Monitoring Azure Backup and Recovery Protected Items
Last updated - 30 January, 2023
LogicMonitor gathers data for Backup Protected Items and Recovery Protected Items from Log Analytics workspaces in your Azure account. To support monitoring of the Backup Protected Items and Recovery Protected Items services, your Azure account must be configured to forward diagnostic events from the Azure Recovery Service vault to a Log Analytics workspace.
Determining the Log Analytics Workspace
In Azure, the Log Analytics workspace is what retains the forwarded diagnostic event data and makes it available for LogicMonitor to query. Before continuing with the rest of the configuration process, you must determine which Log Analytics workspace that the Backup and Site Recovery events will be forwarded to.
Recommendation: Create a new separate Log Analytics workspace to retain all Backup and Site Recovery events. Reusing an existing table may result in hitting the 500 column limit for AzureDiagnostics tables. For more information, see AzureDiagnostics from Azure.
The Log Analytics workspace architecture is customer-dependent. If you have an existing Log Analytics workspace implementation, you can leverage an existing workspace architecture to retain forwarded backup and recovery information. If you do not have an existing Log Analytics workspace, you can create a single Log Analytics workspace and retain all Backup events and Site Recovery events. For more information, see Design a Log Analytics workspace architecture.
Note: LogicMonitor does not require a specific Log Analytics workspace architecture. The only requirement is that Recovery Services vaults forward the events to at least one Log Analytics workspace within the Azure account.
Forwarding Backup Events to Log Analytics
Forwarding Backup events in your Azure account is required to successfully monitor Backup Protected Items within LogicMonitor. LogicMonitor recommends using a policy-based configuration. Using a policy ensures that Azure Diagnostic settings are applied consistently across all Recovery Services vaults, without having to configure event forwarding for each vault. Microsoft offers a built-in Azure policy for forwarding Backup events to Log Analytics. For more information, see Configure Vault Diagnostics settings at scale.
Note: For manual configuration steps, see Use diagnostics settings with Log Analytics.
Forwarding Site Recovery Events to Log Analytics
Forwarding Site Recovery events in your Azure account is required to successfully monitor Recovery Protected Items within LogicMonitor. LogicMonitor recommends using a policy-based configuration. Using a policy ensures that Azure Diagnostic settings are applied consistently across all Recovery Service vaults, without having to configure event forwarding for each vault. However, Microsoft does not offer a built-in policy for forwarding Site Recovery events to Log Analytics at this time.
Adding a Site Recovery Policy
- In Azure, navigate to Policy > Definitions and select + Policy definition.
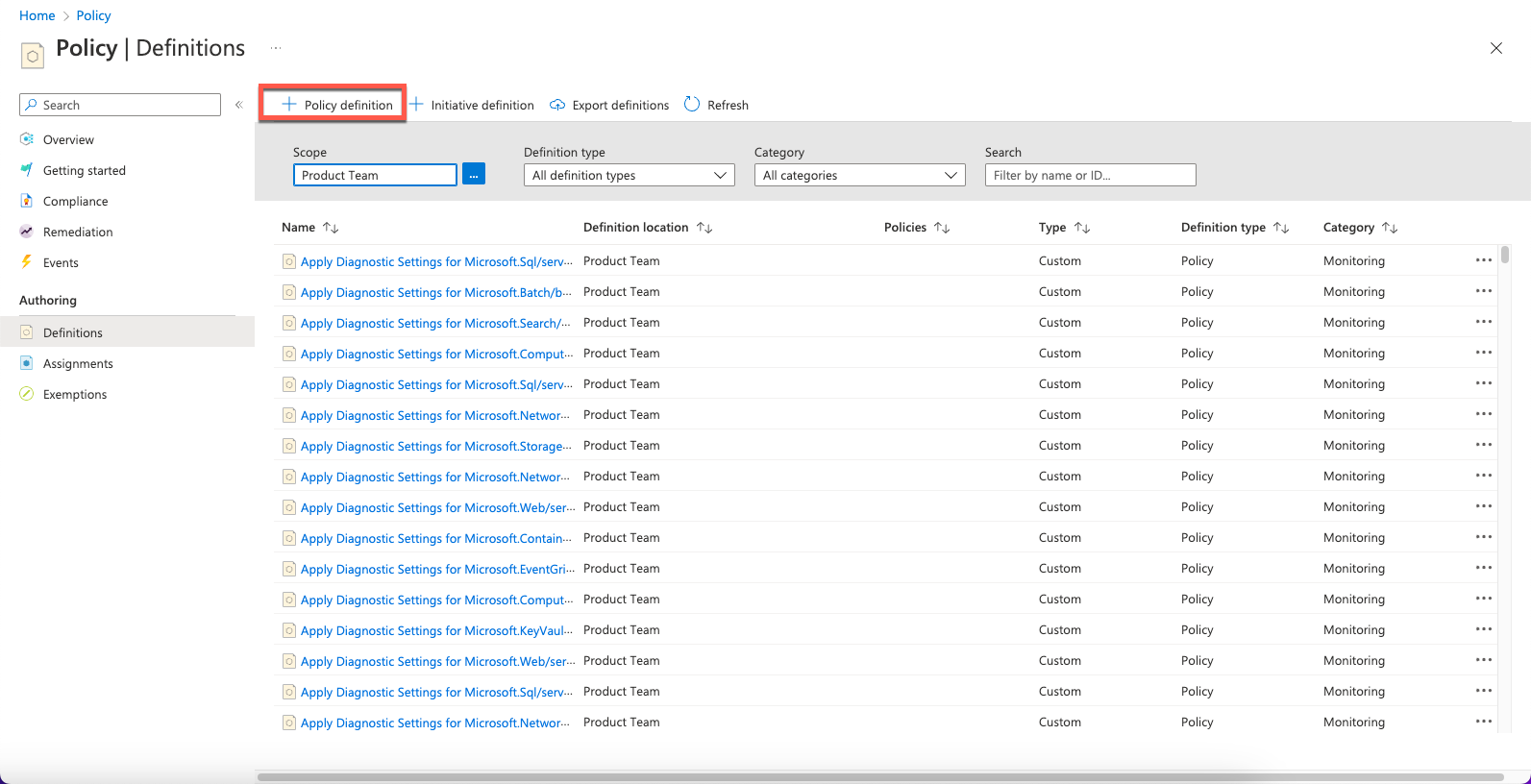
- On the Policy definition page, navigate to Basics > Definition location > Launch scope selector.
