Kubernetes Monitoring Considerations and Required Permissions
Last updated - 19 July, 2023
Kubernetes Monitoring Considerations
- LM Container treats each Kubernetes object instance as a device.
- Our Kubernetes integration is Container Runtime Interface (CRI) agnostic. For more information, see Container Runtime Interface from Kubernetes documentation.
- LM Container officially supports the most recent five versions of Kubernetes at any given time and aims to offer support for new versions within 60 days of the official release. For more information, see Support Matrix for Kubernetes Monitoring.
- All Kubernetes Clusters added are displayed on the Resources page. For more information, see Adding Kubernetes Cluster Using LogicMonitor Web Portal.
Kubernetes Monitoring Dependencies
- LM Container Helm Chart — Unified LM Container Helm chart allows you to install all the services necessary to monitor your Kubernetes cluster, including Argus, Collectorset-Controller, and the kube-state-metrics (KSM) service.
- Argus— Uses LogicMonitor’s API to add Nodes, Pods, and Services into monitoring.
- Collectorset-Controller— Manages one or more Dockerized LogicMonitor Collectors for data collection. Once Kubernetes Cluster resources are added to LogicMonitor, data collection starts automatically. Data is collected for Nodes, Pods, Containers, and Services via the Kubernetes API. Additionally, standard containerized applications (e.g. Redis, MySQL, etc.) will be automatically detected and monitored.
- Dockerized Collector— An application used for data collection.
- Kube-state-metrics (KSM) Service— A simple service that listens to the Kubernetes API server and generates metrics about the state of the objects.
The following image displays how LogicMonitor’s application runs in your cluster as a pod.
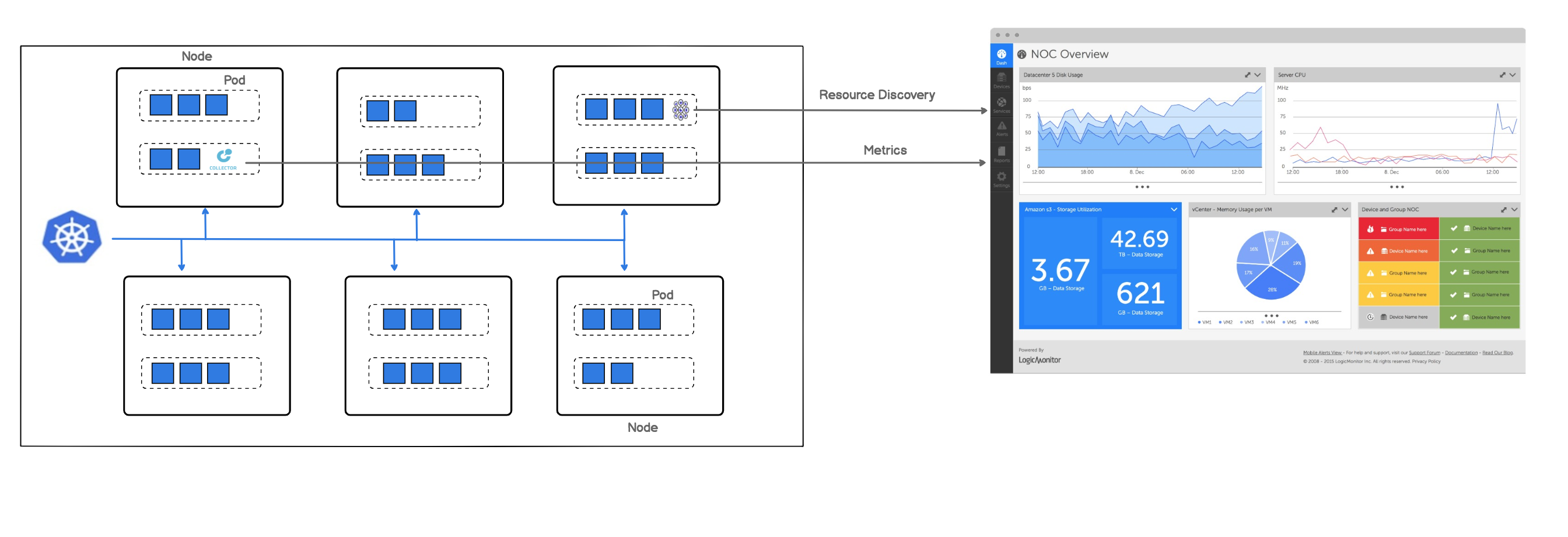
Note: LogicMonitor’s Kubernetes monitoring integration is an add-on feature called LM Container. You may contact your Customer Success Manager (CSM) for more information.
LogicMonitor Portal Permissions
- You should have manage permissions of:
- Settings:
- LogicModules
- Minimum one dashboard group.
- Minimum one resource group.
- Minimum one collector group.
Resources are created if the hosts running in your clusters do not already exist in monitoring.
- Settings:
- You should have view permissions for all the collector groups.
- For creating API tokens for authentication purposes, ensure to check the Allow Creation of API Token checkbox under Settings > User Profile. Any user except an out-of-the-box administrator user role can create API tokens. For more information, see API Tokens.
- Best to install the LM Container from LM portal with the Administrator user role. For more information, see Roles.
Kubernetes Cluster Permissions
There are minimum permissions that are required to install the LM Container.
For creating ClusterRole, do the following:
- Create and save a cluster-role.yaml file with the following configuration:
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: lm-container-min-permissions
rules:
- apiGroups:
- ""
resources:
- "*"
verbs:
- get
- list
- create
- apiGroups:
- ""
resources:
- configmaps
verbs:
- "*"
- apiGroups:
- apps
resources:
- deployments
- statefulsets
- replicasets
verbs:
- get
- list
- create
- apiGroups:
- rbac.authorization.k8s.io
resources:
- clusterroles
- clusterrolebindings
- roles
- rolebindings
verbs:
- "*"
- apiGroups:
- apiextensions.k8s.io
resources:
- customresourcedefinitions
verbs:
- "*"
- apiGroups:
- "*"
resources:
- collectorsets
verbs:
- "*"- Enter the following command:
kubectl apply -f cluster-role.yaml- Run the following command to create cluster-role-binding to give view-only permissions of all the resources for a specific user.
kubectl create clusterrolebinding role-binding-view-only --clusterrole view --user <user-name>- Run the following command to create cluster-role-binding to give permissions to specific user to install LM container components.
kubectl create clusterrolebinding role-binding-lm-container --clusterrole lm-container-min-permissions --user <user-name>For more information on LM Container installation, see Installing the LM Container Helm Chart or Installing LM Container Chart using CLI.


