior, suppressing the alert. Conversely, if it identifies an unusual pattern (e.g., sustained CPU usage across services), it escalates the issue. This filtering reduces noise and ensures that only critical alerts reach IT teams.
Observability enhances monitoring’s proactive capabilities
While monitoring is inherently reactive—alerting when something crosses a threshold—observability takes a proactive stance by identifying patterns and trends that could lead to issues in the future. Observability platforms with predictive analytics use monitoring data to anticipate problems before they fully manifest.
- Example: Observability can predict resource exhaustion in a specific server by analyzing monitoring data on memory usage trends. If it detects a steady increase in memory use over time, it can alert teams before the server reaches full capacity, allowing preventive action.
Unified dashboards combine monitoring alerts with observability insights
Effective incident response requires visibility into both real-time monitoring alerts and in-depth observability insights, often through a unified dashboard. By centralizing these data points, IT teams have a single source of truth that enables quicker and more coordinated responses.
- Example: In a single-pane-of-glass dashboard, monitoring data flags a service outage, while observability insights provide detailed logs, traces, and metrics across affected services. This unified view allows the team to investigate the outage’s impact across the entire system, reducing the time to diagnosis and response.
Feedback loops between monitoring and observability for continuous improvement
As observability uncovers new failure modes and root causes, these insights can refine monitoring configurations, creating a continuous feedback loop. Observability-driven insights lead to the creation of new monitoring rules and thresholds, ensuring that future incidents are detected more accurately and earlier.
- Example: During troubleshooting, observability may reveal that a certain pattern of log events signals an impending memory leak. Setting up new monitoring alerts based on these log patterns can proactively alert teams before a memory leak becomes critical, enhancing resilience.
Key outcomes of the monitoring-observability synergy
Monitoring and observability deliver a comprehensive approach to system health, resulting in:
- Faster issue resolution: Monitoring alerts IT teams to problems instantly, while observability accelerates root cause analysis by providing context and correlations.
- Enhanced resilience: Observability-driven insights refine monitoring rules, leading to more accurate and proactive alerting, which keeps systems stable under increasing complexity.
- Operational efficiency: Unified dashboards streamline workflows, allowing teams to respond efficiently, reduce mean time to resolution (MTTR), and minimize service disruptions.
In short, monitoring and observability create a powerful synergy that supports both reactive troubleshooting and proactive optimization, enabling IT teams to stay ahead of potential issues while maintaining high levels of system performance and reliability.
Steps for transitioning from monitoring to observability
Transitioning from traditional monitoring to a full observability strategy requires not only new tools but also a shift in mindset and practices. Here’s a step-by-step guide to help your team make a seamless, impactful transition:
1. Begin with a comprehensive monitoring foundation
Monitoring provides the essential data foundation that observability needs to deliver insights. Without stable monitoring, observability can’t achieve its full potential.
Set up centralized monitoring to cover all environments—on-premises, cloud, and hybrid. Ensure coverage of all critical metrics such as CPU, memory, disk usage, and network latency across all your systems and applications. For hybrid environments, it’s particularly important to use a monitoring tool that can handle disparate data sources, including both virtual and physical assets.
Pro tip:
Invest time in configuring detailed alert thresholds and suppressing false positives to minimize alert fatigue. Initial monitoring accuracy reduces noise and creates a solid base for observability to build on.
2. Leverage log aggregation to gain granular visibility
Observability relies on an in-depth view of what’s happening across services, and logs are critical for this purpose. Aggregated logs allow teams to correlate patterns across systems, leading to faster root cause identification.
Choose a log aggregation solution that can handle large volumes of log data from diverse sources. This solution should support real-time indexing and allow for flexible querying. Look for tools that offer structured and unstructured log handling so that you can gain actionable insights without manual log parsing.
Pro tip:
In complex environments, logging everything indiscriminately can quickly lead to overwhelming amounts of data. Implement dynamic logging levels—logging more detail temporarily only when issues are suspected, then scaling back once the system is stable. This keeps log data manageable while still supporting deep dives when needed.