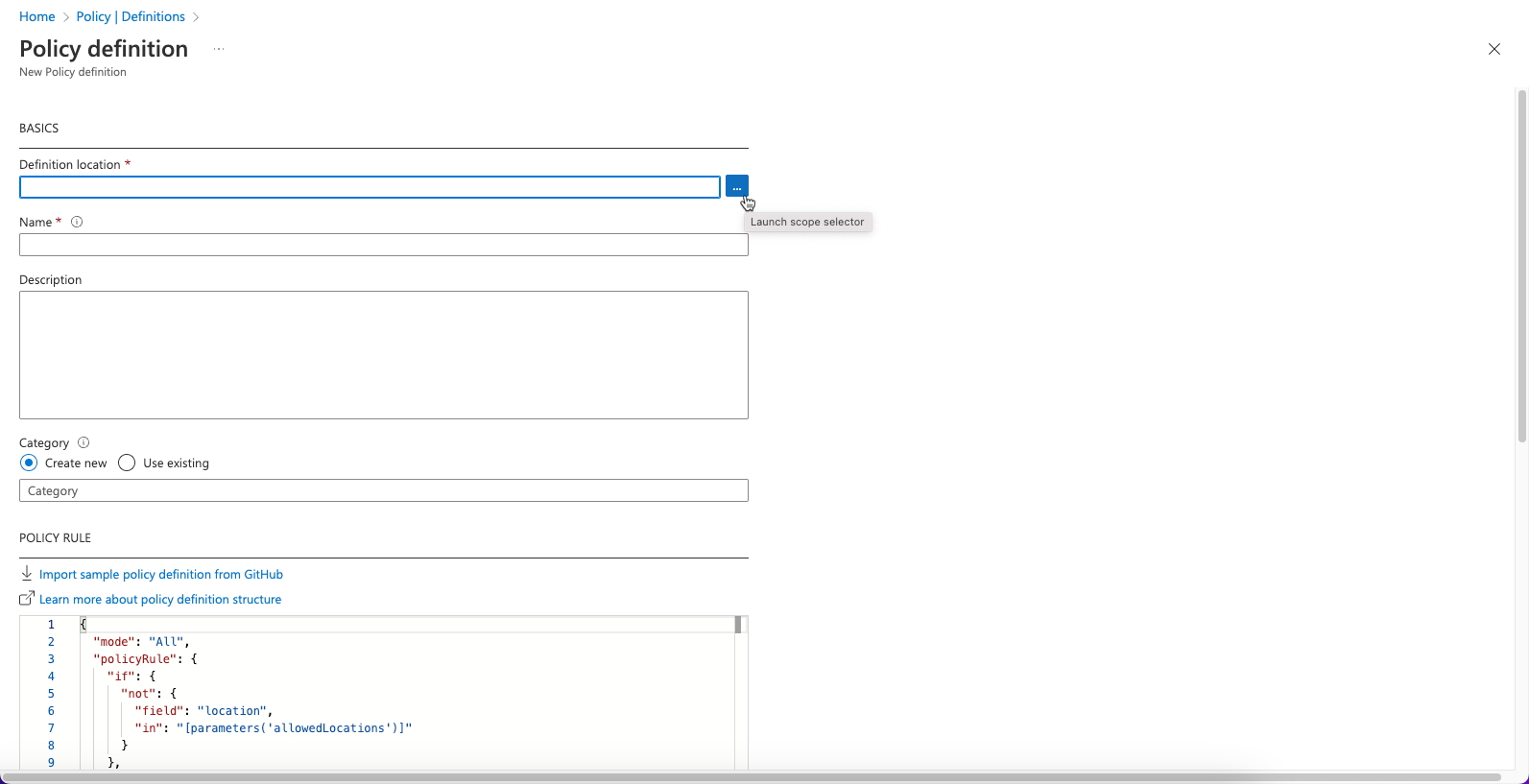
- In the Definition location panel, choose a Subscription and then click Select.
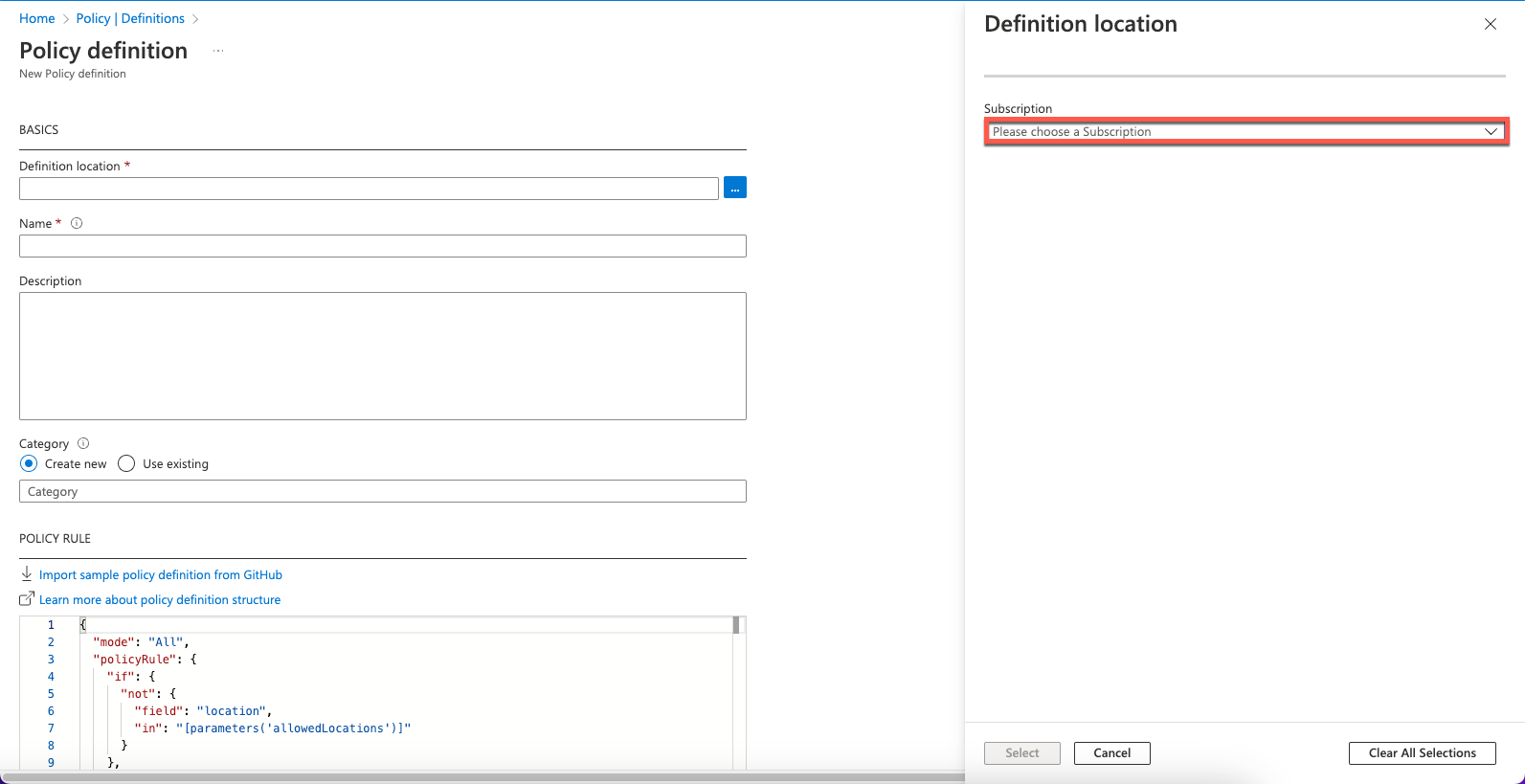
- Enter the following in the Basics section of the Policy definition page:
- Name— Deploy Diagnostic Settings for Recovery Services Vault to Log Analytics workspace for AzureSiteRecovery categories
- Category— Use Existing > Backup
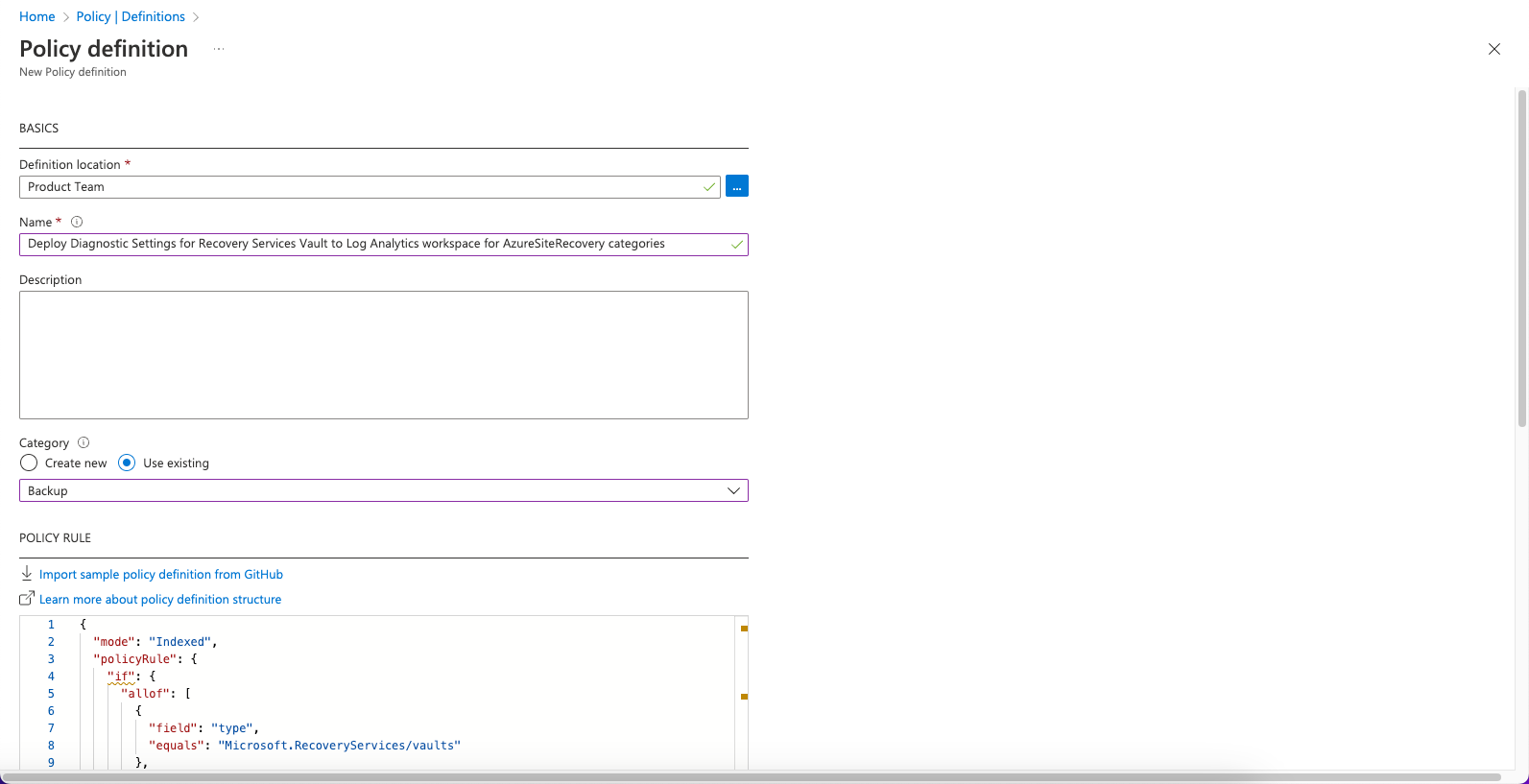
- In the Policy Rule section, copy and paste the contents of AzureSiteRecoveryPolicy.json:
{
"mode": "Indexed",
"policyRule": {
"if": {
"allof": [
{
"field": "type",
"equals": "Microsoft.RecoveryServices/vaults"
},
{
"not": {
"field": "[concat('tags[',parameters('tagName'), ']')]",
"equals": "[parameters('tagValue')]"
}
}
]
},
"then": {
"effect": "deployIfNotExists",
"details": {
"type": "Microsoft.Insights/diagnosticSettings",
"existenceCondition": {
"allof": [
{
"count": {
"field": "Microsoft.Insights/diagnosticSettings/logs[*]",
"where": {
"allof": [
{
"field": "Microsoft.Insights/diagnosticSettings/logs[*].Category",
"in": [
"AzureSiteRecoveryJobs",
"AzureSiteRecoveryEvents",
"AzureSiteRecoveryReplicatedItems",
"AzureSiteRecoveryReplicationStats",
"AzureSiteRecoveryRecoveryPoints",
"AzureSiteRecoveryReplicationDataUploadRate",
"AzureSiteRecoveryProtectedDiskDataChurn"
]
},
{
"field": "Microsoft.Insights/diagnosticSettings/logs[*].Enabled",
"equals": "True"
}
]
}
},
"Equals": 7
},
{
"field": "Microsoft.Insights/diagnosticSettings/workspaceId",
"notEquals": ""
},
{
"field": "Microsoft.Insights/diagnosticSettings/logAnalyticsDestinationType",
"equals": "AzureDiagnostics"
}
]
},
"roleDefinitionIds": [
"/providers/microsoft.authorization/roleDefinitions/749f88d5-cbae-40b8-bcfc-e573ddc772fa",
"/providers/microsoft.authorization/roleDefinitions/92aaf0da-9dab-42b6-94a3-d43ce8d16293"
],
"deployment": {
"properties": {
"mode": "incremental",
"template": {
"$schema": "http://schema.management.azure.com/schemas/2015-01-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"vaultName": {
"type": "string"
},
"logAnalytics": {
"type": "string"
},
"profileName": {
"type": "string"
}
},
"variables": {},
