Adding Microsoft Azure Cloud Monitoring
Last updated on 28 April, 2024Monitor the state of your Azure deployment, underlying services, and license usage. Monitoring your Azure environment with LogicMonitor helps you to manage performance and identify potential faults.
Requirements
Your LogicMonitor account registered as an App in Microsoft Azure and the following credentials:
- Azure Tenant ID–Directory (tenant) ID from Azure > App Registrations > Overview.
- Azure Client ID– Application (client) ID from Azure > App Registrations > Overview.
- Azure Secret Key–Value from Azure > App Registrations > Certificates & Secrets > Client Secrets.
For more information, see How to register apps in Microsoft Azure documentation.
Adding Your Azure Environment to LogicMonitor
In LogicMonitor, add the required information about your Azure App Registration.
1. Navigate to Resources > Add > Cloud Account.
Note: If you’re using the New UI Preview toggle, go to Resources > Add [+] > Cloud and SaaS.
2. Select Azure > Add.
3. On the Name page, enter a Name and Description for your Azure account. These fields determine how your Azure resource is displayed throughout the LogicMonitor environment.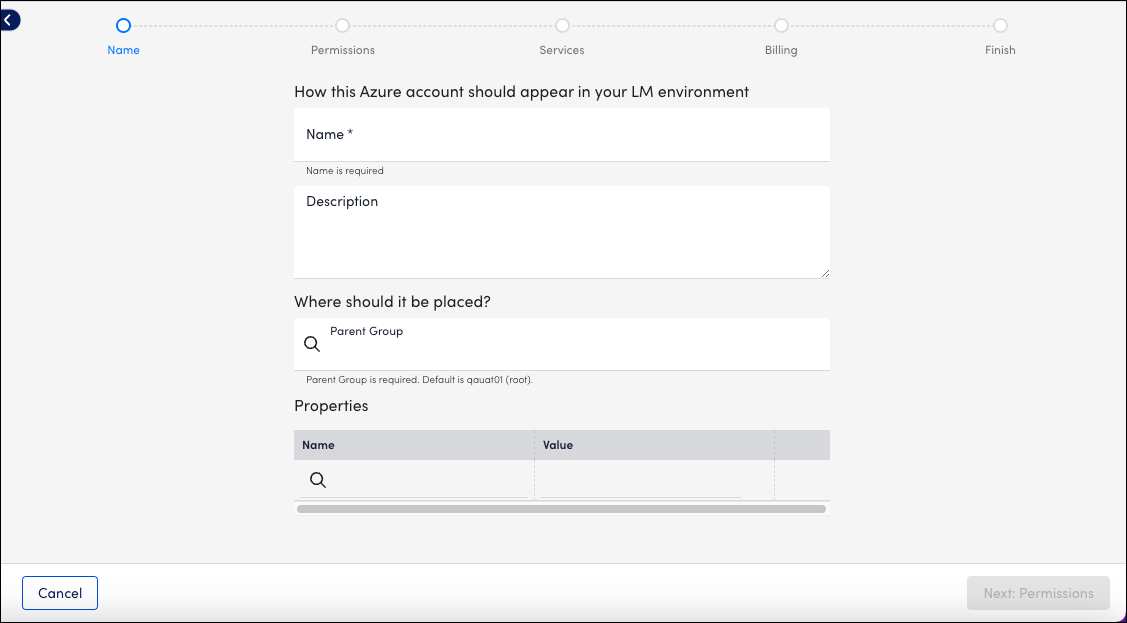
4. To place the new resource into an existing group, select the group from Parent Group field. You can type to search. The default value is root, or the first level of the Resources Tree.
5. (Optional) You can enter key-value pair properties by entering a Name and Value. Or, you can select from a list of existing properties. For more information, see Instance and Resource Properties.
