Security Settings
Last updated - 02 February, 2026
You can customize the security settings of your LogicMonitor account to control user access to the portal. For example, you can suspend users after a specified number of inactivity days and configure an email domain allowlist. In addition, LogicMonitor provides the latest security recommendations to help secure your portal. For more information on securing your LogicMonitor platform, see LogicMonitor Best Practices.
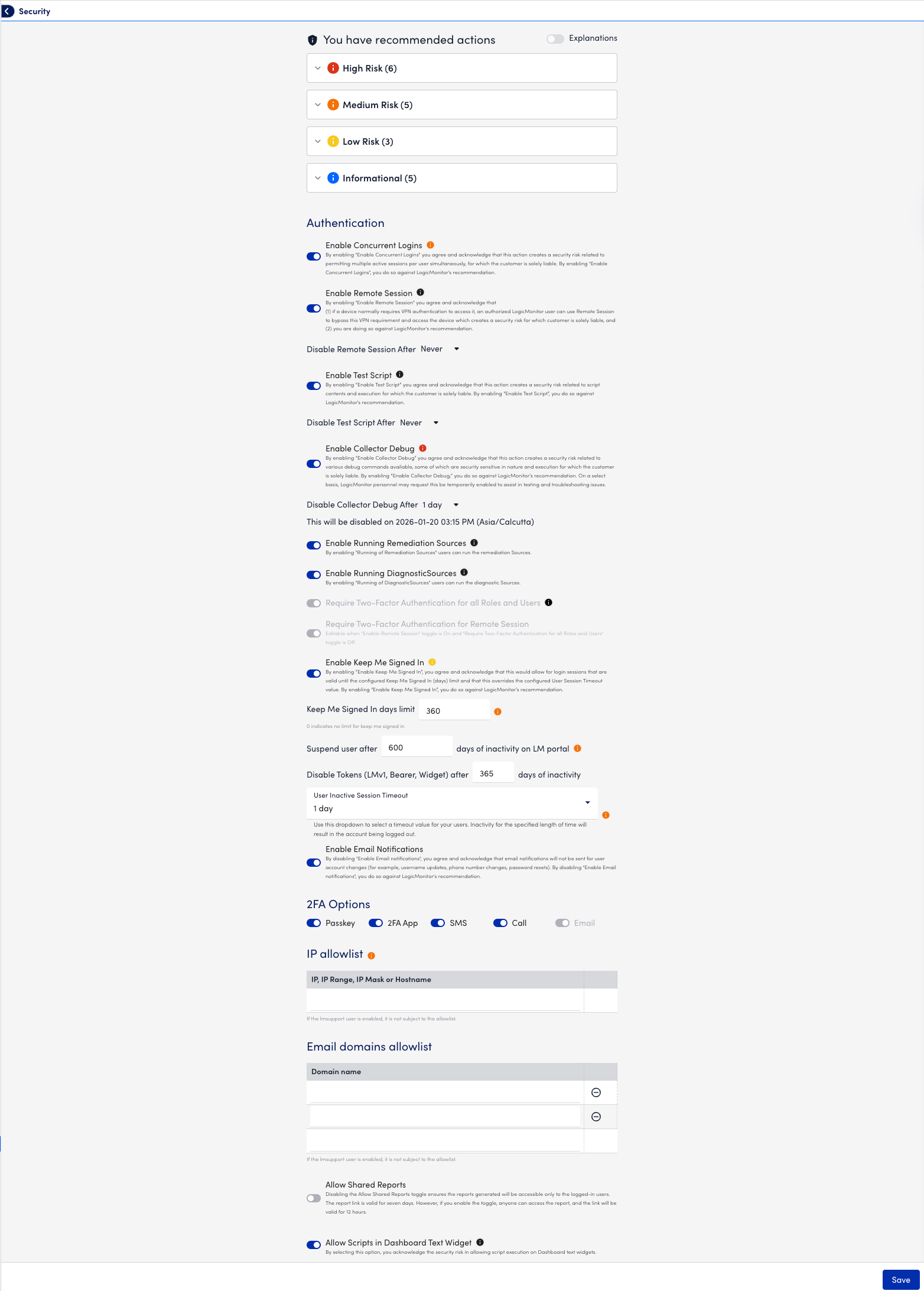
LogicMonitor Security Recommended Actions
LogicMonitor displays all the recommended actions on the Security page if your portal configuration does not match the latest LogicMonitor-released recommendations.