"resources": [
{
"type": "Microsoft.RecoveryServices/vaults/providers/diagnosticSettings",
"apiVersion": "2017-05-01-preview",
"name": "[concat(parameters('vaultName'), '/', 'Microsoft.Insights/', parameters('profileName'))]",
"dependsOn": [],
"properties": {
"workspaceId": "[parameters('logAnalytics')]",
"logAnalyticsDestinationType": "AzureDiagnostics",
"metrics": [],
"logs": [
{
"category": "AzureSiteRecoveryJobs",
"enabled": "true"
},
{
"category": "AzureSiteRecoveryEvents",
"enabled": "true"
},
{
"category": "AzureSiteRecoveryReplicatedItems",
"enabled": "true"
},
{
"category": "AzureSiteRecoveryReplicationStats",
"enabled": "true"
},
{
"category": "AzureSiteRecoveryRecoveryPoints",
"enabled": "true"
},
{
"category": "AzureSiteRecoveryReplicationDataUploadRate",
"enabled": "true"
},
{
"category": "AzureSiteRecoveryProtectedDiskDataChurn",
"enabled": "true"
}
]
}
}
],
"outputs": {
"policy": {
"type": "string",
"value": "[concat(parameters('logAnalytics'), 'configured for AzureDiagnostics logs for ', ': ', parameters('vaultName'), '/', 'Microsoft.Insights/', parameters('profileName'))]"
}
}
},
"parameters": {
"logAnalytics": {
"value": "[parameters('logAnalytics')]"
},
"vaultName": {
"value": "[field('name')]"
},
"profileName": {
"value": "[parameters('profileName')]"
}
}
}
}
}
}
},
"parameters": {
"profileName": {
"type": "String",
"metadata": {
"displayName": "Profile name",
"description": "The diagnostic settings profile name"
},
"defaultValue": "setbypolicy_logAnalyticsAzureSiteRecovery"
},
"logAnalytics": {
"type": "String",
"metadata": {
"displayName": "Log Analytics workspace",
"description": "Select Log Analytics workspace from dropdown list. If this workspace is outside of the scope of the assignment you must manually grant 'Log Analytics Contributor' permissions (or similar) to the policy assignment's principal ID.",
"strongType": "omsWorkspace",
"assignPermissions": true
}
},
"tagName": {
"type": "String",
"metadata": {
"displayName": "Exclusion Tag Name",
"description": "Name of the tag to use for excluding vaults from this policy. This should be used along with the Exclusion Tag Value parameter."
