If you poll IT operations folks on what keeps them up at night, I’m willing to bet that security would make it to the top of the list. Security is a hot topic these days. It’s difficult to open any publication and not see an article about a major hack (such as Yahoo’s recent 1 billion user account hack) or some other security issue. The complex IT world that we live in makes maintaining security practices even more difficult.
Here at LogicMonitor, security is also a primary concern. We jump through major hoops to make sure that we as a company are adhering to security best practices and that our monitoring platform provides the options that our customers need to keep things secure on their end.

Historically we have provided two methods for logging into a LogicMonitor account: username/password (subject to password strength verification) and single sign-on (SSO). SSO is a great way for companies to have one login for all their tools and integrate with their internal IT system. At LogicMonitor, we use that very method to log into all of our internal tools and LogicMonitor accounts (using Okta). Single sign-on is usually secured with multi-factor authentication too, which is a great way to keep your company secure.
So, if many of our customers already use SSO, why add two-factor authentication (2FA) to LogicMonitor’s login?
There are a couple of reasons for this. First off, not all companies utilize a SAML-compliant SSO and these companies were asking for 2FA. In addition, our large Service Provider (SP) customers and their clients likely have separate single SSOs, and both may need access to LogicMonitor. LogicMonitor can’t authenticate against both the Service Provider’s SSO system, and the end customers. This meant that the end users of SP customers would be constrained to username/password authentication, which is not ideal. We had room to improve our security here, so we did.
This takes me to the next part of my story. When we made the decision to implement 2FA for our product we had an important decision to make: build or buy? The answer was simple: don’t reinvent the wheel if you don’t have to (one of the core ideals of LogicMonitor). So we decided to buy! The next step was to pick a service. After looking at all the pros and cons of different systems, we decided to go with Twilio’s Authy:
- Pros: supports SMS/voice codes, can de-register users, OneTouch, Cloud-Sync between devices, System Recovery, Desktop App, we already use Twilio for Alert Delivery
- Cons: not free, no QR code scan
The second we started specifying the 2FA project, Authy had a technical contact for us (who was very punctual and responded quickly when we had questions), their API documentation was great, and the implementation was straightforward.
So, you’re a LogicMonitor user and you’re pumped up about 2FA and you want to set it up right now! How do you do it?
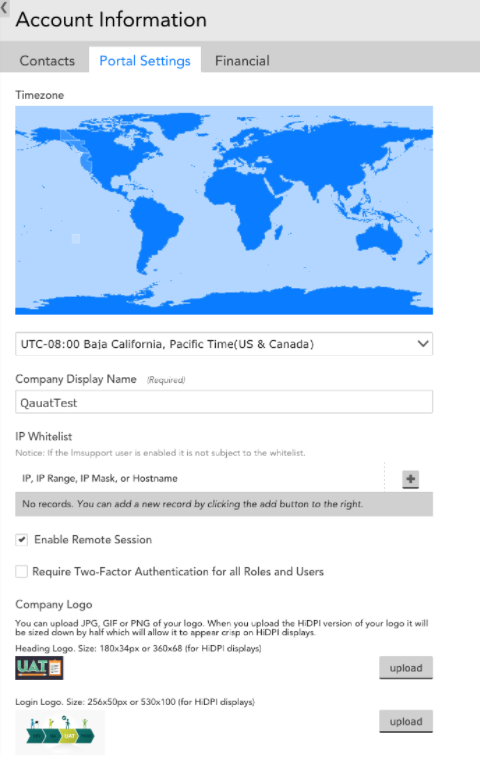
Two-factor authentication can be enabled at multiple levels in your account. You can require it for all users in your account at the Account Information/Portal Settings tab, or you can require it for all users in a particular role, or require it only for specific users.
Note that two-factor authentication defers to single sign-on. This means that if one has enabled “strict” SSO access, users will not be able to access LogicMonitor via two-factor authentication. Below are some pictures that should help with the process.