Recommendation: Review this information and update your configuration accordingly.
The recommended actions are categorized into the following:
- High Risk—Requires immediate attention to address potential vulnerabilities
- Medium Risk—Important to resolve but not immediately critical
- Low Risk—Minor issues that should be corrected for best practices
- Informational—Advisory items for awareness or optional configuration improvements
You can view additional information for each recommended action if you toggle the Explanation switch.
Warning: If you close the recommended action and save without incorporating it, then the same recommended action displays on the next session.
Two-Factor Authentication
Two-factor authentication (2FA) provides an extra layer of security for accessing your LogicMonitor account. In addition, to a username and password, 2FA requires users to use a third-party application or an authentication token delivered using SMS, voice, or email to verify their identity.
You can globally apply 2FA for all users who log in to the portal for your LogicMonitor account. 2FA can also be applied on a per-user basis, however globally enabling 2FA forces all users to authenticate using 2FA regardless of the per-user setting.
Note: If you enable Single Sign On (SSO) for your LogicMonitor account, and SSO is not set to Restrict Single Sign On, users can choose to log in to their portals using SSO or 2FA.
For more information about accessing your LogicMonitor account when 2FA is enabled, see Two-Factor Authentication Account Access.
Keep Me Signed In
An admin user can control the appearance and usage of Keep Me Signed In option on the Company Settings page. Also, the admin can control the duration of timeout from 0 to 400 days for users who chose to be kept signed in. 0 represents no limit; user session will last indefinitely.
Note: The Keep Me Signed In session timeout durations would be 0 and 30 days for existing and new LogicMointor customers respectively.
When an admin enables this, users can choose to use it while logging in. User sessions who had not checked the button while logging in will timeout after a certain time of inactivity. When the admin disables this, users whose session is still active as they had checked Keep me Signed In would be forcefully logged out. User sessions who had not checked the button while logging in, will be exempt as their session will timeout eventually.
Admin Account Recovery for Inactivity Suspension
All users except API-only, and LM Support users can self-activate their accounts when suspended by the Suspend user after X days of inactivity on LM portal option on the Security page.
When a user, excluding SAML-based Single Sign-On users , attempts to log in after their account has been suspended due to inactivity, a secure recovery link is sent to their registered email address. Your account is automatically reactivated—no manual intervention required.
Important: If you have not enabled Suspend user after X days of inactivity on LM portal option on the Security page, this functionality does not work.
Disable Unused Tokens
As a mitigation against risks related to the disclosure of previously generated and unused LMv1, Bearer, and Widget tokens, LogicMonitor has introduced a feature to auto-disable unused tokens after a set days of inactivity. Admin user with Manage Security permission can set the number of inactive days after which the unused token is auto-disabled.
When the unused token is disabled, LogicMonitor sends an email alert to the owner of the token about the disabled token and the reason for disabling it. A log of disabled token is maintained on the Audit Logs page.