},
"defaultValue": ""
},
"tagValue": {
"type": "String",
"metadata": {
"displayName": "Exclusion Tag Value",
"description": "Value of the tag to use for excluding vaults from this policy. This should be used along with the Exclusion Tag Name parameter."
},
"defaultValue": ""
}
}
}- Select Save.
Assigning the Site Recovery Policy
- In Azure, navigate to Backup center > Policy and compliance > Azure policies for backup and select:
Deploy Diagnostic Settings for Recovery Services Vault to Log Analytics workspace for AzureSite Recovery categories.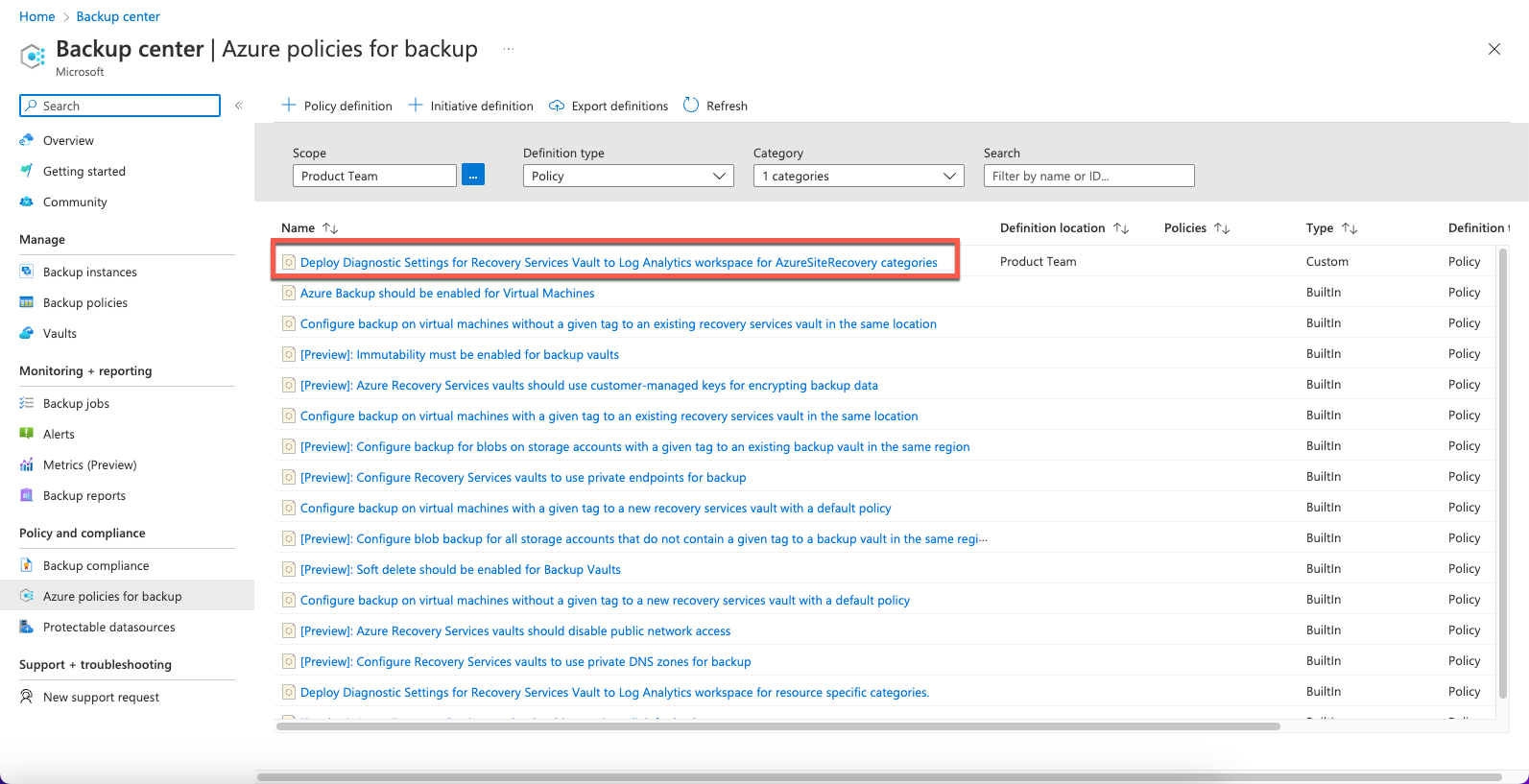
- On the Azure policies for backup page, select Assign.