3. Add tracing to connect metrics and logs for a complete picture
In distributed environments, tracing connects the dots across services, helping to identify and understand dependencies and causations. Tracing shows the journey of requests, revealing delays and bottlenecks across microservices and third-party integrations.
Adopt a tracing framework that’s compatible with your existing architecture, such as OpenTelemetry, which integrates with many observability platforms and is widely supported. Configure traces to follow requests across services, capturing data on latency, error rates, and processing times at each stage.
Pro tip:
Start with tracing critical user journeys—like checkout flows or key API requests. These flows often correlate directly with business metrics and customer satisfaction, making it easier to demonstrate the value of observability to stakeholders. As you gain confidence, expand tracing coverage to additional services.
4. Introduce machine learning and AIOps for enhanced anomaly detection
Traditional monitoring relies on static thresholds, which can lead to either missed incidents or alert fatigue. Machine learning (ML) in observability tools dynamically adjusts these thresholds, identifying anomalies that static rules might overlook.
Deploy an AIOps (Artificial Intelligence for IT Operations) platform that uses ML to detect patterns across logs, metrics, and traces. These systems continuously analyze historical data, making it easier to spot deviations that indicate emerging issues.
Pro tip:
While ML can be powerful, it’s not a one-size-fits-all solution. Initially, calibrate the AIOps platform with supervised learning by identifying normal versus abnormal patterns based on historical data. Use these insights to tailor ML models that suit your specific environment. Over time, the system can adapt to handle seasonality and load changes, refining anomaly detection accuracy.
5. Establish a single pane of glass for unified monitoring and observability
Managing multiple dashboards is inefficient and increases response time in incidents. A single pane of glass consolidates monitoring and observability data, making it easier to identify issues holistically and in real-time.
Choose a unified observability platform that integrates telemetry (logs, metrics, and traces) from diverse systems, cloud providers, and applications. Ideally, this platform should support both real-time analytics and historical data review, allowing teams to investigate past incidents in detail.
Pro tip:
In practice, aim to customize the single-pane dashboard for different roles. For example, give SREs deep trace and log visibility, while providing executive summaries of system health to leadership. This not only aids operational efficiency but also allows stakeholders at every level to see observability’s value in action.
6. Optimize incident response with automated workflows
Observability is only valuable if it shortens response times and drives faster resolution. Automated workflows integrate observability insights with incident response processes, ensuring that the right people are alerted to relevant, contextualized data.
Configure incident response workflows that trigger automatically when observability tools detect anomalies or critical incidents. Integrate these workflows with collaboration platforms like Slack, Teams, or PagerDuty to notify relevant teams instantly.
Pro tip:
Take the time to set up intelligent incident triage. Route different types of incidents to specialized teams (e.g., network, application, or database), each with their own protocols. This specialization makes incident handling more efficient and prevents delays that could arise from cross-team handoffs.
7. Create a feedback loop to improve monitoring with observability insights
Observability can reveal recurring issues or latent risks, which can then inform monitoring improvements. By continually refining monitoring based on observability data, IT teams can better anticipate issues, enhancing the reliability and resilience of their systems.
Regularly review observability insights to identify any new patterns or potential points of failure. Set up recurring retrospectives where observability data from recent incidents is analyzed, and monitoring configurations are adjusted based on lessons learned.
Pro tip:
Establish a formal feedback loop where observability engineers and monitoring admins collaborate monthly to review insights and refine monitoring rules. Observability can identify previously unknown thresholds that monitoring tools can then proactively track, reducing future incidents.
8. Communicate observability’s impact on business outcomes
Demonstrating the tangible value of observability is essential for maintaining stakeholder buy-in and ensuring continued investment.
Track key performance indicators (KPIs) such as MTTR, incident frequency, and system uptime, and correlate these metrics with observability efforts. Share these results with stakeholders to highlight how observability reduces operational costs, improves user experience, and drives revenue.
Pro tip:
Translating observability’s technical metrics into business terms is crucial. For example, if observability helped prevent an outage, quantify the potential revenue saved based on your system’s downtime cost per hour. By linking observability to bottom-line metrics, you reinforce its value beyond IT.