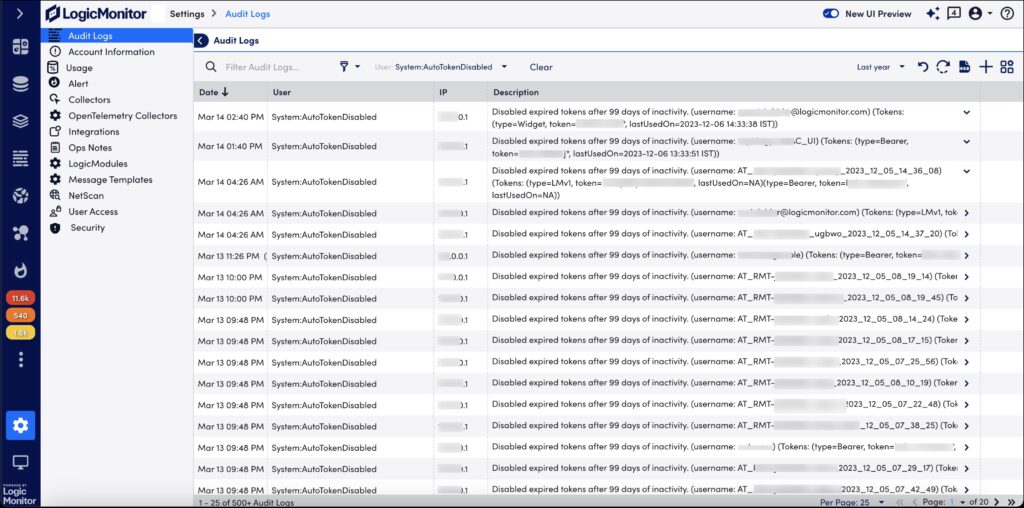
Similarly, details of the disabled tokens are also available in the table for LMv1 API token, bearer, and widgets token. To access the details, navigate to Settings > User Access > Users and Roles and access the LMv1 API Tokens, Bearer Tokens, and Widgets Tokens tab. The details of the disabled token are greyed and cannot be edited.
To activate the disabled token, contact your administrator. For more information, see LMv1 API tokens, Bearer tokens, and Widgets tokens.
Requirements to Configure the Security Settings
To configure the Security settings, you need a LogicMonitor user with the “Manage” role for Security. For more information, see Users and Roles.
Note: Any changes to security settings trigger an email notification to the primary contact and all listed additional contacts.
Configuring the Security Settings
- In LogicMonitor, navigate to Settings > Security.
- Toggle the Explanations switch to view additional information about each recommendation.
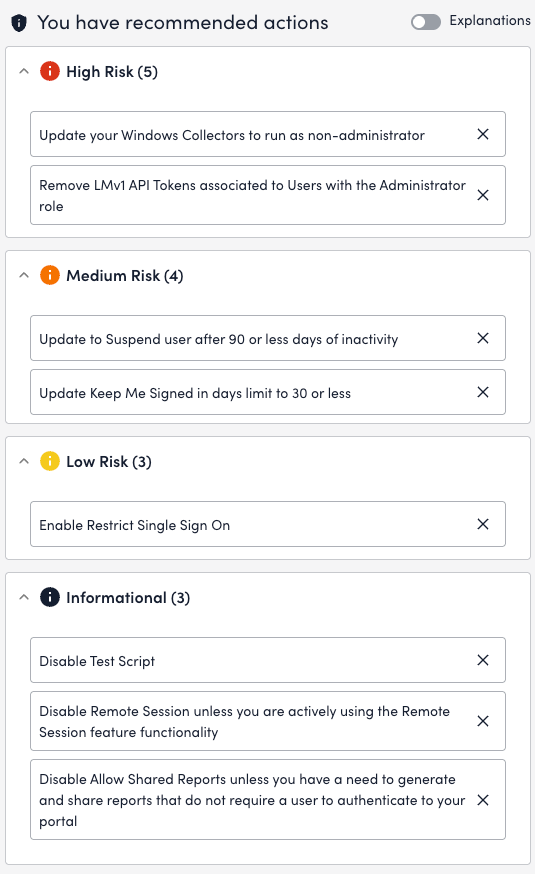
- Toggle the Enable Concurrent Logins switch to enable permitting multiple active sessions per user simultaneously.
This switch is disabled by default. - Toggle the Enable Remote Session switch to enable a remote session on an account-wide basis.
For more information, see Remote Session.
This switch is disabled by default.
When you enable this switch, the Disable Remote Session After dropdown displays, enabling you to select the disable-after duration. The default value is 1 day. - Toggle the Enable Test Script switch to disable the Test Script option testing the script-based LogicModules.
This switch is disabled by default.
When you enable this switch, the Disable Test Script After dropdown displays, enabling you to select the disable-after duration. The default value is 1 day. - Toggle the Enable Collector Debug switch to disable collector debug on an account-wide basis.
This switch is disabled by default.
When you enable this switch, the Disable Collector Debug After dropdown displays, enabling you to select the disable-after duration. The default value is 1 day.
