The ICMP Discovery Method
Last updated - 28 February, 2023
The ICMP ping discovery method pings and checks for specified open ports on all IP addresses you specify. As discussed next, several unique settings must be configured, under the ICMP Discovery Rules section, when you use this method to perform NetScans.
Setting ICMP Discovery
- Navigate to Settings > NetScans > Add Advanced NetScan.
- In the ICMP Discovery Rules section, enter the following details:
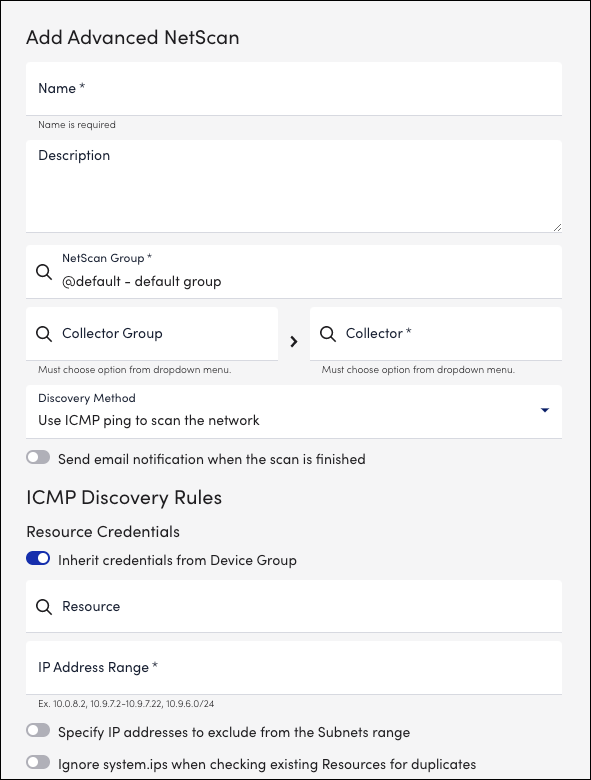
- Resource Credentials – To name the discovered resources using ##SYSTEMNAME## or to add only specified resources such as Cisco, NetApp, and so on, you must enter credentials that are used during NetScan to detect resource types.
Note: These properties or credentials are not set on the resources after the NetScan is set. Therefore, you must specify a destination group that has the required credentials.
The following are the two options for specifying credentials used for detecting resources during the NetScan.- Inherit credentials from Device Group — Select an existing resource group whose properties or credentials will be used for NetScan.
- Use custom credentials for this scan — Enter the Property Name or Property value for the required resources for NetScan.
- Inherit credentials from Device Group — Select an existing resource group whose properties or credentials will be used for NetScan.
- Adding SNMP Credentials
- If there are large networks with different SNMP v3 credentials per device, and if the credentials and devices are not mapped, it is a time consuming task to match multiple devices with their credentials. In such scenarios, you can select Add SNMP Credentials to let collector scan the device and identify the correct SNMP v3 credentials configured for it. You can add maximum 30 credentials per NetScan. To use this feature the collector version must be EA 33.400 and later.
- To add SNMP v3 credential set, select the Add SNMP Credentials or the Plus (+) button and add SNMP v3 credential details.