Embrace the power of observability and monitoring
Observability is not just an extension of monitoring—it’s a fundamental shift in how IT teams operate. While monitoring is essential for tracking known issues and providing visibility, observability provides a deeper, proactive approach to system diagnostics, enabling teams to innovate while minimizing downtime.
To fully realize the benefits of observability, it’s important to combine both monitoring and observability tools into a cohesive, holistic approach. By doing so, businesses can ensure that their systems are not only operational but also resilient and adaptable in an ever-evolving digital landscape.
Logging is critical for gaining valuable application insights, such as performance inefficiencies and architectural structure. But creating reliable, flexible, and lightweight logging solutions isn’t the easiest task—which is where Docker helps.
Docker containers are a great way to create lightweight, portable, and self-contained application environments. They also give IT teams a way to create impermanent and portable logging solutions that can run on any environment. Because logging is such a crucial aspect of performance, Docker dual logging is more beneficial in complex, multi-container setups that depend on reliable log management for troubleshooting and auditing.
Docker dual logging allows the capture of container logs in two separate locations at the same time. This approach ensures log redundancy, improved compliance, and enhanced operating system (like Windows, Linux, etc.) observability by maintaining consistent log data across distributed environments.
This guide covers the essentials of Docker logging, focusing on implementing Docker dual logging functionality to optimize your infrastructure.
What is a Docker container?
A Docker container is a standard unit of software that wraps up code and all its dependencies so the program can be moved from one environment to another, quickly and reliably.
Containerized software, available for Linux and Windows-based applications, will always run the same way despite the infrastructure.
Containers encapsulate software from its environment, ensuring that it performs consistently despite variations between environments — for example, development and staging.
Docker container technology was introduced as an open-source Docker Engine in 2013.
What is a Docker image?
A Docker image is a lightweight, standalone, executable software package that contains everything required to run an application: code, system tools, system libraries, and settings.
In other words, an image is a read-only template with instructions for constructing a container that can operate on the Docker platform. It provides an easy method to package up programs and preset server environments that you can use privately or openly with other Docker users.
What is Docker logging?
Docker logging refers to the process of capturing and managing logs generated by containerized applications. Logs provide critical insights into system behavior, helping you troubleshoot issues, monitor performance, and ensure overall application log health.
Combined with monitoring solutions, you can maintain complete visibility into your containerized environments, helping you solve problems faster and ensure reliability. Using other data insights, you can examine historical data to find trends and anticipate potential problems.
Docker container logs
What are container logs?
Docker container logs, in a nutshell, are the console output of running containers. They specifically supply the stdout and stderr streams running within a container.
As previously stated, Docker logging is not the same as logging elsewhere. Everything that is written to the stdout and stderr streams in Docker is implicitly forwarded to a driver, allowing accessing and writing logs to a file.
Logs can also be viewed in the console. The Docker logs command displays information sent by a currently executing container. The docker service logs command displays information by all containers members of the service.
What is a Docker logging driver?
The Docker logging drivers gather data from containers and make it accessible for analysis.
If no additional log-driver option is supplied when a container is launched, Docker will use the json-file driver by default. A few important notes on this:
- Log-rotation is not performed by default. As a result, log files kept using the json-file logging driver can consume a significant amount of disk space for containers that produce a large output, potentially leading to disk space depletion.
- Docker preserves the json-file logging driver — without log-rotation — as the default to maintain backward compatibility with older Docker versions and for instances when Docker is used as a Kubernetes runtime.
- The local driver is preferable because it automatically rotates logs and utilizes a more efficient file format.
Docker also includes logging drivers for sending logs to various services — for example, a logging service, a log shipper, or a log analysis platform. There are many different Docker logging drivers available. Some examples are listed below:
- syslog — A long-standing and widely used standard for logging applications and infrastructure.
- journald — A structured alternative to Syslog’s unstructured output.
- fluentd — An open-source data collector for unified logging layer.
- awslogs — AWS CloudWatch logging driver. If you host your apps on AWS, this is a fantastic choice.
You do, however, have several alternative logging driver options, which you can find in the Docker logging docs.