Note: The date and time displayed for remote session, test script, and collector debug are based on the timezone you have specified in the portal settings. - Toggle the Allow Execution of Diagnostic Sources switch to run diagnostic sources on an account-wide basis.
This switch is disabled by default. - Toggle the Require Two-Factor Authentication for all Roles and Users switch to enable two-factor authentication on an account-wide basis.
For more information, see Two-Factor Authentication.
A message displays prompting you to select when to enforce authentication. You can enforce authentication immediately or eventually. This switch is enabled by default.
Note: LogicMonitor sends email notification to all local users and primary and additional contacts defined in Portal Settings if the Require Two-Factor Authentication for all Roles and Users option is modified.
- Toggle the Require Two-Factor Authentication for Remote Session switch to enable two-factor authentication on your remote session.
You are required to toggle off the Require Two-Factor Authentication for all Roles and Users switch to use this option. - Toggle the Keep Me Signed In switch and in the Keep Me Signed In days field, enter the number of days you want to remain signed in.
- To suspend an account of a user after a defined number of days, enter a value in the Suspend user after days of inactivity on LM portal setting.
Accepted values are whole numbers. The default days set is 90 days.
Note: For users nearing suspension due to inactivity on the LM Portal, a warning notification email is sent seven days prior to suspension. - In the Disable Token (LMv1, Bearer, Widget) after X days of inactivity, enter the number of days after which you want to disable the inactive tokens.
The default days set is 365 days. - Select a timeout value for users from the User Inactive Session Timeout dropdown menu to log users out of the LogicMonitor portal after a specified time.
Inactivity for the specified length of time results in a user account being logged out. The timeout period is applied to users not enabling the option to stay signed in when they log in to their LogicMonitor portal.
The default timeout period is 4 hours.
Note: If your LogicMonitor account has Single Sign On enabled, session timeouts are also governed by your SSO identity provider. If you have an account that must remain logged in longer than the timeout value, there are two options available:
- Enable the option to stay signed when logging in to the LogicMonitor portal.
- Restrict Single Sign On to force a user session to re-authenticate and renew with the SSO provider. If the SSO session timeout is configured for a longer timeout session than the LogicMonitor portal, the user session re-authenticates and renews with the SSO provider when the LogicMonitor portal session times out.
LogicMonitor cannot guarantee the session timeout behavior with every environment that leverages Single Sign On. For more information, see Single Sign On.
- Toggle the Enable Email Notification switch to send email alerts for user account changes, such as username updates, phone number changes, and password resets.
- To configure two-factor authentication (2FA) methods that are displayed on the LogicMonitor user login page and setup, you can enable or disable the Passkey, Authenticator app, SMS, Voice call, and Email switch. By default, all 2FA options are enabled and you cannot disable the Email switch.
- In the IP allowlist table, enter a public Internet-facing IP address.
You can identify addresses using any of the following formats:- Hostname (mycomputer.mybusiness.com)
- IP address (192.168.1.1)
- Network/mask (192.168.1.0/24)
- Network range (192.168.1.100-255)
LogicMonitor displays a warning if your current IP address is locked out after saving the list. If you are locked out of your account, contact Customer Success.
- In the Email domain allowlist, enter the name of the required email domains for the primary email ID. You can enter multiple domain names by adding commas, for example, google.com, tomotom.com, and so on. By default, the field is blank.
Note: The maximum limit for adding the domains is 100. The character limit is 253 up to a storage limit of 65,535 characters.
In addition, this feature applies only to new users and not existing users who have registered before the domain allowlist feature and for SAML users.
- Toggle the Allow Shared Reports switch to give access to reports to the users who are not logged in.
Note: Disabling the Allow Shared Reports toggle ensures the reports generated is accessible only to the logged-in users. The report link is valid for seven days. If you enable the toggle, anyone can access the report, and the link is valid for 12 hours.
- Toggle the Allow Scripts in Dashboard Text Widget switch to allow scripts in the Dashboard Text Widget.
Warning: By selecting this option, you acknowledge the security risk in allowing script execution on Dashboard text widgets.
- Select Save.
The Security settings are applied globally for all users that log in to the portal.