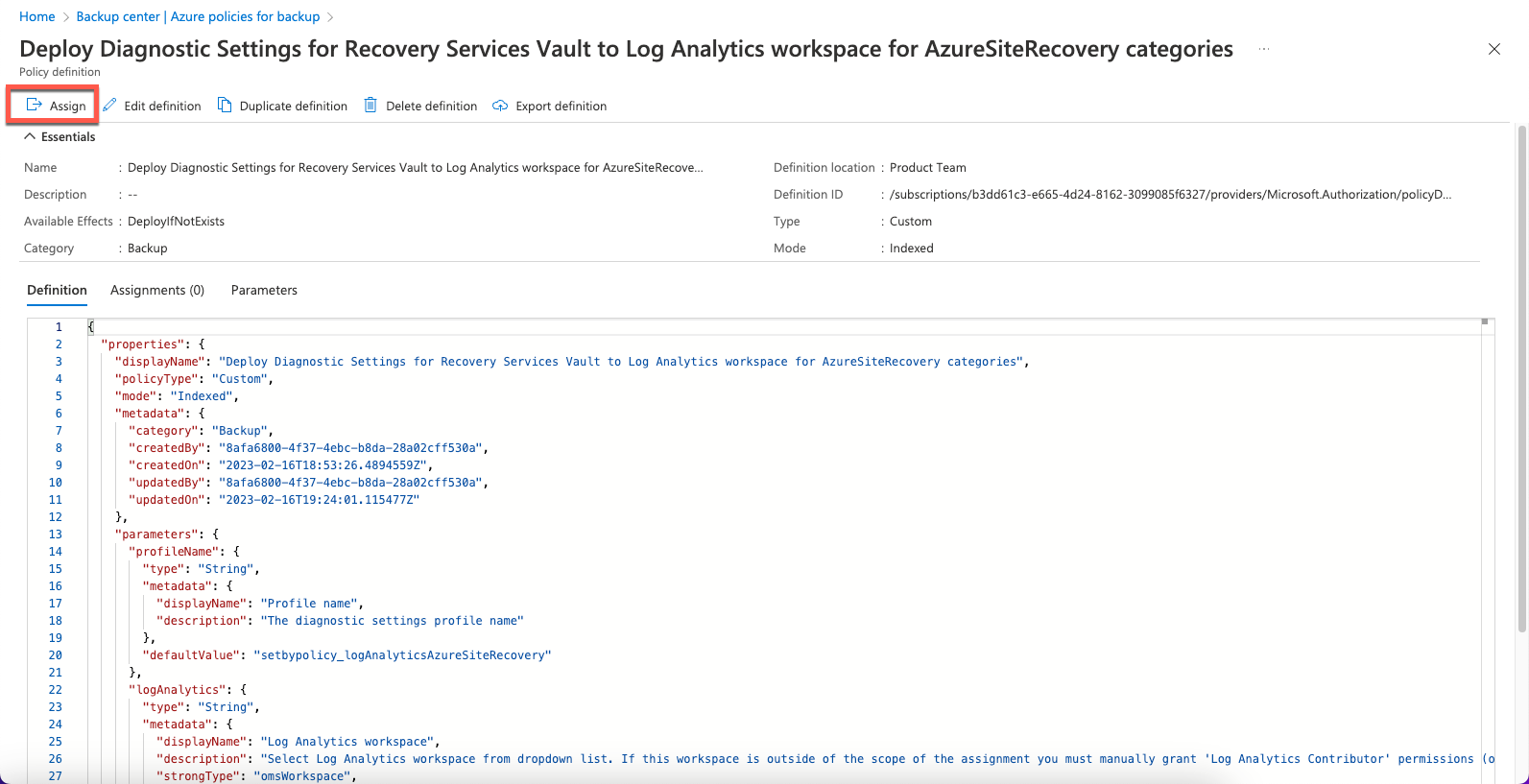
- On the Assign policy page, select Basics > Scope > Launch scope selector.
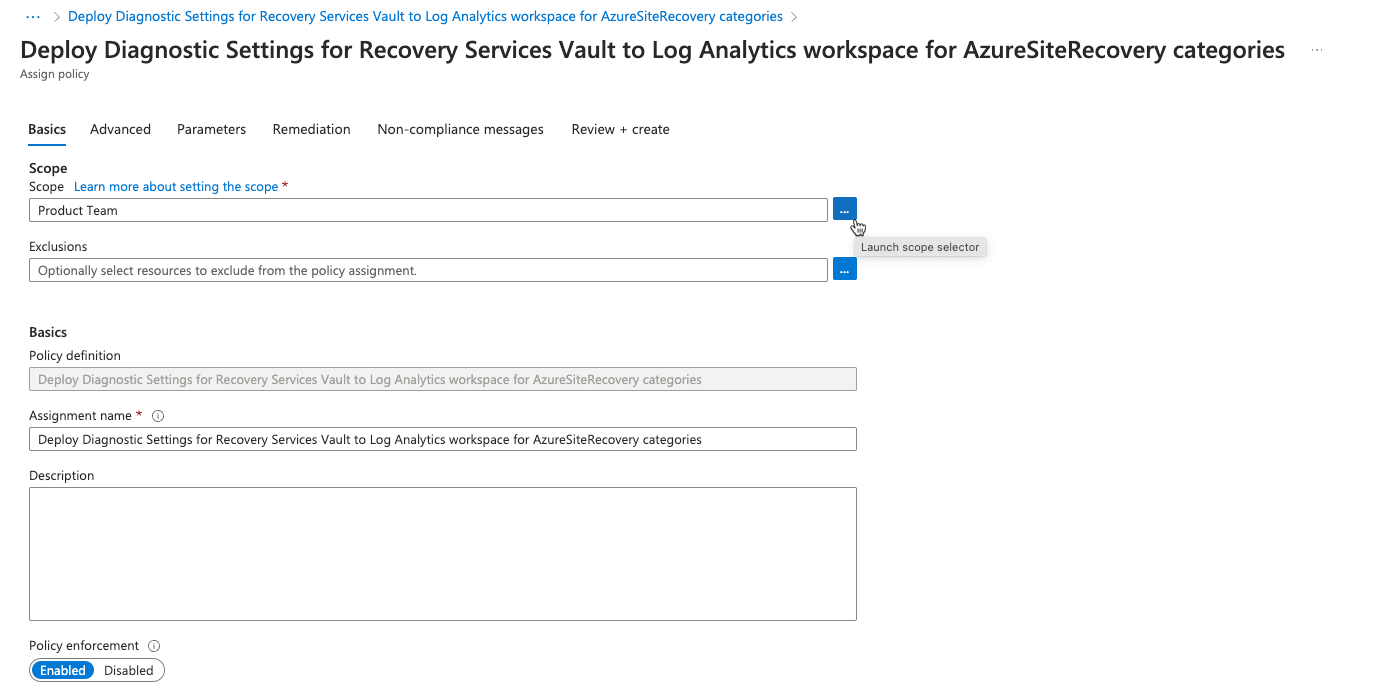
- Select a Subscription in the Scope window. Optionally, you can select a LogicMonitor resource group so that the policy is applied only to vaults in a particular resource group. Click Select.