Docker also allows logging driver plugins, enabling you to write your Docker logging drivers and make them available over Docker Hub. At the same time, you can use any plugins accessible on Docker Hub.
Logging driver configuration
To configure a Docker logging driver as the default for all containers, you can set the value of the log-driver to the name of the logging driver in the daemon.json configuration file.
This example sets the default logging driver to the local driver:
{
“log-driver”: “local”
}Another option is configuring a driver on a container-by-container basis. When you initialize a container, you can use the –log-driver flag to specify a different logging driver than the Docker daemon’s default.
The code below starts an Alpine container with the local Docker logging driver:
docker run -it –log-driver local alpine ashThe docker info command will provide you with the current default logging driver for the Docker daemon.
Docker Logs With Remote Logging Drivers
Previously, the Docker logs command could only be used with logging drivers that supported containers utilizing the local, json-file, or journald logging drivers. However, many third-party Docker logging drivers did not enable reading logs from Docker logs locally.
When attempting to collect log data automatically and consistently, this caused a slew of issues. Log information could only be accessed and displayed in the format required by the third-party solution.
Starting with Docker Engine 20.10, you can use docker logs to read container logs independent of the logging driver or plugin that is enabled.
Dual logging requires no configuration changes. Docker Engine 20.10 later allows double logging by default if the chosen Docker logging driver does not support reading logs.
Where are Docker logs stored?
Docker keeps container logs in its default place, /var/lib/docker/. Each container has a log that is unique to its ID (the full ID, not the shorter one that is generally presented), and you may access it as follows:
/var/lib/docker/containers/ID/ID-json.log
docker run -it –log-driver local alpine ashWhat are the Docker logging delivery modes?
Docker logging delivery modes refer to how the container balances or prioritizes logging against other tasks. The available Docker logging delivery modes are blocking and non-blocking. Both the options can be applied regardless of what Docker logging driver you selected.
Blocking mode
When in blocking mode, the program will be interrupted whenever a message needs to be delivered to the driver.
The advantage of the blocking mode is that all logs are forwarded to the logging driver, even though there may be a lag in your application’s performance. In this sense, this mode prioritizes logging against performance.
Depending on the Docker logging driver you choose, your application’s latency may vary. For example, the json-file driver, which writes to the local filesystem, produces logs rapidly and is unlikely to block or create a significant delay.
On the contrary, Docker logging drivers requiring the container to connect to a remote location may block it for extended periods, resulting in increased latency.
Docker’s default mode is blocking.
When to use the blocking mode?
The json-file logging driver in blocking mode is recommended for most use situations. As mentioned before, the driver is quick since it writes to a local file. Therefore it’s generally safe to use it in a blocking way.
The blocking mode should also be used for memory-hungry programs requiring the bulk of the RAM available to your containers. The reason is that if the driver cannot deliver logs to its endpoint due to a problem such as a network issue, there may not be enough memory available for the buffer if it’s in non-blocking mode.
Non-blocking
The non-blocking Docker logging delivery mode will not prevent the program from running to provide logs. Instead of waiting for logs to be sent to their destination, the container will store logs in a buffer in its memory.
Though the non-blocking Docker logging delivery mode appears to be the preferable option, it also introduces the possibility of some log entries being lost. Because the memory buffer in which the logs are saved has a limited capacity, it might fill up.
Furthermore, if a container breaks, logs may be lost before being released from the buffer.
You may override Docker’s default blocking mode for new containers by adding an log-opts item to the daemon.json file. The max-buffer-size, which refers to the memory buffer capacity mentioned above, may also be changed from the 1 MB default.
{
“log-driver”: “local”,
“log-opts”: {
“mode”: “non-blocking”
}
}Also, you can provide log-opts on a single container. The following example creates an Alpine container with non-blocking log output and a 4 MB buffer:
docker run -it –log-opt mode=non-blocking –log-opt max-buffer-size=4m alpineWhen to use non-blocking mode?
Consider using the json-file driver in the non-blocking mode if your application has a big I/O demand and generates a significant number of logs.
Because writing logs locally is rapid, the buffer is unlikely to fill quickly. If your program does not create spikes in logging, this configuration should handle all of your logs without interfering with performance.