Account Wide
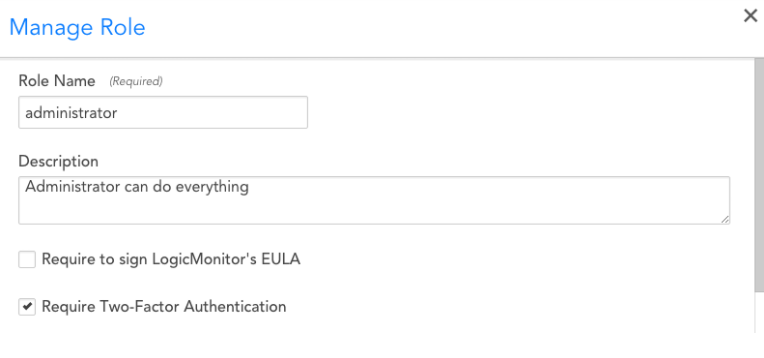
Per User
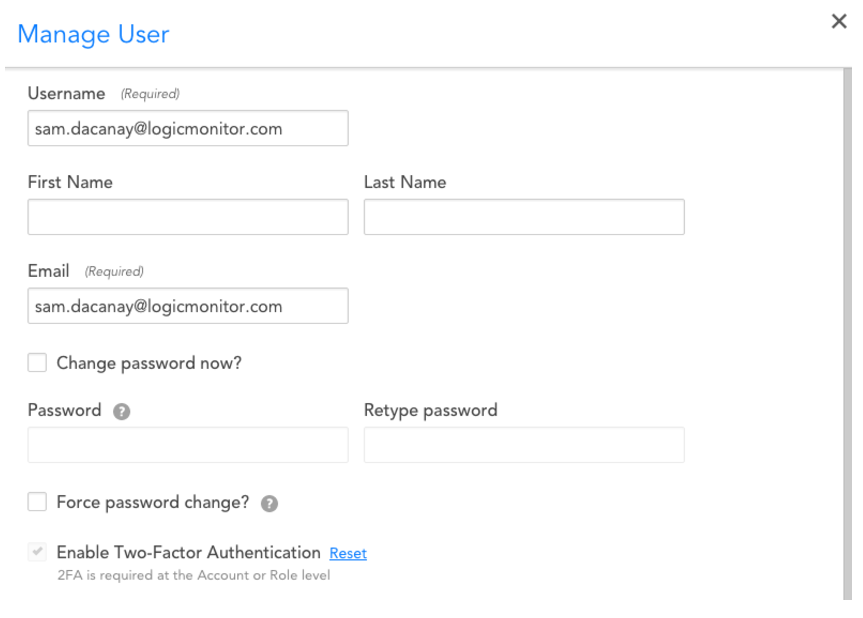
Once required, the next time a user logs in, they will be prompted to validate their device, then voila, 2FA is enabled!
Each time a 2FA-enabled user logs in, they have a couple of options for how to perform that second step of authentication:
Option 1) OneTouch – in the Authy application (on iOS or Android), a single-click approve or deny button
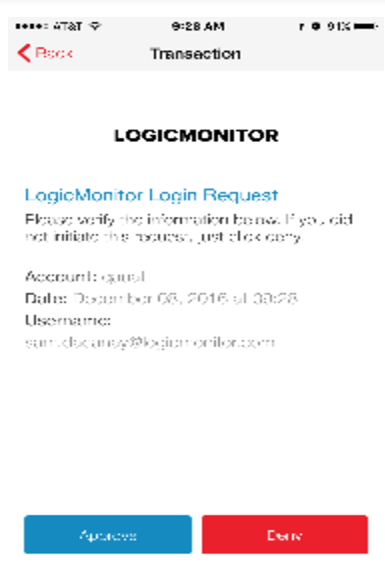
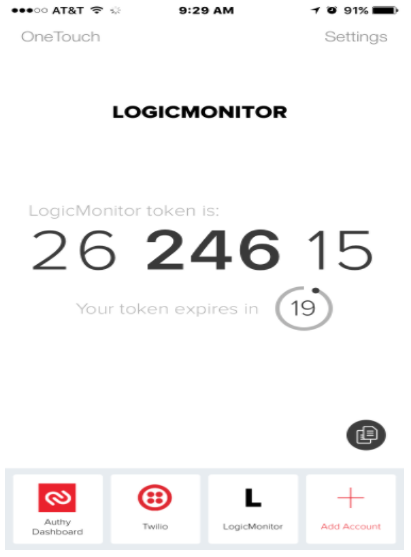
Option 2) SoftCode – in the Authy application (OTP password, changes every 20 seconds)
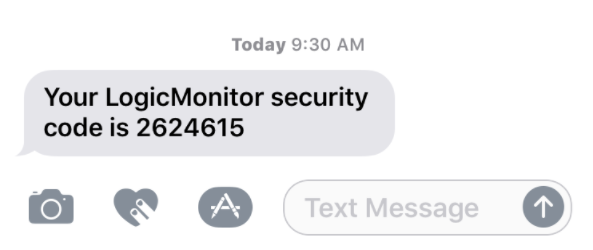
Option 3) SMS/Voice Token – Don’t have a good signal? Log in with a cod
e that is texted or sent via phone call.
The 2FA feature is available in Release v.83 (our last one in 2016). If you have any questions about how this works feel free to check out our help documentation or contact our support team.
Happy Authenticating!

Subscribe to our blog
Get articles like this delivered straight to your inbox