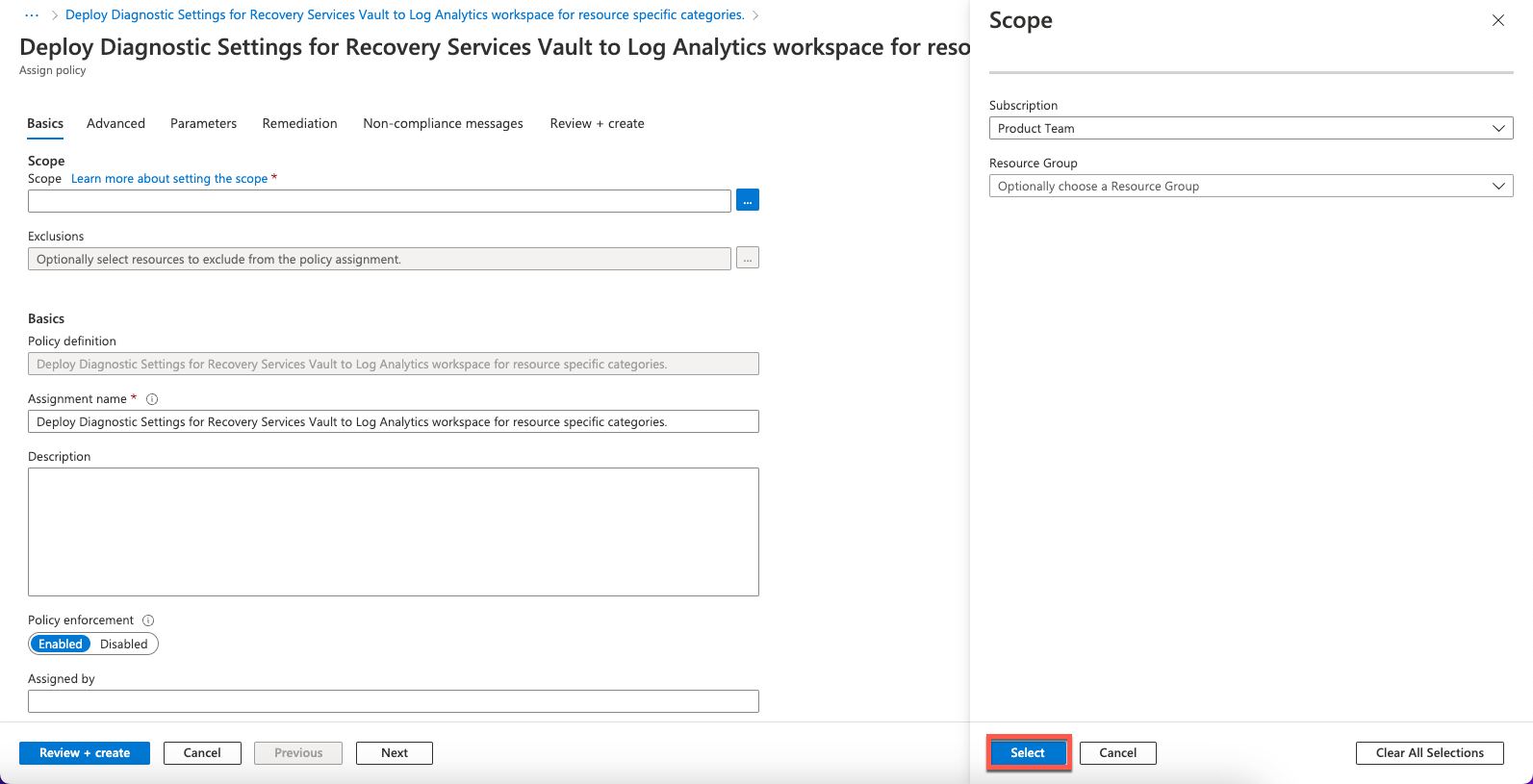
- Select the Parameters tab and disable Only show parameters that need input or review.
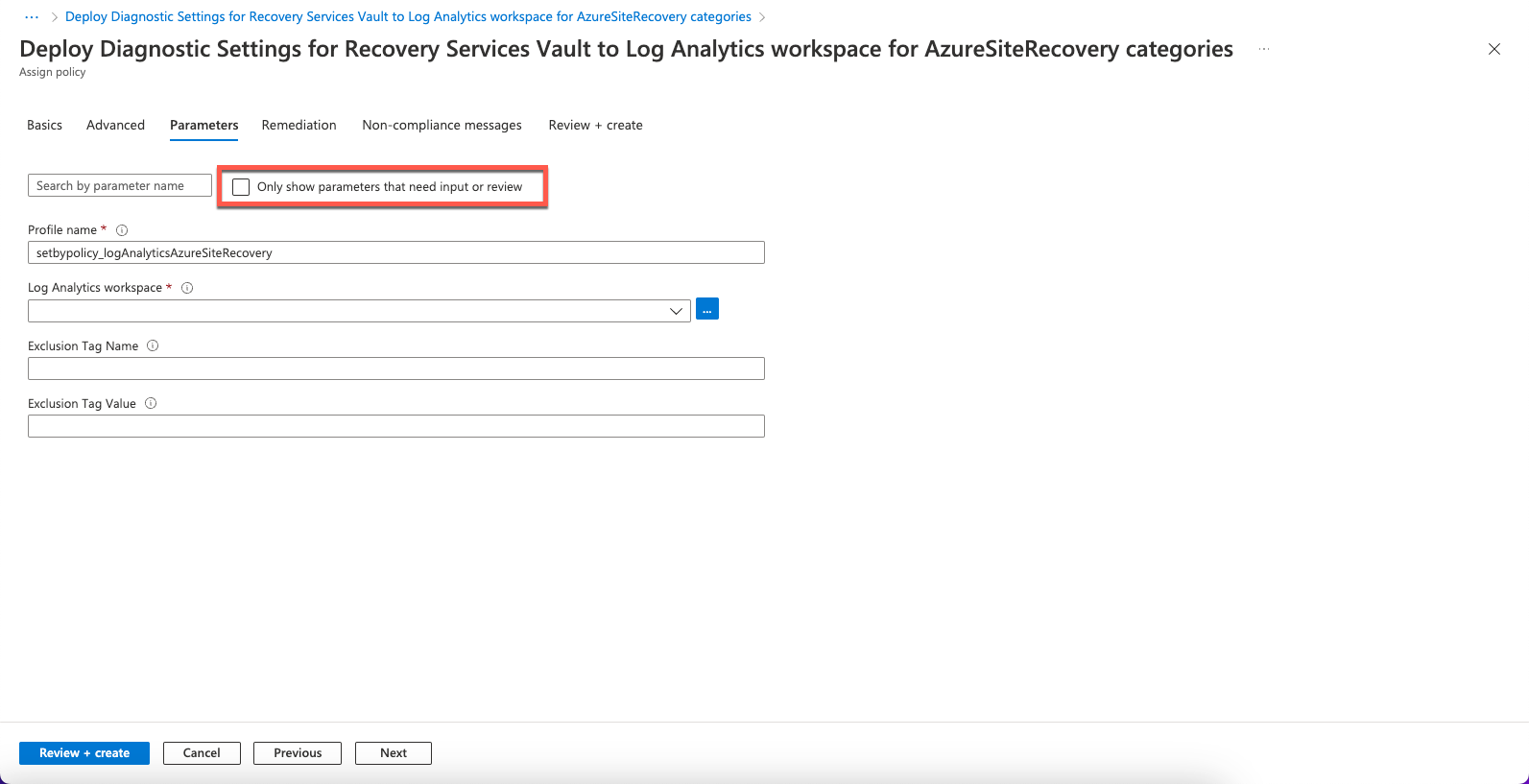
- Enter the following information:
- Profile Name— The name that will be assigned to the diagnostics settings created by the policy.