For applications where performance is more a priority than logging but cannot use the local file system for logs — such as mission-critical applications — you can provide enough RAM for a reliable buffer and use the non-blocking mode. This setting should ensure the performance is not hampered by logging, yet the container should still handle most log data.
Why Docker logging is different from traditional logging
Logging in containerized environments like Docker is more complex than in traditional systems due to the temporary and distributed nature of containers. Docker containers generate multiple log streams, often in different formats, making standard log analysis tools less effective and debugging more challenging compared to single, self-contained applications.
Two key characteristics of Docker containers contribute to this complexity:
- Temporary containers: Docker containers are designed to be short-lived, meaning they can be stopped or destroyed at any time. When this happens, any logs stored within the container are lost. To prevent data loss, it’s crucial to use a log aggregator that collects and stores logs in a permanent, centralized location. You may use a centralized logging solution to aggregate log data and use data volumes to store persistent data on host devices.
- Multiple logging layers: Docker logging involves log entries from individual containers and the host system. Managing these multi-level logs requires specialized tools that can gather and analyze data from all levels and logging formats effectively, ensuring no critical information is missed. Containers may also generate large volumes of log data, which means traditional log analysis tools may struggle with the sheer amount of data.
Understanding Docker dual logging
Docker dual logging involves sending logs to two different locations simultaneously. This approach ensures that log data is redundantly stored, reducing the risk of data loss and providing multiple sources for analysis. Dual logging is particularly valuable in environments where compliance and uptime are critical.
Benefits of Docker dual logging
- Redundancy: Dual logging ensures that log messages are preserved even if one logging system fails and logging continues in case of service failure.
- Enhanced troubleshooting: With logs available in two places, cross-referencing data leads to diagnosing issues more effectively.
- Compliance: For industries with strict data retention and auditing requirements, dual logging helps meet these obligations by providing reliable log storage across multiple systems.
Docker dual logging in action
Docker dual logging is widely implemented in various industries to improve compliance, security, and system reliability. By implementing Docker dual logging, you can safeguard data, meet regulatory demands, and optimize your infrastructure. Below are some real-world examples of how organizations benefit from dual logging:
- E-commerce compliance: A global e-commerce company uses dual logging to meet data retention laws by storing log files both locally and in the cloud, ensuring regulatory compliance (such as GDPR and CCPA) and audit readiness.
- Financial institution security: A financial firm uses dual logging to enhance security by routing logs to secure on-premise and cloud systems, quickly detecting suspicious activities, aiding forensic analysis, and minimizing data loss.
- SaaS uptime and reliability: A SaaS provider leverages dual logging to monitor logs across local and remote sites, minimizing downtime by resolving issues faster and debugging across distributed systems to ensure high service availability.
How to implement Docker dual logging
Implementing dual logging in the Docker engine involves configuring containers to use multiple logging drivers. For example, logs can be routed to both a local JSON file and a remote logging service like AWS CloudWatch. Here’s a simple configuration file example:
bash
copy code
docker run -d \
--log-driver=json-file \
--log-driver=fluentd \
--log-opt fluentd-address=localhost:24224 \
your-container-imageThe specific logging driver and other settings will vary based on your specific configuration. Look at your organization’s infrastructure to determine the driver names and the address of the logging server.
This setup ensures that logs are stored locally while also being sent to a centralized log management service. If you’re using Kubernetes to manage and monitor public cloud environments, you can benefit from the LogicMonitor Collector for better cloud monitoring.
Docker Daemon Logs
What are Daemon logs?
The Docker platform generates and stores logs for its daemons. Depending on the host operating system, daemon logs are written to the system’s logging service or a log file.
If you only collected container logs, you would gain insight into the state of your services. On the other hand, you need to be informed of the state of your entire Docker platform, and the daemon logs exist for that reason as they provide an overview of your whole microservices architecture.
Assume a container shuts down unexpectedly. Because the container terminates before any log events can be captured, we cannot pinpoint the underlying cause using the docker logs command or an application-based logging framework.