6. Select Next: Permissions.
7. On the Permissions page, enter the Azure Tenant ID, Azure Client ID, and Azure Secret Key.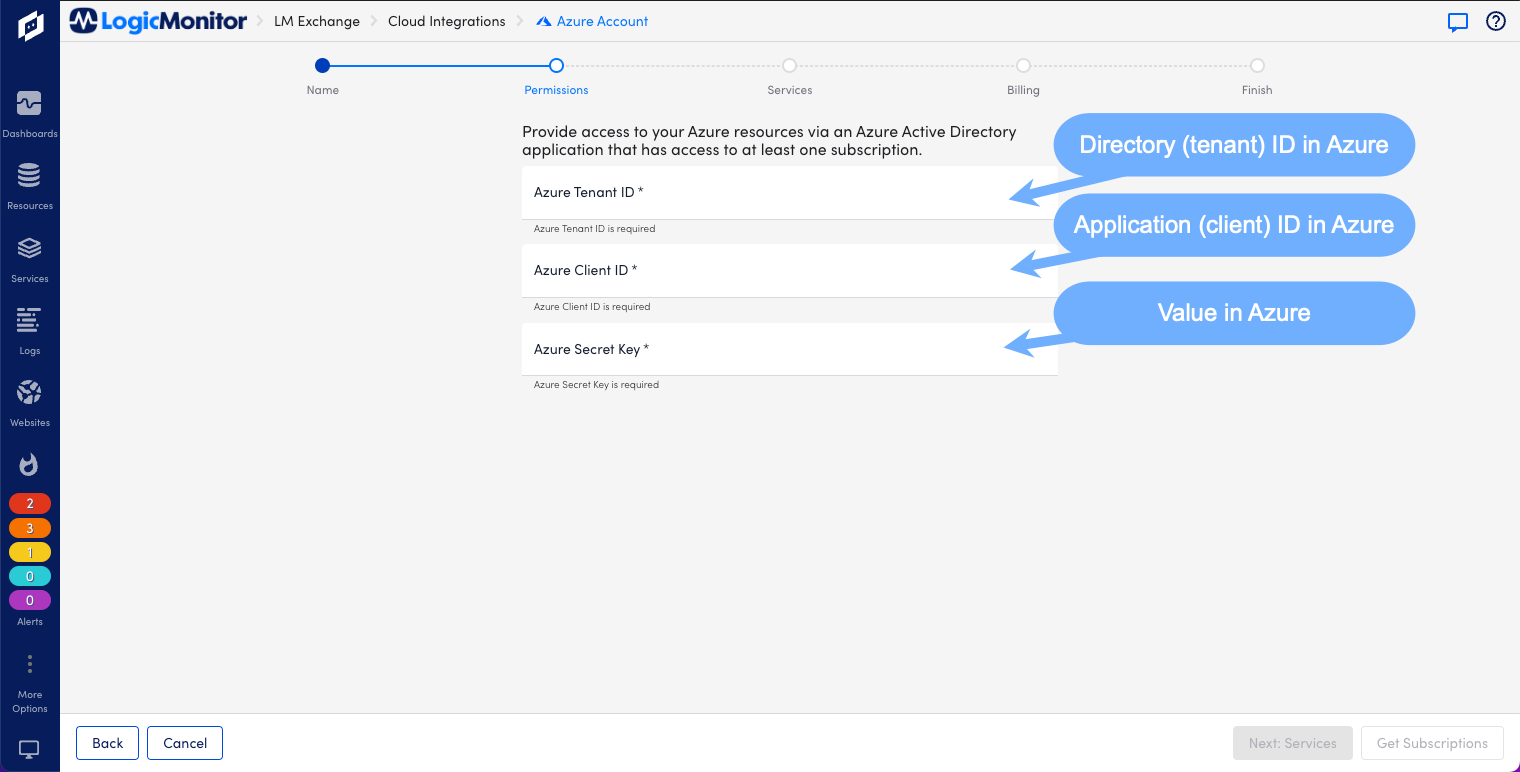

8. Select Get Subscriptions. All subscriptions available to LogicMonitor based on the permissions you’ve configured are listed. If you don’t see the subscriptions you expect, verify that the application you created in Azure has reader permissions for those subscriptions.