- Log Analytics workspace— The workspace to which the diagnostics setting will be associated. Diagnostics data of all vaults in the scope of the policy assignment will be pushed to the specified Log Analytics workspace.
- Exclusion Tag Name and Exclusion Tag Value— You can choose to exclude vaults containing a certain tag name and value from the policy assignment. For example, if you do not want a diagnostics setting to be added to those vaults that have a tag
isTestset to the valueyes, enter isTest in the Exclusion Tag Name field and yes in the Exclusion Tag Value field. If any (or both) of these two fields are left empty, the policy is applied to all relevant vaults regardless of the tags they contain.
- Click Next.
- Select the Remediation tab and enable Create a remediation task.
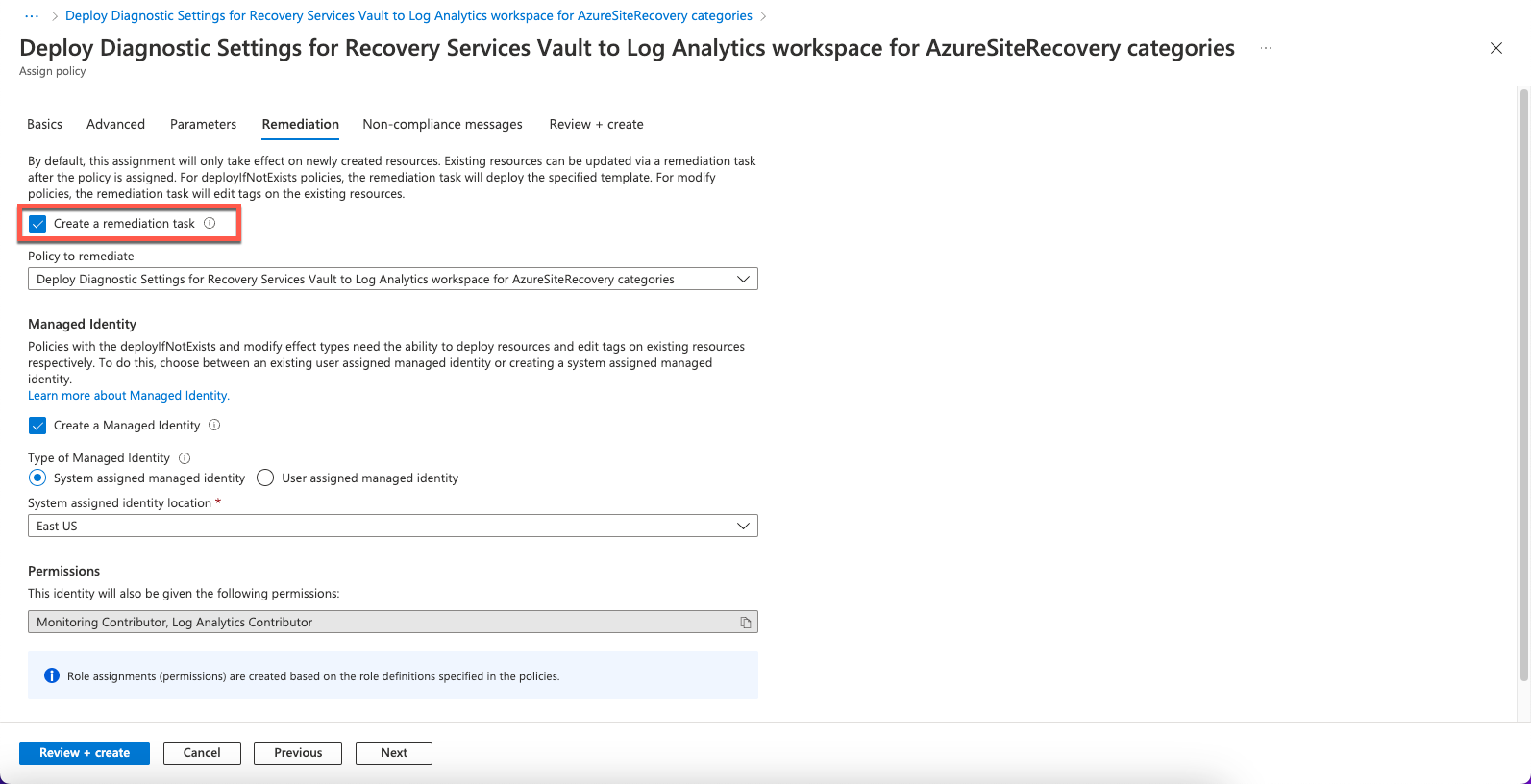
Note: Once the policy is assigned to a scope, any new vaults created in that scope get Log Analytics diagnostics settings configured automatically (within 30 minutes from the time of creation of the vault). To add a diagnostics setting to existing vaults in the scope, you can trigger a remediation task at policy assignment time. To trigger a remediation task, select Create a Remediation task.
- Select the Review+Create tab and click Create.
Note: LogicMonitor recommends using a policy-based configuration for forwarding site recovery events to Log Analytics. For manual configuration steps, see Configure Site Recovery to send logs.
Next Steps
You can view and validate your Diagnostic settings in Azure.
- In Azure, navigate to Recovery Services vaults.
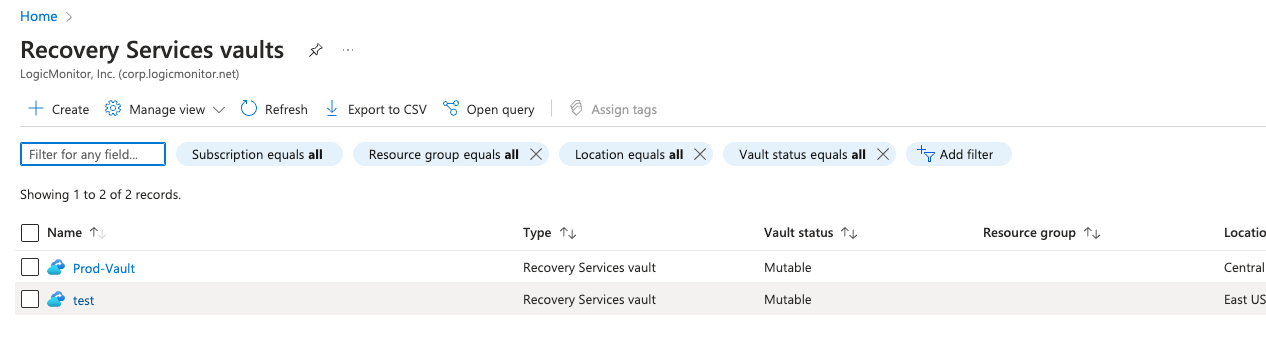
- Select the vault that you want to view and navigate to Monitoring > Diagnostic settings.