Instead, we may filter the daemon log for events that contain the container name or ID and sort by timestamp, which allows us to establish a chronology of the container’s life from its origin through its destruction.
The daemon log also contains helpful information about the host’s status. If the host kernel does not support a specific functionality or the host setup is suboptimal, the Docker daemon will note it during the initialization process.
Depending on the operating system settings and the Docker logging subsystem utilized, the logs may be kept in one of many locations. In Linux, you can look at the journalctl records:
sudo journalctl -xu docker.serviceAnalyzing Docker logs
Log data must be evaluated before it can be used. When you analyze log data, you’re hunting for a needle in a haystack.
You’re typically hunting for that one line with an error among thousands of lines of regular log entries. A solid analysis platform is required to determine the actual value of logs. Log collecting and analysis tools are critical. Here are some of the options.
Fluentd
Fluentd is a popular open-source solution for logging your complete stack, including non-Docker services. It’s a data collector that allows you to integrate data gathering and consumption for improved data utilization and comprehension.
ELK
ELK is the most widely used open-source log data analysis solution. It’s a set of tools:ElasticSearch for storing log data, Logstash for processing log data, and Kibana for displaying data via a graphical user interface.
ELK is an excellent solution for Docker log analysis since it provides a solid platform maintained by a big developer community and is free.
Advanced log analysis tools
With open-source alternatives, you must build up and manage your stack independently, which entails allocating the necessary resources and ensuring that your tools are highly accessible and housed on scalable infrastructure. It can necessitate a significant amount of IT resources as well.
That’s where more advanced log analysis platforms offer tremendous advantages. For example, tools like LogicMonitor’s SaaS platform for log intelligence and aggregation can give teams quick access to contextualized and connected logs and metrics in a single, unified cloud-based platform.
These sophisticated technologies leverage the power of machine learning to enable companies to reduce troubleshooting, streamline IT operations, and increase control while lowering risk.
Best practices for Docker dual logging
Docker dual logging offers many benefits. But to get the most out of it, you’ll need to implement best practices to build a reliable logging environment. Use the best practices below to get started.
- Monitor log performance: Regularly check the performance impact of dual logging on containers by gathering metrics like CPU usage and network bandwidth, and adjust configurations as necessary.
- Ensure log security: Use encryption and secure access controls when transmitting logs to remote locations, and verify your controls comply with regulations.
- Automate log management: implement automated processes to manage, review, and archive logs from devices ingesting logs to prevent storage issues.
Analyzing Docker logs in a dual logging setup
When logs are stored in two places, analyzing them becomes more complicated. Using log aggregation tools like Fluentd or ELK to collect and analyze logs from both sources provides a comprehensive view of a system’s behavior. This dual approach can significantly increase the ability to detect and resolve your issues quickly.
Overview of Docker logging drivers
Docker supports various logging drivers, each suited to different use cases. Drivers can be mixed and matched when implementing dual logging to achieve the best results for whole environments. Common drivers include:
- json-file: Stores logs in a JSON format on the local filesystem
- Fluentd: Sends logs to a Fluentd service, ideal for centralized logging
- awslogs: Directs logs to AWS CloudWatch, suitable for cloud-based monitoring
- gelf: Sends logs to in Graylog Extended Log Format for GrayWatch and Logstash endpoints
Tools and integration for Docker dual logging
To fully leverage Docker dual logging, integrating with powerful log management tools is essential. These popular tools enhance Docker dual logging by providing advanced features for log aggregation, analysis, and visualization.
- ELK Stack: An open-source solution comprising Elasticsearch, Logstash, and Kibana, ideal for collecting, searching, and visualizing log data.
- Splunk: A platform offering comprehensive log analysis and real-time monitoring capabilities suitable for large-scale environments.
- Graylog: A flexible, open-source log management tool that allows centralized logging and supports various data sources.
Conclusion
Docker dual logging is a powerful strategy for ensuring reliable, redundant log management in containerized environments. Implementing dual logging enhances your system’s resilience, improves troubleshooting capabilities, and meets compliance requirements with greater ease. As containerized applications continue to grow in complexity and scale, implementing dual logging will be critical for maintaining efficient infrastructures.