9. Select Next: Services.
10. On the Services page, enable or disable the Azure services listed.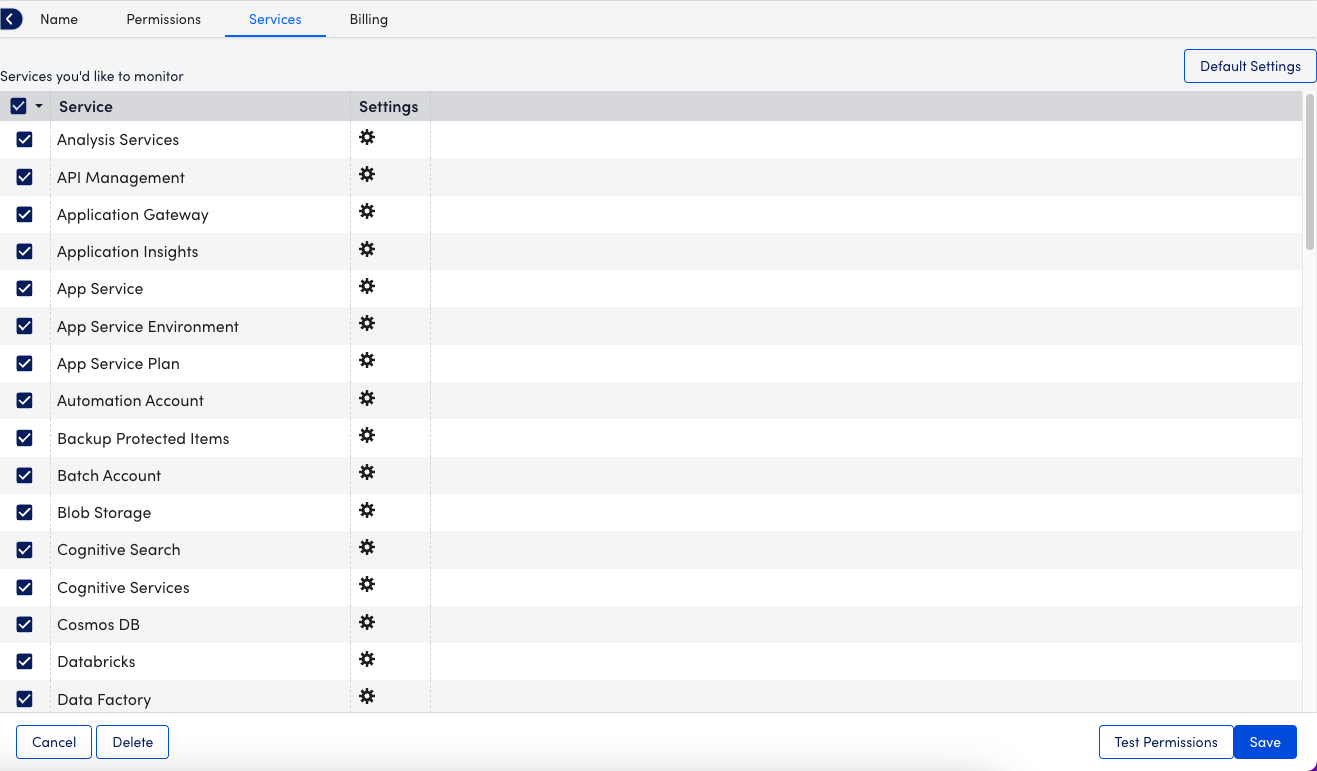

Note: If you’re adding LogicMonitor services for Backup Protected Items or Recovery Protected Items, you need to make configuration changes to the Recovery Service Vault and Log Analytics Workspace in Microsoft Azure. For more information, see Forwarding Backup and Recovery Events.