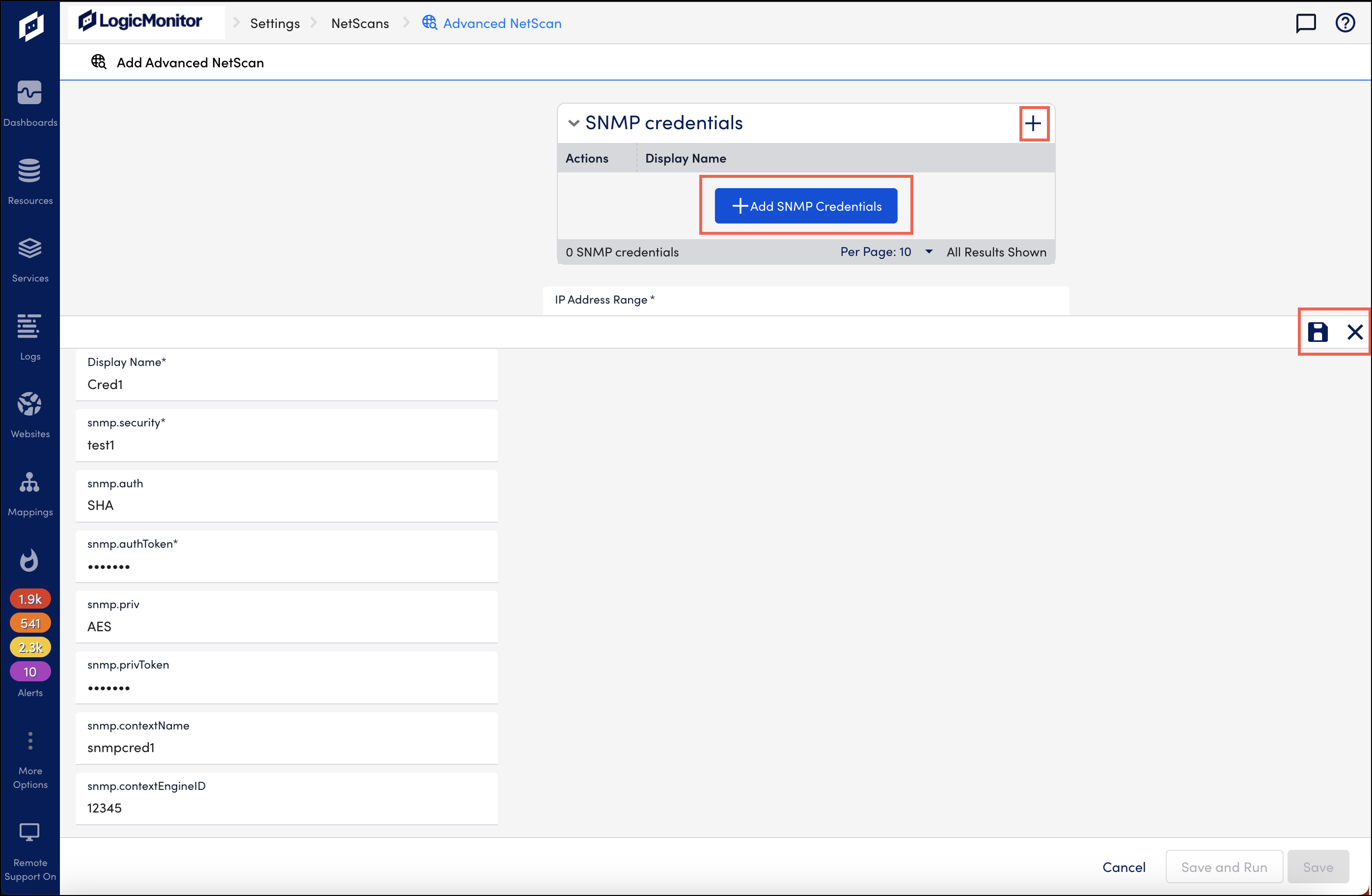
- You have to enter valid details in the Display Name, snmp.security, and snmp.authToken mandatory fields. If the optional fields are kept empty, collector will populate them with the default values, such as SHA for snmp.auth and AES for snmp.priv. After you enter credential details, select
 to save them. Select X to close the expanded area. Note that if you select X without saving the details, the credentials will not be auto saved, and you will loose the details.
to save them. Select X to close the expanded area. Note that if you select X without saving the details, the credentials will not be auto saved, and you will loose the details. - When LogicMonitor performs netscan, the credentials are checked against every device found under the specified IP range. For example, you have added 30 credentials and specified an IP range for 10 devices. For every device, collector will check the 30 credentials. Note that at the device level, collector will exit the credential match operation when it finds the first match.
- Warning: This process involves brute force to find matching credentials. For example, you have added 30 credentials. In cases where collector does not find a match during initial attempts, then in such cases collector will hit every device 30 times to check if the credentials match. This might impact your ongoing processes or your account might get blocked after crossing a set limit of attempts. We recommend that before using this feature, you check your infrastructure and firewall settings to allow collector to make multiple attempts.
- Once found, correct credentials are reported and updated on respective device’s host properties. Collector will later use the credentials to perform SNMP based data collection on the devices.