- Azure diagnostics
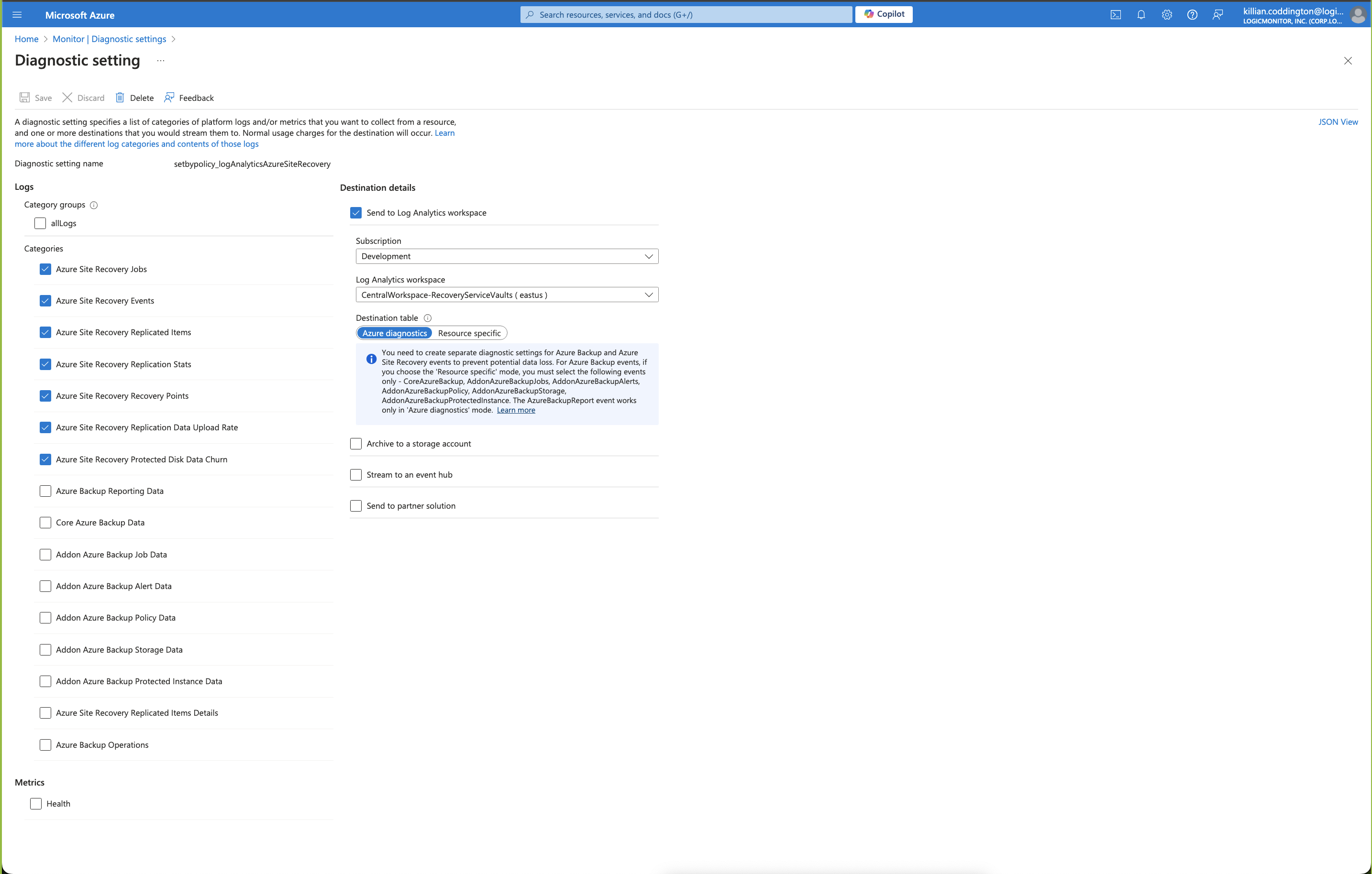
Ensure the Azure Site Recovery Replicated Items Details option is unchecked. However, the Azure Site Recovery option must remain selected. - Resource specific
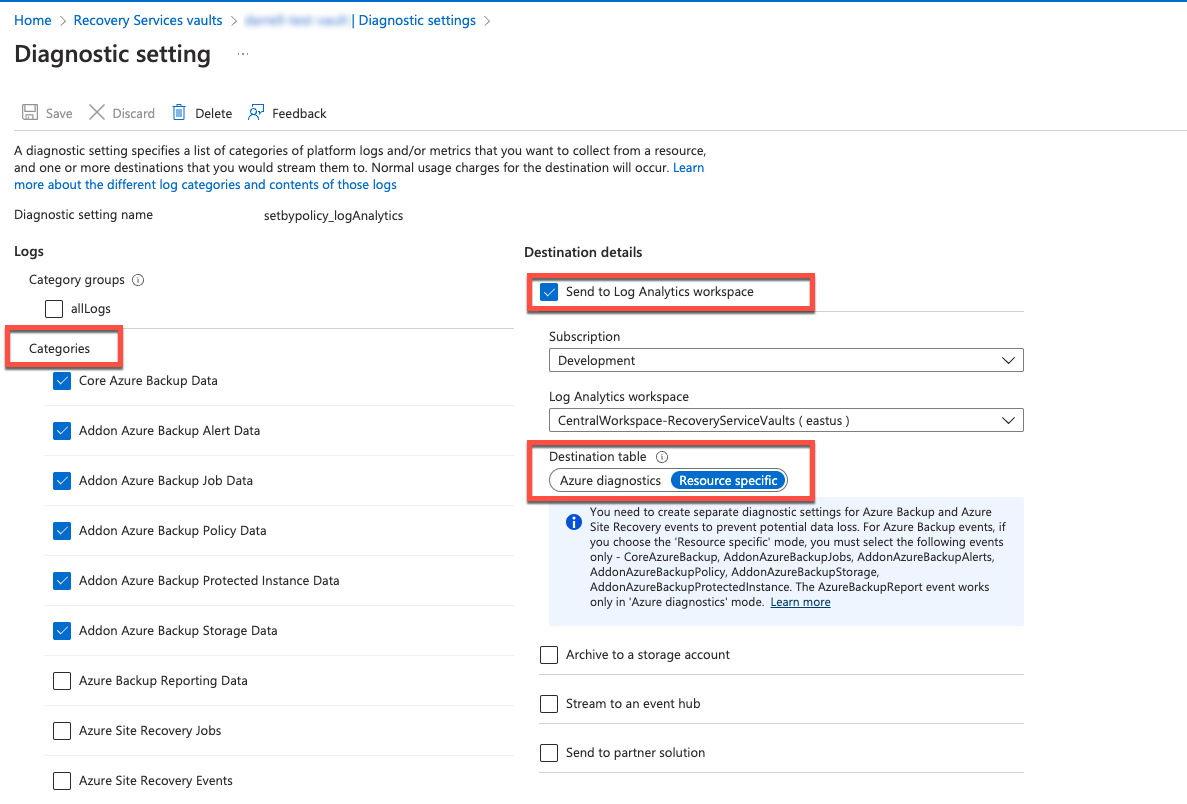
- Azure diagnostics
Note: Backup and recovery diagnostic settings cannot be combined in the same policy. For more information, see Diagnostic settings in Azure Monitor.