11. Select Test Permissions to authenticate.
12. Select Next: Billing.
13. On the Billing page, enter the Subscriptions ID, Offer ID, and Monthly Billing Date. 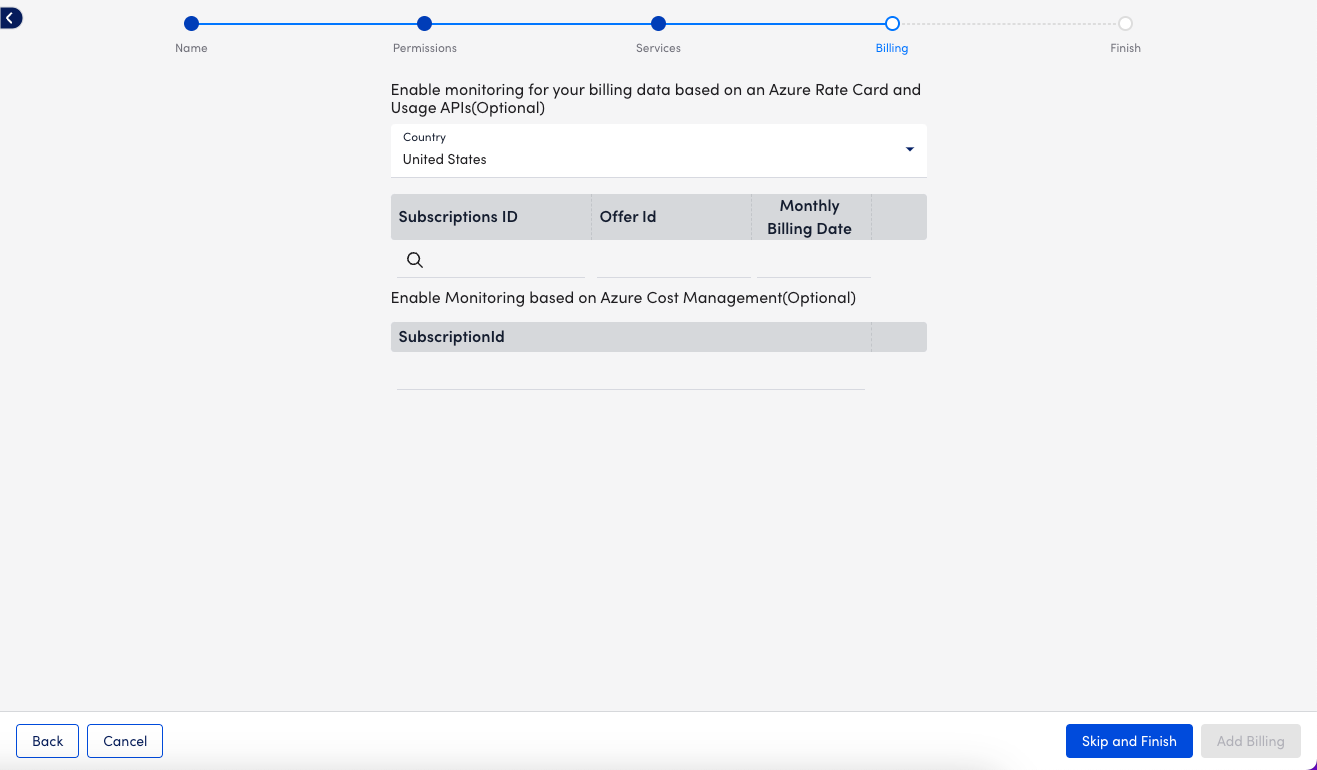

Note: You have the option to provide Billing details using Azure Rate Card or Azure Cost Management. LogicMonitor recommends using Azure Cost Management whenever possible. For Azure Cost Management, enter the Subscription ID from Azure > Subscriptions > Overview. For Rate Card, go to Azure > Subscriptions > Settings > Billing Properties > Microsoft Azure Plan to view your plan’s Subscription ID, Offer ID, and Monthly Billing Date. For more information, see Monitoring Azure Billing.
14. Select Add Billing and then select View Azure Resources to finish.
Configuring Azure Services in LogicMonitor
- Navigate to Resources and select the Azure resource that you added.
- Select Manage and then select the Services tab.
- Select Default Settings.
- On the Global Settings tab:
- NetScan Frequency: Select the preferred frequency for scheduling NetScans.
- Automatically delete terminated Azure resources if they are no longer available in the cloud portal: Enable to automatically remove “dead” instances. You can also select whether this happens immediately or after a specified period during, where no data is received for the instance. This does not remove resources terminated prior to adjusting this setting. These resources must be deleted manually.
- Automatically disable alerting for terminated Azure resources if they are no longer available in the cloud portal: Select this option to disable alerting for terminated instances. This ensures that you will not receive any alerts once instances are terminated if they are not scheduled to be automatically deleted.
Note: LogicMonitor intelligently and automatically stops Azure Monitor API data collection once instances are terminated. This option ensures that you do not receive alerts for traditional Collector DataSources like Ping.
- In the Monitored Regions section, you can enable or disable the regions that you want to monitor.
- Select the Tags tab. To monitor Azure instances for a particular service, you can tag those instances from your Azure portal and then apply a tag filter in LogicMonitor. If you specify a tag filter, only Azure resources that meet the filter criteria will be added to your LogicMonitor account. The criteria is as follows:
- You can use glob expressions with the tag filter. For example:
tag value = prod* - Resources are discovered when they contain one or more tags specified with an include operation, and not with any of the exclude tags.
- The tag filter is case sensitive.
- You can use glob expressions with the tag filter. For example:
- Select Save.
Note: For a list of Azure services monitored, see Cloud Services and Resource Units.
