Troubleshooting SAML 2.0 Login Issues
Last updated - 25 July, 2025
As a result of the migration of SAML1 to SAML2, users authenticated using SAML-based Single Sign-On (SSO) may be logged out and not able to login again. You can experience various login scenarios depending on your IdP configuration and authentication.
404 Not Found Error on Login Page
If you are getting a “404 Not Found” error on your login page, contact Customer Support.
Did Not Decrypt Error Due to Unsigned Response
The error occurs when the Identity Provider (IdP) is configured to sign only the SAML assertion instead of the entire response, which may not meet service provider requirements.
Requirements for Mitigating Did Not Decrypt Error Due to Unsigned Response
Admin user permissions for Active Directory Federation Services (ADFS)
Mitigating Did Not Decrypt Error Due to Unsigned Response
- Log in as admin user in your Active Directory Federation Services (ADFS).
- Select Relaying Party Trusts.
- Right-click on the required row from the Relaying Party Trusts table and copy the display name.
- Launch PowerShell as administrator and run the following command, where “<Display Name>” is the name you copied from ADFS:
Set-ADFSRelyingPartyTrust -TargetName "<Display Name>" -SamlResponseSignature BothIf an error occurs with the above command, run the following command:
Set-ADFSRelyingPartyTrust -TargetName "<Display Name>" -SamlResponseSignature MessageAndAssertion- Verify the setting using the following command:
Get-ADFSRelyingPartyTrust -Name "<Display Name>" | Select-Object SamlResponseSignatureThe console displays the SAML response signature depending on which configuration successfully worked with your setup.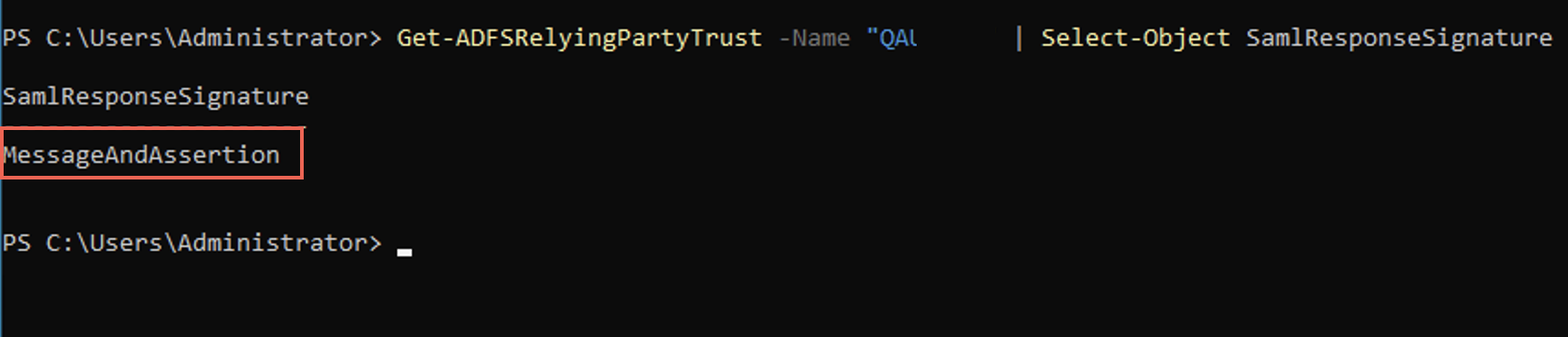
You can navigate back to your LogicMonitor portal and log in.
Blank Page or URL Redirection Loop Encountered During Access
The errors occurs if the Identity Provider (IdP) does not meet updated validation criteria and the RestrictSSO feature is enabled on the account.
Requirements for Mitigating Blank Page or URL Redirection Loop Encountered During Access
To mitigate blank page or URL redirection loop, you need the following:
- Admin user permissions for Active Directory Federation Services (ADFS)
- Restrict Single Sign On switch is enabled on the Security page. For more information, see Enforcing SSO.
Mitigating Blank Page or URL Redirection Loop Encountered During Access
- Log in as admin user in your Active Directory Federation Services (ADFS).
- Select Relaying Party Trusts.
- Right-click on the required row from the Relaying Party Trusts table and copy the display name.
- Launch PowerShell as administrator and run the following command, where “<Display Name>” is the name you copied from ADFS:
Set-ADFSRelyingPartyTrust -TargetName "<Display Name>" -SamlResponseSignature BothIf an error occurs with the above command, run the following command:
Set-ADFSRelyingPartyTrust -TargetName "<Display Name>" -SamlResponseSignature MessageAndAssertion- Verify the setting using the following command:
Get-ADFSRelyingPartyTrust -Name "<Display Name>" | Select-Object SamlResponseSignatureThe console displays the SAML response signature depending on which configuration successfully worked with your setup.
You can navigate back to your LogicMonitor portal and log in.
SAML Destination Invalid Error When Using Shibboleth or SSOCircle
This error occurs with IdPs like Shibboleth or SSOCircle, which may send incomplete or mismatched redirect URLs, leading to destination or redirect errors.
Requirements for SAML Destination Invalid Error When Using Shibboleth or SSOCircle
Admin user permissions for Shibboleth or SSOCircle IDP
Mitigating SAML Destination Invalid Error When Using Shibboleth or SSOCircle
- Log in as admin user in Shibboleth.
- Download the current IDP metadata file.
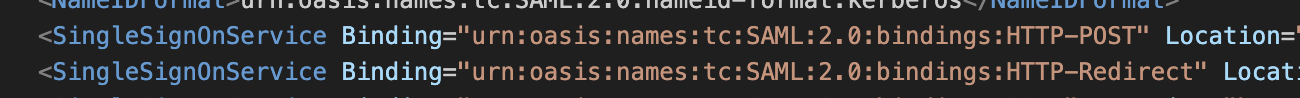
- Open the metadata XML file and perform one of the following to the SingleSignOnService tag that uses the redirect binding:
- Remove the redirect binding
- Move the redirect binding under the POST binding tag to ensure that POST is set as the default binding.
- In LogicMonitor, upload the updated IDP metadata to your Service Provider configuration. For more information, see Enabling Single Sign-on.
You can navigate back to your LogicMonitor portal and log in.