- Note: There is a possibility that all 10 devices can have 10 different credentials or 5 devices can have one credential which is common and rest of them can have different credentials. If the credentials do not match, it is noted in the logs. In cases where a device exists but there is no information about it, or we are unable to monitor it, the device is placed under minimal monitoring.
- IP address range – Enter the IP address range. The accepted syntax is as follows:
- A hyphenated range like this: 10.9.8.2-10.9.8.240
- CIDR notation like this: 192.168.1.0/24 (i.e. 192.168.1.1 through 192.168.1.254)
- A comma-separated list like this: 10.9.8.4, 10.9.8.8
- Mixture separated by commas like this: 10.9.8.2, 10.9.7.2-10.9.7.22, 10.9.6.0/24
- Specify IP addresses to exclude from the Subnets range – Select the Specify IP addresses to exclude from the Subnets range option if you would like to exclude any IP addresses. You can exclude a single range of IP addresses and/or several IP addresses separated by commas.
- Ignore system.ips when checking existing devices for duplicates – Allows for the discovery of resources that share an IP with a device already in monitoring, as determined by the system.ips property. If not slected, a resource that shares the same IP as one captured for an existing device’s system.ips property is considered to be a duplicate and not discovered.
- Exclude duplicate IP addresses — Specify a range, comma-separated list of IP addresses, or both to exclude.
- Included/Excluded Devices – By default, LogicMonitor includes all discovered resources and automatically assigns them to the Unmonitored Resource group. For more information, see Unmonitored Resources.
- In the ICMP Discovery Rules section, enter the following details:
Note: You can manually decide which resources to add for monitoring. You can do this by override the settings to change the resources that are included, and for which groups these resources are assigned. In addition, you can specify which resources you want to exclude from monitoring.
You can include or exclude resources based on the resource type (Cisco, Linux, Windows, NetApp) or use a custom query. The properties supported for custom queries are a subset of those typically available with AppliesTo scripting, including:
- system.devicetype
- system.hostname
- system.ips
- properties set by the LogicMonitor auto-properties feature: system.sysoid, system.sysinfo, etc.
You must specify which resource group the discovered resources should be assigned while setting each inclusion criteria.
Note: The dynamic resource groups are not available for selection as discovered resources are not manually added to the dynamic resources groups. However, the newly discovered resources are automatically placed into any previously-created dynamic device groups with matching criteria, including the group you selected. For more information on dynamic resource groups, see Device Groups Overview.
In addition to setting a device group for each set of device inclusion criteria, you can also disable alerts for the required set by unchecking the Enable Alerting option.
Note: Rules for excluded devices are prioritized over rules for included devices.
- Insert Token and Rename Discovered Devices- You can optionally choose to name discovered devices using a naming convention other than (or in addition to) LogicMonitor’s default DNS naming for the ICMP discovery method. You can use a combination of text and tokens. The following tokens are supported:
- ##IPADDRESS##. The IP address of the device.
- ##SYSTEMNAME##. The system name is provided by the sysName OID if the device responds to SNMP. You require either the Inherit credentials from Device Group or the Use custom credentials for this scan option set to retrieve the SYSTEMNAME during the NetScan.
- ##REVERSEDNS##. By default, the DNS name is provided by your reverse DNS resolution.
For example, you can add the text and tokens in combination as a prefix to the resources IP address: Cisco_switch_##IPADDRESS##.
Note: When a NetScan adds unique devices with duplicate names, those resources are added with display names set to IP_CollectorID.
- Schedule — To run the NetScan on a schedule instead of running it on demand, enable the Run this NetScan on a schedule option, and select the required options such as the Frequency, Starts Hourly, and the time zone for running the NetScans.
- Ports — You can modify the global default list of ports by selecting the Custom Ports for this NetScan option for the ICMP discovery method. If you know which TCP ports are open, you can determine the resource type.
For example, Windows usually has ports 135 and 3389 open, while Linux does not.
- Enhanced NetScan Scripts – Use the LogicMonitor Enhanced Script Netscan option for improved output formatting, additional group assignment options, and resource filtering. You can choose to inherit device credentials from a specific resource, or resource group, or set custom credentials in the NetScan configuration. For more information, see Enhanced Script Netscan.


